Premium Only Content
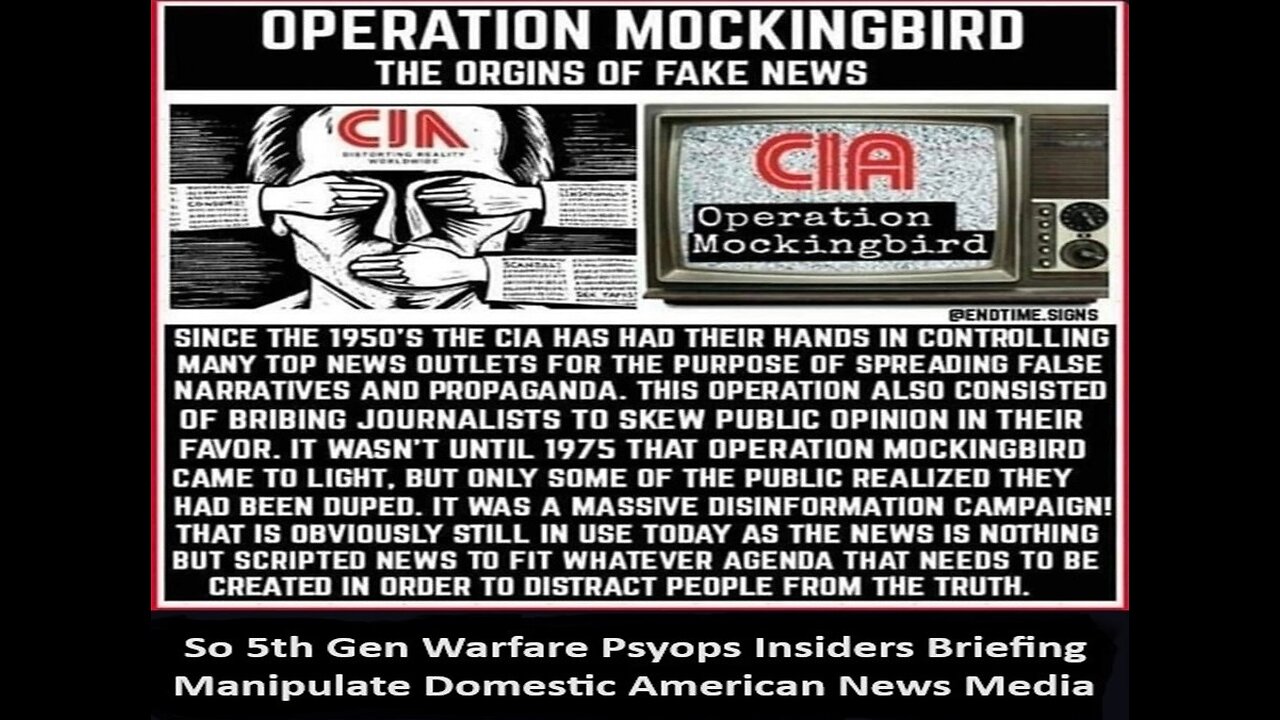
5th Gen Warfare Psyops Insiders Briefing Manipulate Domestic American News Media
Have You Ever Heard Of 5th Generation Warfare? Operation Mockingbird is an alleged large-scale program of the United States Central Intelligence Agency (CIA) that began in the early years of the Cold War and attempted to manipulate domestic American news media organizations for propaganda purposes.
An introduction to 5G-W
The nature of warfare has been changing, with the emergence of new tactics and strategies that go beyond traditional military engagements. The concept of 5th Generation Warfare has been increasingly used to describe these non-conventional methods that involve a range of tactics, including psychological operations, disinformation campaigns, and cyber-attacks. This article aims to provide a comprehensive overview of 5th Generation Warfare, its historical and current examples, and the challenges it poses for security and stability in the world.
It is important to note that this article does not take a political stance or endorse any particular ideology or nation. Instead, it is intended to be an educational resource that informs readers about the various tactics and strategies used in 5th Generation Warfare, and their potential impacts. By understanding the nature of 5th Generation Warfare and its evolving tactics, readers can gain a more nuanced and informed perspective on the contemporary geopolitical landscape.
Each chapter will provide readers with a detailed analysis of the topic, including historical examples, current events, and potential future implications. The article will also include strategies for countering 5th Generation Warfare and protecting against its effects.
Chapter I: 5th Generation warfare (5G-W)
In recent years, there has been growing interest in the concept of 5th Generation Warfare (5G-W). This term has been used to describe a new form of warfare that is characterised by the use of non-traditional tactics, such as information operations, cyber attacks, and psychological warfare, to achieve strategic objectives.
5G-W is a complex and multifaceted concept that is still evolving, with ongoing debates about its definition and scope. Some experts define 5G-W as a type of conflict that is waged by non-state actors, while others view it as a broader phenomenon that encompasses state-level strategies as well.
One of the defining features of 5G-W is its reliance on non-kinetic means of warfare, such as propaganda, disinformation, and social engineering. These tactics are used to influence the perceptions and behaviour of target populations, with the ultimate goal of achieving strategic objectives without resorting to traditional military force.
Another key characteristic of 5G-W is its emphasis on asymmetric tactics and strategies. This means that 5G-W actors often seek to exploit vulnerabilities and weaknesses in the opponent’s defence, rather than engaging in direct combat. This can make it difficult for traditional military forces to detect and respond to 5G-W threats effectively.
Despite its relatively recent emergence as a concept, 5G-W has already been identified as a major strategic challenge for modern militaries and governments. In order to understand and effectively counter 5G-W threats, it is important to have a clear understanding of its tactics, strategies, and objectives.
However, it is important to note that not all modern warfare falls under the definition of 5G-W. Traditional kinetic warfare, such as conventional ground and air combat, still plays a significant role in military operations. The distinction between traditional and 5th generation warfare is important to understand when analysing contemporary conflicts and developing effective strategies for defence and security.
Another aspect of 5G-W is the use of advanced technology to carry out non-kinetic attacks. For example, cyber attacks on critical infrastructure, including power grids and communication networks, can have a significant impact on a nation’s security and stability. Hackers and other malicious actors can exploit vulnerabilities in these systems, causing widespread disruption and chaos without ever firing a shot.
Additionally, the use of social media and other online platforms has become a key element of 5G-W. Actors can use these platforms to spread disinformation and propaganda, sow discord and division, and even influence public opinion and political outcomes.
One of the biggest challenges in countering 5G-W is the difficulty in identifying and attributing attacks. Because many of these tactics are carried out anonymously and remotely, it can be hard to determine who is behind them and how to respond effectively.
As 5G-W continues to evolve and grow in importance, it is likely that governments and militaries will need to adapt their strategies and tactics to effectively counter this new form of warfare. This may involve a greater emphasis on cyber-security, information operations, and other non-kinetic means of defence. It may also require a new approach to international relations and diplomacy, as nations seek to mitigate the risks of 5G-W while still pursuing their strategic objectives.
Despite the ongoing debates and controversies surrounding the concept of 5G-W, it is clear that this new form of warfare is becoming increasingly relevant in the modern world. As such, it is important for governments, militaries, and the general public to be aware of the potential risks and threats associated with 5G-W, as well as the strategies and tactics that can be used to counter these threats.
Chapter II: The Power of Language in 5G-W
The Impact of Language in Shaping Public Opinion
Language is a powerful tool that can be used to shape and influence public opinion. The words and phrases we use can have a profound impact on how people perceive and understand the world around them. From political speeches to advertising slogans, language is used to convey ideas, promote products, and sway opinions.
Throughout history, language has been used as a tool of manipulation and control. One of the most infamous examples of language manipulation is Nazi propaganda during the Holocaust. Adolf Hitler and his regime used language to dehumanise Jews and other groups, referring to them as vermin and parasites in order to justify their persecution and ultimately their genocide.
Historical language manipulation was used by governments during wartime to dehumanise the enemy, and the use of euphemisms to make unpleasant or controversial actions seem more palatable to the public.
Language manipulation is still prevalent in modern society, with political leaders and advertisers using language to sway public opinion. In political discourse, language is often used to demonise opponents and rally support for a particular agenda. Advertisers use language to make products seem more desirable and to create a sense of urgency to buy.
Below are a few examples of 5G-W language manipulation techniques:
Euphemisms and Framing: Politicians and interest groups often use euphemisms and framing techniques to shape public opinion. By choosing specific words or phrases, they can frame an issue or policy in a positive or negative light. For example, referring to budget cuts as “fiscal responsibility” or describing a controversial policy as “safeguarding individual welfare,” can influence how people perceive and react to the issue.
Loaded Language and Name-calling: In political debates and public discourse, loaded language and name-calling are used to demean opponents or de-legitimise their viewpoints. Labelling someone as a “radical,” “extremist,” “socialist,” or “fascist” is a way to evoke emotional reactions and discredit their ideas without engaging in substantive arguments. This tactic is employed by various sides of the political spectrum to polarise and rally their base.
It is essential to recognise that not everyone labelled as an “extremist” or “radical” truly espouses extreme beliefs. Loaded language can be employed to exaggerate or mis-characterise a person’s views, painting them with a broad brush based on limited information or intentional manipulation. This can be particularly problematic when it leads to unfair judgements and the marginalisation of individuals who may have nuanced perspectives.
Dog Whistling: Dog whistling refers to the use of coded language that appeals to a specific group while maintaining plausible deniability to the wider audience. Politicians may employ subtle cues, symbols, or phrases that resonate with a particular demographic without explicitly stating their intentions. This form of language manipulation can exploit existing prejudices or biases and provoke emotional responses among targeted groups.
Below are some examples of Dog Whistling:
Class Struggle: The concept of “class struggle”. On the surface, it may seem like a call for workers to unite against oppression and fight for their rights. However, it often served as a dog whistle to incite hatred towards the bourgeoisie and promote the idea of a revolution to overthrow the existing social order.
Equality and Social Justice: While these concepts can have positive connotations, they were historically used as dog whistles. Behind these seemingly benign ideas, leaders sought to consolidate power, suppress dissent, and impose a collectivist society that often resulted in authoritarian rule.
Worker Solidarity: The idea of worker solidarity was also historically another common dog whistle used. While it may seem like a call for unity and empowerment of the working class, it was often used to promote an ideology, control labour movements, and suppress dissenting voices. By appealing to the struggles and aspirations of workers, governments could manipulate public sentiment and gain support for their revolutionary goals.
Misinformation and Disinformation: The intentional spread of misinformation and disinformation through various channels, including social media, is a significant example of language manipulation. False or misleading information is crafted and disseminated to deceive the public, shape narratives, and influence political discourse. This manipulation tactic aims to sow confusion and create division.
Spin and PR Techniques: Public relations (PR) professionals and political “spin doctors” employ language manipulation techniques to shape public perception of individuals, organisations, or events. Through carefully crafted press releases, media appearances, and messaging strategies, they aim to control the narrative, downplay negative information, and emphasise positive aspects to shape public opinion in a favourable direction.
Framing Opposition, eg. “Anti-(Insert Value)”: Another common tactic in language manipulation is framing opposition against specific values. By labelling “dissenters” as “un-this” or “anti-that,” proponents seek to marginalise opposing viewpoints and discourage critical engagement. This tactic aims to create an “us vs them” mentality and suppress alternative perspectives.
These examples illustrate the pervasive nature of language manipulation in contemporary discourse. It’s crucial to critically analyse and question the language used in various contexts to understand the underlying intentions and biases behind the messaging.
However, language can also be used to inspire positive change and promote empathy and understanding. By using language that is inclusive and respectful, we can create a more tolerant and compassionate society.
Are you still with me? … This is just heating up …
Stay awake and read on :)
Chapter III: Ideological Subversion and AI
Ideological subversion is a method of undermining the existing system of government or social structure by infiltrating and manipulating key institutions, such as the media, education, and government. This method involves slowly changing the beliefs and values of the population over time, often through the use of propaganda and other forms of information warfare.
Yuri Bezmenov, a former KGB agent, outlined a theory of ideological subversion in a series of interviews in the 1980s. He described a four-stage process that he claimed was used by the Soviet Union to undermine and destabilise targeted societies. These stages are:
Demoralisation: According to Bezmenov, demoralisation is the first stage of ideological subversion, which involves the gradual erosion of societal values, norms, and moral foundations. The goal is to weaken the belief system of the targeted society and make it more susceptible to ideological manipulation. This stage can take years or even decades to achieve and is primarily achieved through propaganda, infiltration of educational institutions, and the promotion of moral relativism and cultural decay.
Destabilisation: The destabilisation stage aims to create a sense of crisis and unrest within the targeted society. Bezmenov argued that this is done by promoting social and economic turmoil, exacerbating existing divisions, and undermining the functioning of institutions. The goal is to foster a state of chaos and make the population more receptive to radical change and alternative ideologies.
Crisis: During the crisis stage, the targeted society experiences a period of intense turmoil, marked by political, social, and economic upheaval. Bezmenov suggested that the crisis is intentionally provoked or exploited to further destabilise the society and create a power vacuum. This stage often involves mass protests, violence, and a breakdown of law and order.
*Normalisation: The final stage of ideological subversion is normalisation, where a new ideological framework is imposed to establish control over the destabilised society. Bezmenov argued that this involves the installation of a puppet regime or a new political system that aligns with the interests of the subverter. The new system is presented as a solution to the crisis, offering stability and promising a better future. The population may be subjected to censorship, repression, and restrictions on freedoms under the guise of maintaining order and protecting the “revolutionary” gains.
In a future article we will explore the relationships of the following terms:
*Normalisation, new normal and new world order.
It’s important to note that while Bezmenov’s theory has gained some attention, it is also a subject of criticism and controversy. Some argue that his perspective may be overly simplistic and rooted in Cold War-era rhetoric. Nonetheless, understanding and critically evaluating the stages Bezmenov described can contribute to a broader analysis of ideological manipulation and societal influence.
Watch the video for more context on Ideological subversion
One of the most well-known examples of ideological subversion was the Soviet Union’s efforts to undermine Western democracies during the Cold War. The KGB, the Soviet intelligence agency, infiltrated and manipulated various institutions in the West, such as academia, the media, and political organisations, to spread Soviet propaganda and influence public opinion.
Another example is the Chinese Communist Party’s current efforts to spread its influence and ideology beyond its borders through initiatives like the Belt and Road Initiative and Confucius Institutes.
Lets now look at ideological subversion and technology in the modern era …
Well, here is where it get’s interesting :)
I had a conversation with AI about it … see a snippet of that chat below …
Me — “Is ideological subversion a conspiracy theory or a real phenomenon?”
ChatGPT — “Ideological subversion is a real phenomenon that has been studied and documented by various experts in the fields of psychology, sociology, and political science. It refers to the systematic efforts to manipulate and influence people’s beliefs, values, and worldview in order to achieve political or social goals. While the term “ideological subversion” may sometimes be used in a conspiratorial or exaggerated manner, the underlying concept and the potential dangers associated with it are widely recognised and studied in academic and professional settings”
Me — “Could AI be ideologically subverted?”
ChatGPT — “As an AI language model, I do not have personal beliefs or biases. However, it is possible that the data I am trained on, or the algorithms used to train me, may contain biases or ideological subversion. It is important for humans to continue to monitor and critically analyse information, including information provided by AI systems, to ensure accuracy and avoid ideological subversion”
Me — “I get labelled as a conspiracy theorist for calling out ideological subversion, is that fair?”
ChatGPT — ” It is not fair to label someone as a conspiracy theorist simply for expressing concerns about ideological subversion. However, it is important to distinguish between legitimate concerns about biased or inaccurate information and unfounded, baseless claims that are not supported by evidence. It is possible for some individuals to use accusations of ideological subversion as a way to discredit information or viewpoints they disagree with, without providing any evidence to support their claims. Therefore, it is important to approach these issues with critical thinking and careful analysis of the available evidence”
Me — “What are the ramifications of ideological subversion through a technocratic system that implements AI to do its bidding?”
ChatGPT — ” Ideological subversion through a technocratic system that implements AI could have significant ramifications. If the data and algorithms used to train the AI are ideologically subverted, the AI’s output could be biased and unreliable, leading to incorrect or harmful decisions being made. This could have serious consequences, particularly in areas such as healthcare, finance, and law enforcement. Furthermore, if the technocratic system is controlled by those with ideological biases, the AI could be used as a tool to perpetuate and amplify those biases, potentially leading to further polarisation and division in society. It’s important to ensure that AI is developed and deployed in an ethical and transparent manner, with rigorous testing and validation to ensure that it is not being used to promote ideological subversion or any other form of bias or discrimination”
Me — “Final question, What if the flow of information has been ideologically subverted through a technocracy or oligarchy? involving the political system, education system, media, flow of information and all peer review organisations?”
ChatGPT — “If the flow of information has been ideologically subverted through a technocracy or oligarchy, it can have significant ramifications on society. This is because information plays a crucial role in shaping people’s beliefs, values, and behaviours. If the information that people receive is ideologically subverted, it can lead to a distorted view of the world, which can have serious consequences.
For example, if people are fed false or misleading information, it can lead to a lack of action on this critical issue. Similarly, if people are exposed to ideologically subverted information about a political candidate, it can influence their voting behaviour, leading to the election of an unfit leader.
Furthermore, if the flow of information is ideologically subverted, it can lead to the suppression of alternative viewpoints and the marginalisation of dissenting voices. This can lead to a chilling effect on free speech and open debate, which is crucial for a healthy democracy.
In the context of AI, if the data used to train AI models is ideologically subverted, it can lead to biased and discriminatory algorithms. This can have serious consequences in areas such as healthcare, criminal justice, and hiring practices, where AI is increasingly being used to make important decisions.
Overall, the ramifications of ideological subversion through a technocratic system that implements AI to do its bidding can be far-reaching and profound, affecting nearly every aspect of society”.
It is important to be aware of the methods and tactics used in ideological subversion, in order to safeguard against attempts to undermine the existing system of government or social structure …
I will reserve a separate article to delve into the diverse range of ideologies that have shaped human history. Stay tuned for an upcoming piece that will shed light on the complexities of different ideologies and their role in shaping societies.”
Such as:
Democracy, Capitalism, Socialism, Liberalism, Conservatism, Fascism, Communism, Nationalism, Anarchism and much more …
Yet, we must now move on to our next 5G-W chapter :)
Chapter IV: Cultural Hegemony and Disinformation
What is hegemony?
Hegemony refers to the domination or leadership of one social group or nation over others, usually achieved through the use of power, persuasion, or cultural influence. The term was originally coined by the Italian Marxist theorist Antonio Gramsci to describe the ways in which ruling elites maintain their power and control over society through the use of ideology, culture, and institutions. In the context of cultural hegemony, the dominant group uses its cultural and ideological influence to shape the beliefs, values, and norms of society in ways that perpetuate its power and privilege. This can include the dissemination of propaganda and disinformation, the co-optation of oppositional movements or ideas, and the promotion of a particular worldview or way of life as natural or inevitable.
Cultural Hegemony and Disinformation are important concepts in understanding 5th generation warfare. Cultural hegemony refers to the domination of a particular culture over others, while disinformation refers to the deliberate spread of false information to mislead and manipulate people. In this chapter, we will explore historical and current examples of cultural hegemony and disinformation.
Throughout history, powerful empires have used cultural hegemony and disinformation to maintain their dominance over other cultures. The British Empire, for example, used cultural hegemony to spread their language, religion, and customs to the colonies they controlled. The empire also used disinformation to mislead the local population, such as spreading rumours about rebellious leaders to weaken their support.
Similarly, during the Cold War, the United States and the Soviet Union engaged in a cultural battle to spread their ideologies and values to other countries. This was known as the cultural Cold War, and both sides used propaganda and disinformation to shape public opinion and influence political decisions.
In the modern era, cultural hegemony and disinformation are still prevalent. One example is the dominance of American culture in the global entertainment industry. American movies, TV shows, and music are popular worldwide, leading to concerns about the homogenisation of culture.
Another example is the use of disinformation in political campaigns and international relations. Russia, for instance, has been accused of using disinformation campaigns to influence elections in other countries and to sow discord among their populations.
Overall, cultural hegemony and disinformation are important tools in 5th generation warfare, and it is essential to recognise their use in modern conflicts.
Yes … This leads on to the whole communism vs capitalism debate … we will explore this in a later article … for now lets try to keep on track … we are talking about 5G-W :)
Chapter V: Social Engineering
Definition of Social Engineering
Social engineering is the practice of using psychological manipulation and deception to influence or control individuals or groups of people, usually for personal gain or political purposes. It involves the use of various tactics to gain trust, build relationships, and ultimately influence or control people’s thoughts, beliefs, and behaviours.
Social engineering can involve psychological operations (PSYOPs) as a means of achieving its goals, but it can also involve other tactics and techniques, such as manipulation of social norms, use of propaganda, and manipulation of information.
While there can be some overlap between social engineering and PSYOPs, social engineering is generally considered to be a broader category of influence operations that encompasses a range of tactics beyond just psychological manipulation.
Such as:
Phishing scams: This is a type of social engineering where attackers trick individuals into divulging sensitive information such as passwords or bank account details through fake emails or websites.
Advertising: Advertisers use social engineering techniques to influence people’s behaviour and buying decisions by creating emotional connections and manipulating people’s desires.
Political campaigns: Political campaigns use social engineering to manipulate public opinion and influence voting behaviour by using targeted messaging, propaganda, and emotional appeals.
Product design: Product designers use social engineering techniques to create products that are more appealing and engaging to users, such as addictive mobile games or social media platforms that keep users hooked.
Education: Educators use social engineering to shape students’ beliefs, attitudes, and behaviours through curriculum design, classroom activities, and messaging.
These are just a few examples, but social engineering can be applied in many different contexts and industries.
One of the earliest examples of social engineering is the Trojan Horse, a story from Greek mythology where the Greeks used deception to gain access to the city of Troy. In the 20th century, governments and corporations have used social engineering tactics for various purposes. One example is the propaganda campaigns of Nazi Germany, which used social engineering to promote their ideology and create a sense of national unity. Another example is the use of advertising to manipulate consumer behaviour and create brand loyalty.
In the modern era, social engineering has become increasingly prevalent, especially in the digital world. Cyber-criminals use social engineering tactics such as phishing and pre-texting to trick people into revealing sensitive information or performing actions that can compromise their security. Social media platforms and search engines also use social engineering to influence user behaviour and collect personal data for advertising purposes. Additionally, political campaigns and organisations use social engineering to influence public opinion and promote their agenda.
Overall, social engineering is a powerful tool that can be used for both positive and negative purposes. It is important to be aware of these tactics and take steps to protect oneself from manipulation and deception.
Chapter VI: Propaganda in the Digital Age
Definition of Propaganda in the Digital Age
In the digital age, propaganda can be defined as the systematic dissemination of information, ideas, or narratives, often with a biased or misleading nature, to influence public opinion and shape beliefs and behaviours. Propaganda in the digital age takes advantage of the rapid spread of information through online platforms, social media, and other digital channels. It is often used by individuals, organisations, or governments to manipulate perceptions, advance agendas, and gain a strategic advantage.
Here are some key characteristics of propaganda in the digital age:
Mass Dissemination: Digital platforms enable the widespread distribution of propaganda to reach a large audience quickly. Social media, websites, blogs, and online forums serve as vehicles for propagandists to spread their messages to targeted individuals or broad segments of the population.
Targeted Messaging: Digital technologies allow for precise targeting of propaganda messages based on demographic, geographic, or behavioural data. This enables propagandists to tailor their content to specific audiences, increasing the likelihood of resonance and impact.
Amplification through Viral Spread: The viral nature of digital content can amplify the reach of propaganda. When individuals share, like, or comment on propaganda content, it can quickly spread across networks, influencing a broader range of individuals and potentially reinforcing biases or beliefs.
Blurring of Information Sources (muddied waters): The abundance of information sources online, combined with the rise of user-generated content, can create a confusing landscape where it becomes challenging to discern reliable information from propaganda. Propagandists often exploit this ambiguity to blur the lines between fact and fiction, making it more challenging for individuals to critically evaluate information.
Psychological Manipulation: Propaganda in the digital age often employs various psychological tactics to influence perceptions and behaviours. These tactics may include appealing to emotions, exploiting cognitive biases, using persuasive techniques, and employing micro-targeting strategies to tailor messages to individual psychological profiles.
You may have heard of “gaslighting”, it is a form of psychological manipulation …
Gas-lighting: typically involves a pattern of behaviour aimed at making the victim question their own perceptions, experiences, and even their sense of self. The gaslighter may engage in tactics such as lying, contradicting the victim’s memories or experiences, withholding information, trivialising their feelings, and creating a sense of confusion or self-doubt
Gaslighting often occurs within personal relationships, but it can also be employed in other contexts, such as workplaces or political settings, to manipulate and exert influence over individuals or groups. It exploits psychological vulnerabilities and relies on the power dynamics between the gaslighter and the victim.
Echo Chambers and Polarisation: Digital platforms can contribute to the formation of echo chambers, where individuals are exposed mainly to information that reinforces their existing beliefs and ideologies. This reinforcement can deepen divisions, polarise societies, and make individuals more susceptible to propaganda that aligns with their preconceived notions.
Algorithmic Manipulation: Algorithms used by digital platforms can shape the information users are exposed to, potentially amplifying propaganda content based on user preferences and engagement patterns. This algorithmic manipulation can create filter bubbles, limiting exposure to diverse perspectives and fostering the spread of confirmation bias.
Additional context … Cognitive Dissonance: Cognitive dissonance, the psychological discomfort that arises from conflicting beliefs or information, is relevant when discussing propaganda in the digital age. When individuals encounter information that contradicts their existing beliefs or opinions, they may experience cognitive dissonance. This discomfort can lead individuals to reject or rationalise the new information, or modify their beliefs to reduce the dissonance. Propagandists can exploit cognitive dissonance by strategically crafting messages that align with existing beliefs, making it more difficult for individuals to critically evaluate and challenge their own beliefs. Additionally, cognitive dissonance can contribute to the formation of echo chambers and filter bubbles, as individuals seek out information that confirms their existing beliefs, further reinforcing cognitive biases.
Historical examples of Propaganda in the Digital Age
World War II: Propaganda played a significant role during World War II, with both the Allied and Axis powers employing various propaganda techniques. Governments produced posters, films, and radio broadcasts to shape public opinion, boost morale, demonise the enemy, and encourage support for the war effort.
Cold War: The Cold War era witnessed intense propaganda campaigns by both the United States and the Soviet Union. Each side used various mediums, such as newspapers, radio broadcasts, and television, to portray the other as a threat and promote their own political and ideological systems.
Nazi Germany: The Nazi regime under Adolf Hitler employed extensive propaganda to control public opinion and advance its agenda. Joseph Goebbels, the Minister of Propaganda, utilised techniques like censorship, rallies, and the dissemination of anti-Semitic materials to manipulate public sentiment and maintain the support of the German population.
Soviet Union: The Soviet Union under Joseph Stalin used propaganda to promote Communist ideology and create a cult of personality around Stalin himself. Propaganda posters, films, and literature portrayed Stalin as a strong leader and propagated the idea of a socialist utopia.
These historical examples demonstrate how propaganda has been used throughout different periods to shape public opinion, manipulate perceptions, and advance political or ideological objectives.
Current Examples of Propaganda in the Digital Age
Digital propaganda is still very much present in today’s world, with governments and organisations using it to spread their message or influence public opinion. One example is the Chinese government’s use of digital propaganda to shape the narrative around its actions in Xinjiang and Hong Kong, with state-controlled media outlets spreading misinformation and propaganda. Similarly, during the COVID-19 pandemic, there has been an abundance of disinformation and propaganda surrounding the virus and its origins, with various governments and interest groups pushing their own narratives.
Lets see a few current examples :)
State-sponsored propaganda: Various countries have been accused of using digital platforms to disseminate propaganda in order to influence public opinion both domestically and internationally. State-sponsored propaganda can include the spread of misinformation, the manipulation of news narratives, and the creation of online troll armies to target specific individuals or groups.
Election interference: Instances of propaganda campaigns aimed at influencing elections have been a significant concern in the digital age. Foreign actors or domestic groups may engage in spreading false information or using targeted messaging to sway public opinion, discredit political opponents, or undermine confidence in the electoral process.
Extremist recruitment and radicalisation: Online platforms have been utilised by extremist groups to recruit individuals and spread propaganda to further their ideologies. These groups may use social media, online forums, and encrypted messaging apps to disseminate their messages, target vulnerable individuals, and radicalise them towards violent or extremist beliefs.
Disinformation and deepfakes: The spread of disinformation, including fabricated news stories, doctored images, and manipulated videos, has become a prominent issue in the digital age. Deepfake technology, which allows for the creation of highly realistic fake videos or audio recordings, has the potential to further amplify the impact of disinformation campaigns.
These are just a few general examples, and it’s important to recognise that propaganda in the digital age is constantly evolving and may take on new forms. Critical thinking, media literacy, and verification of information from reliable sources are essential in navigating the digital landscape and identifying instances of propaganda.
While the digital age has made propaganda more widespread and accessible, it has also made it easier to detect and counteract. However, the fight against propaganda in the digital age is an ongoing battle that requires constant vigilance, awareness and understanding.
Chapter VII: Information Warfare
Information warfare refers to the use of information and communication technologies (ICTs) to influence or disrupt the decision-making of an adversary. This can include a range of tactics such as spreading false information, manipulating social media, and conducting cyber-attacks.
Information warfare, or the use of information and communication technologies to gain a strategic advantage, has a long history. Here are some historical examples of information warfare:
Operation Mincemeat (World War II): During World War II, the British launched Operation Mincemeat, a successful deception campaign. The British planted false information on a corpse, dressed as a British officer, and allowed it to wash ashore in Spain. The information suggested that the Allied forces would attack Greece instead of their actual target, Sicily. The Germans fell for the ruse and diverted their resources, giving the Allies a strategic advantage in the Sicily campaign.
Operation Fortitude (World War II): Another significant deception campaign during World War II was Operation Fortitude, which aimed to deceive the Germans about the location of the D-Day landings. The Allies used a combination of fake radio transmissions, dummy equipment, and double agents to convince the Germans that the main invasion would occur at Pas-de-Calais instead of Normandy. This misinformation misled the Germans and allowed the Allies to launch a successful surprise attack.
Stuxnet (2010): Stuxnet is a computer worm that is considered one of the most sophisticated cyber-weapons ever deployed. It was jointly developed by the United States and Israel and specifically designed to target Iran’s nuclear program. Stuxnet infected the computer systems controlling Iran’s uranium enrichment centrifuges, causing physical damage to the equipment. The attack was covert and aimed at disrupting Iran’s nuclear capabilities while maintaining plausible deniability.
These historical examples highlight the various forms and techniques of information warfare throughout history, demonstrating the use of deception, manipulation, and cyber tactics to gain strategic advantages or achieve specific objectives.
Current Examples of Information Warfare
In recent years, there have been numerous examples of information warfare in the international arena. One notable example is the use of disinformation campaigns to sway public opinion on issues such as Taiwan and Hong Kong, as well as North Korea’s use of cyber-attacks to disrupt critical infrastructure and steal sensitive information.
In addition, there is growing concern about the use of deepfakes, which are videos or audio recordings that have been manipulated to make it appear as though someone said or did something that they did not. Deepfakes have the potential to be used in information warfare to spread false information and manipulate public opinion on a large scale.
Overall, information warfare is a growing concern in the modern world, as technology continues to advance and the internet becomes an increasingly important part of our lives. It is important for individuals and governments to be aware of these tactics and to take steps to defend against them.
Political warfare and information warfare are related but distinct concepts. Political warfare refers to the use of political means to achieve strategic objectives, such as influencing or controlling a population, government, or territory. It includes tactics such as propaganda, disinformation, and psychological operations.
On the other hand, information warfare is a type of warfare that involves the use of information and communication technologies to achieve strategic objectives. It includes tactics such as hacking, cyber-attacks, and disinformation campaigns.
While political warfare can include the use of information operations, information warfare typically focuses more specifically on the use of information technology to achieve objectives. Both political warfare and information warfare can be used in conjunction with each other, as the manipulation of information and public opinion is often a key aspect of political warfare.
Chapter VIII: Cyber Warfare
Cyber warfare is the use of digital attacks and defensive measures to disrupt or destroy an enemy’s information systems and networks. Cyber warfare can take various forms, including espionage, sabotage, and propaganda. In recent years, cyber warfare has become an increasingly important tool in military and political conflicts, with countries and non-state actors using sophisticated cyber attacks to achieve strategic objectives.
One of the earliest known examples of cyber warfare occurred in 2007 when the Russian government launched a cyber attack on Estonia. The attack was launched in response to Estonia’s decision to move a Soviet-era war memorial from central Tallinn. The cyber attack targeted Estonia’s government, banks, media outlets, and other critical infrastructure, causing widespread disruption and chaos.
Another significant example of cyber warfare is the NotPetya ransomware attack that occurred in 2017. NotPetya is widely regarded as one of the most destructive cyber attacks in history, targeting organisations primarily in Ukraine but causing collateral damage worldwide. The malware disguised itself as a software update, infecting computer systems and spreading rapidly. It disrupted critical infrastructure, including government networks, power grids, and transportation systems. NotPetya demonstrated the potential for cyber attacks to have far-reaching consequences, impacting not only individual targets but also causing significant economic disruptions on a global scale. This incident underscored the importance of robust cyber-security measures and the need for international cooperation in combating cyber threats.
Cyber warfare continues to be a growing concern in today’s interconnected world. In recent years, countries such as China, Russia, and North Korea have been accused of launching cyber attacks against their adversaries. These attacks have targeted everything from government agencies to corporations and critical infrastructure.
In 2021, the United States government accused China of a cyber attack on Microsoft’s Exchange Server, which affected tens of thousands of organisations around the world. The attack was believed to have been carried out by a group known as Hafnium, which has links to the Chinese government.
Another current example of cyber warfare is the ongoing conflict between Israel and Iran. In recent years, there have been several cyber attacks on Iranian nuclear facilities, with Israel believed to be behind many of them. In response, Iran has launched cyber attacks against Israeli targets, including government agencies and private companies.
Cyber warfare is a growing threat in today’s digital age. As technology continues to evolve, so do the tactics and techniques used in cyber attacks. Countries and non-state actors will continue to use cyber warfare to achieve their strategic objectives, making it essential for governments and organisations to prioritise cyber-security and develop effective defensive measures.
Chapter IX: Economic Warfare
Economic warfare is a type of warfare that aims to use economic means to achieve strategic objectives. It involves using economic tools such as sanctions, embargoes, tariffs, and trade barriers to weaken an adversary’s economy and limit their ability to pursue their strategic goals.
Throughout history, economic warfare has been used as a tool of statecraft to achieve strategic objectives. Some examples of historical economic warfare include:
The British blockade of Germany during World War I, which aimed to prevent Germany from accessing essential goods and materials needed for the war effort.
The U.S embargo on Japan prior to World War II, which aimed to limit Japan’s access to oil and other critical resources.
The U.S -led sanctions on South Africa during the apartheid era, which aimed to pressure the South African government to end apartheid policies.
Today, economic warfare continues to be used by states to achieve strategic objectives.
Some current examples of economic warfare include:
The U.S sanctions on Iran, which aim to limit Iran’s ability to finance its nuclear program and support for regional allies.
The ongoing trade war between the U.S and China, which involves the use of tariffs and trade barriers to pressure China to change its economic policies.
The EU sanctions on Russia following its annexation of Crimea, which aim to limit Russia’s access to Western markets and technologies.
Economic warfare can have far-reaching consequences for both the targeted state and the global economy. As such, it is a powerful tool that must be used judiciously and in accordance with international law.
Chapter X: Hybrid Warfare
Hybrid warfare refers to the use of a combination of conventional and unconventional methods of warfare by a state or non-state actor to achieve its objectives.
This chapter will examine the concept of hybrid warfare and its historical and current examples.
Throughout history, hybrid warfare has been used by various states and non-state actors. One prominent example is the Vietnam War, where the North Vietnamese forces used a combination of guerrilla tactics, propaganda, and conventional military force to resist the United States and its allies. Another example is the Soviet Union’s invasion of Afghanistan, where they used a combination of conventional military force and support for local insurgent groups to maintain control over the country.
In recent years, hybrid warfare has become an increasingly prominent feature of global conflict. One example is Russia’s actions in Ukraine, where they used a combination of military force, information warfare, and support for local separatist groups to destabilise the country and annex Crimea. Another example is Iran’s use of proxies in Iraq and Syria, where they have used a combination of conventional military force and support for local militias to advance their strategic interests.
Hybrid warfare has become a major challenge for the international community, as it blurs the lines between war and peace and makes it difficult to respond effectively to aggression. It requires a comprehensive approach that involves not only military force but also political, economic, and informational tools to counter the various elements of hybrid warfare.
Chapter XI: The Grey Zone
The grey zone is a term used to describe a state of conflict between nations or other actors in which the lines between war and peace are blurred. In the grey zone, actors engage in activities that are not quite war but are also not quite peace. These activities may include cyber attacks, propaganda, economic pressure, and other tactics that seek to undermine an opponent without engaging in direct military conflict.
Historical examples of the grey zone include the Cold War between the United States and the Soviet Union, where both sides engaged in espionage, proxy wars, and other activities that were not technically considered war. Other examples include the conflicts in Ukraine and Syria, where Russian forces have used hybrid warfare tactics, including propaganda, cyber attacks, and support for separatist groups, to destabilise these countries without engaging in direct military conflict.
The ongoing conflict between Israel and Palestine is also an example of the grey zone, with both sides using tactics such as terrorism, propaganda, and economic pressure to achieve their objectives.
The grey zone poses a significant challenge to traditional approaches to conflict resolution and diplomacy, as it is often difficult to clearly define the boundaries of the conflict and identify appropriate responses. As such, understanding the grey zone and developing effective strategies to counter its tactics is essential for maintaining international security and stability.
Chapter XII: Political Warfare
Political warfare is a set of techniques and methods used by governments and other organisations to achieve their objectives. It involves a combination of military and non-military means to influence the behaviour of an opponent and achieve a desired outcome. Political warfare can include the use of propaganda, covert action, economic pressure, and other forms of persuasion.
Throughout history, political warfare has been used by nations and groups to gain advantages over their opponents.
Some historical examples of political warfare include:
The propaganda campaigns of World War I and II: Both sides in these wars used propaganda to sway public opinion and win support for their cause.
The Cold War: The United States and the Soviet Union engaged in political warfare throughout the Cold War, using covert operations, propaganda, and economic pressure to gain advantages over each other.
The Iranian Revolution: In 1979, a revolution in Iran overthrew the country’s government and installed an Islamic regime. The new government used political warfare to consolidate power and gain support from the Iranian people.
Today, political warfare continues to be used by governments and other organisations to achieve their objectives. Some current examples of political warfare include:
Disinformation Campaigns: Disinformation campaigns have become prevalent in the digital age. Various actors, including foreign governments, political parties, and interest groups, spread false or misleading information to shape public opinion and undermine their opponents. These campaigns often exploit existing left-right divisions by amplifying partisan narratives, promoting conspiracy theories, and fueling polarisation.
Social Media Manipulation: Social media platforms have become battlegrounds for political warfare. Manipulation tactics, such as the use of bots, trolls, and coordinated influence campaigns, are employed to spread propaganda, amplify certain viewpoints, and suppress opposing voices. This manipulation aims to reinforce existing divisions, deepen polarisation, and sway public opinion.
Identity Politics: Identity politics plays a significant role in contemporary political warfare. Activists, politicians, and interest groups often exploit social divisions based on race, gender, religion, or sexual orientation to advance their agendas. This can involve framing political issues in a way that appeals to specific identity groups and using divisive rhetoric to mobilise support or demonise opponents.
Online Harassment and Cancel Culture: Online harassment and cancel culture have become tactics used in political warfare. Individuals or groups perceived as holding opposing views are targeted with coordinated harassment campaigns, often including doxing (publicly sharing private information) and threats. Cancel culture involves the public shaming and ostracisation of individuals or organisations deemed to have violated perceived social or political norms, leading to reputational damage or professional consequences.
Election Interference: Election interference continues to be a prominent form of political warfare. State-sponsored actors and other entities attempt to influence elections through hacking, leaking sensitive information, spreading disinformation, and manipulating social media platforms. The objective is to undermine confidence in the democratic process, sow division among the electorate, and favor certain candidates or parties.
It’s important to note that political warfare exists on both sides of the ideological spectrum, and it is not limited to left or right-wing divisions. The examples above illustrate some of the current tactics and strategies used in political warfare, but it is a constantly evolving landscape influenced by technological advancements and changing political dynamics.
Chapter XIII: Soft Power
Soft power is the ability to influence others through attraction, persuasion, and co-option rather than through coercion or force. It is a concept introduced by political scientist Joseph Nye in the late 1980s, who argued that a country’s power is not only determined by its military and economic might, but also by its cultural appeal, values, and policies.
One of the earliest examples of the use of soft power was during the Cold War, when the United States and the Soviet Union competed for influence in the developing world. While the Soviet Union relied on economic aid and military assistance to win allies, the United States used its cultural and political influence to promote democracy, capitalism, and human rights.
Another example is Japan’s use of soft power in the 1980s and 1990s. Through its successful economic model and popular culture, such as anime, manga, and video games, Japan projected a positive image to the world and won many fans in Asia and beyond.
Today, China is perhaps the most visible practitioner of soft power, using its economic and cultural influence to enhance its global standing. China has invested heavily in its Confucius Institutes, which promote Chinese language and culture abroad, and in its Belt and Road Initiative, which aims to build infrastructure and improve connectivity across Asia and beyond.
Another example is the European Union, which has used its soft power to promote democracy, human rights, and economic prosperity in its neighbourhood and beyond. The EU’s enlargement policy, which has expanded the union to include 27 member states, is seen as a successful example of soft power in action.
Soft power can also be used by non-state actors, such as multinational corporations, NGOs, and social movements, to promote their interests and values. For example, tech companies like Google and Facebook have used their influence to promote free expression, privacy, and democratic values around the world.
This leads us on to political correctness:
political correctness can be seen as a form of cultural influence, as it shapes the discourse around social issues and norms. Countries that prioritise inclusivity and respect for marginalised communities can be seen as progressive and more appealing to global audiences. By adopting political correctness in their policies, cultural expressions, and public discourse, nations can enhance their soft power by projecting an image of social progress, fairness, and inclusivity.
It’s important to note that political correctness can also be a subject of debate and criticism. Some argue that it restricts free speech or stifles dissenting viewpoints. These debates highlight the complexities and challenges associated with navigating cultural norms, differing perspectives, and balancing freedom of expression with the need for inclusivity and sensitivity.
In conclusion, soft power is an increasingly important aspect of international relations, and countries and actors that can effectively use soft power can gain significant advantages in the global arena.
Chapter XIV: Globalisation and 5th Generation Warfare
I worked hard on this one …
Globalisation is the process of increased “inter-connectedness” and interdependence among people, businesses, and countries across the world. It involves the flow of goods, services, capital, and ideas across national borders, enabled by advances in transportation, communication, and technology.
Globalisation has been an ongoing process throughout human history, with various periods of intensified exchange and integration. Some historical examples include:
The Silk Road, a network of trade routes that connected China with the Mediterranean world from the 2nd century BCE to the 14th century CE.
The Age of Exploration, a period of European exploration and colonisation of the Americas, Africa, and Asia from the 15th to 17th centuries.
The Industrial Revolution, a period of technological innovation and economic growth in Europe and North America from the late 18th to early 20th centuries.
Globalisation has had a profound impact on modern warfare, particularly in the context of 5th generation warfare. Some of the ways in which globalisation and 5th generation warfare intersect include:
Transnational Networks and Operations
Globalisation has enabled the rise of non-state actors such as terrorist groups and transnational criminal organisations, which operate across multiple borders and exploit the vulnerabilities of a globalised world. These groups can use cyberspace, financial networks, and social media to plan and execute attacks, and to spread propaganda and disinformation.
Economic Interdependence
Globalisation has led to increased economic interdependence, with many countries relying on trade and investment flows to sustain their growth and development. As a result, economic sanctions and other forms of economic coercion have become key tools of 5th generation warfare, with countries seeking to use their economic leverage to achieve political or strategic objectives.
Technological Innovation
Globalisation has facilitated rapid advances in technology, including in areas such as artificial intelligence, biotechnology, and space exploration. These technologies have the potential to transform the nature of warfare, with countries seeking to develop new weapons systems and capabilities to gain an edge over their adversaries.
Information and Communication
Globalisation has enabled the rapid spread of information and ideas, including through social media and other online platforms. This has created new opportunities for influence operations and propaganda, with countries seeking to shape public opinion and disrupt the information environment of their adversaries.
In conclusion, globalisation has had a profound impact on the nature of modern warfare, particularly in the context of 5th generation warfare. It has enabled the rise of new threats and challenges, while also providing new tools and opportunities for state and non-state actors to achieve their objectives. As such, understanding the intersection between globalisation and 5th generation warfare is essential for policymakers and strategists seeking to navigate the complex and rapidly evolving security environment of the 21st century.
Chapter XV: Combating 5th Generation Warfare
Recognising and Countering 5th Generation Warfare Tactics
Combating 5th Generation Warfare requires recognition and awareness of the tactics being used, as well as the development and implementation of effective strategies across various sectors of society. Only by working together can we hope to effectively counter this new form of warfare and preserve democracy, security, and stability in the modern world.
Empowering Individuals in Countering 5th Generation Warfare
Raising awareness and understanding of 5th Generation Warfare tactics is vital for individuals, not just economies, to counter this form of warfare. By recognising these tactics and taking appropriate actions, individuals can contribute to the overall effort of safeguarding democracy, security, and stability. Here are a few examples of how individuals can play an active role:
Knowledge and Education: Individuals can educate themselves and others about the tactics employed in 5th Generation Warfare, raising awareness among their friends, family, and communities. By understanding the techniques used to manipulate information, sow discord, or spread disinformation, individuals can be better equipped to recognise and resist such attempts.
Critical Thinking and Media Literacy: Developing critical thinking skills and media literacy is crucial for individuals in the face of 5th Generation Warfare tactics. By questioning information sources, fact-checking, and considering diverse perspectives, individuals can avoid falling victim to false narratives and manipulation. Promoting media literacy in schools, workplaces, and communities can help individuals navigate the complex information environment effectively.
Civil Discourse and Dialogue: Open and respectful communication is essential in countering the fragmentation and polarisation caused by 5th Generation Warfare. Individuals can actively engage in civil discourse, seeking common ground and promoting constructive dialogue across ideological differences. By fostering understanding and empathy, individuals can mitigate the impact of divisive tactics employed in this form of warfare.
Support for Democratic Values and Institutions: Active participation in democratic processes, such as voting, engaging with elected representatives, and supporting institutions that uphold democratic principles, is crucial. By defending democratic values, advocating for transparency and accountability, and rejecting corruption, individuals can contribute to the resilience of democratic systems against 5th Generation Warfare tactics.
Additional Strategies to Counter 5th Generation Warfare
Counter-propaganda: Developing and disseminating counter-messaging to challenge false narratives and promote accurate information is essential in countering the influence of 5th Generation Warfare.
International Cooperation: Building partnerships with other countries and organisations to share information and resources for countering 5th Generation Warfare can enhance collective efforts.
Strengthening Democracy: Upholding democratic values and institutions, promoting transparency, and holding accountable those who engage in corrupt practices, disinformation, or other tactics used in 5th Generation Warfare is vital for preserving democratic systems.
Offensive Strategies: Developing offensive strategies to deter adversaries from engaging in 5th Generation Warfare, such as imposing sanctions, cyber-attacks, or using special forces to disrupt adversary networks and operations, can be part of a comprehensive approach.
Multidisciplinary Approach: Combating 5th Generation Warfare requires a multidisciplinary approach involving various sectors of society, including government, military, academia, media, and civil society. Collaborative efforts across these sectors can enhance effectiveness and resilience in countering this new form of warfare.
By combining individual efforts with these additional strategies, we can successfully confront 5th Generation Warfare and protect the values and principles that underpin our democratic societies.
Real Illuminati Media CIA Television Mass Mind Control Operation Mockingbird U.S.A. - https://rumble.com/v4b6vkr-real-illuminati-media-cia-television-mass-mind-control-operation-mockingbir.html
Real Illuminati Media Ultimate TV Mind Control Media Manipulation Pt.2 Documentary - https://rumble.com/v4bd5cq-real-illuminati-media-ultimate-tv-mind-control-media-manipulation-pt.2-docu.html
Real Illuminati One World Headquarter Order Out Of Chaos Freemasonry 1776-2024 - https://rumble.com/v4b8nqr-real-illuminati-one-world-headquarter-order-out-of-chaos-freemasonry-1776-2.html
Global Citizen One World Together At Home 15 Min. City UN Extreme Propaganda - https://rumble.com/v4bfaqz-global-citizen-one-world-together-at-home-15-min.-city-un-extreme-propagand.html
Welcome 2 New World Order Black-White-Yellow-Brown Peoples Dan Smoot Report - https://rumble.com/v4ervb0-welcome-2-new-world-order-black-white-yellow-brown-peoples-dan-smoot-report.html
Welcome 2 New World Order Black-White-Yellow-Brown-Red-Woke-Trans-Etc. Peoples Of The New America Phoenix Rising From The Ashes... See The True Dan Smoot Report To U.S.A.. So Yes America Is A Republic & Is Not A Democracy Is A Dangerous And Wrong Argument Enabling Sustained Minority Rule At The National level Is Not A Feature Of Our True Constitutional Design But A Perversion Of It. We The True People's Of The Worlds.
-
 28:31
28:31
What If Everything You Were Taught Was A Lie?
2 days agoIf Heaven’s Is So Perfect, Why Do They Saint Peter Lock The Gates To Heaven’s By George Carlin
1.42K1 -
 2:30:00
2:30:00
Laura Loomer
8 hours agoEP142: Loomer Prompts Calls For FBI To Investigate Palestinian Youth Movement
40.9K18 -
 1:26:34
1:26:34
Man in America
11 hours agoExposing the Cover-Up That Could Collapse Big Medicine: Parasites
46.1K19 -
 4:53:00
4:53:00
CHiLi XDD
6 hours agoTekken Fight Night
24.4K1 -
 9:25:57
9:25:57
ItsLancOfficial
12 hours agoFREAKY FRIDAY-GETTING FRIED-WELP! #TOTS
24.2K4 -
 1:09:11
1:09:11
Sarah Westall
7 hours agoRead the Signs: Are We Already Operating in a New Financial System? w/ Andy Schectman
37.5K7 -
 1:32:53
1:32:53
Flyover Conservatives
11 hours agoRicky Schroder Exposes How Hollywood Planted Him as a Child Star | FOC Show
47.7K12 -
 4:59:48
4:59:48
JahBlessCreates
5 hours ago🎉 TEKKEN TING, and maybe some music...
24.7K14 -
 LIVE
LIVE
GritsGG
7 hours agoTop 250 Ranked Grind! Dubulars!🫡
53 watching -
 4:31:29
4:31:29
StuffCentral
6 hours agoStar Stuffy
9.23K4