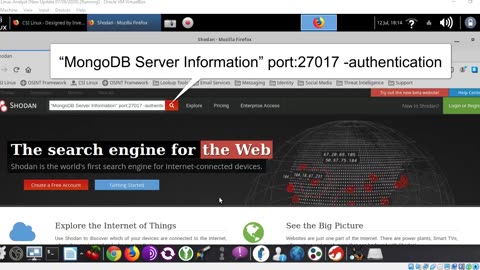
Using Shodan to Search for Vulnerable Databases
Using Shodan to Search for Vulnerable Databases
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
3
views
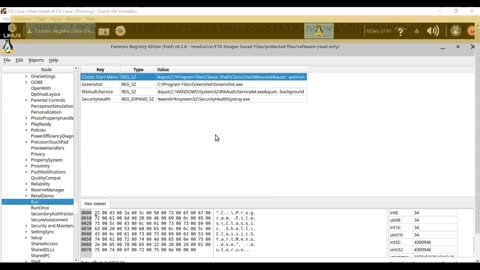
Acquiring a Forensic Copy of the Windows Registry
Acquiring a Forensic Copy of the Windows Registry
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
2
views
Create a Kali Live (forensic Mode) Bootable USB
Create a Kali Live (forensic Mode) Bootable USB
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
1
view
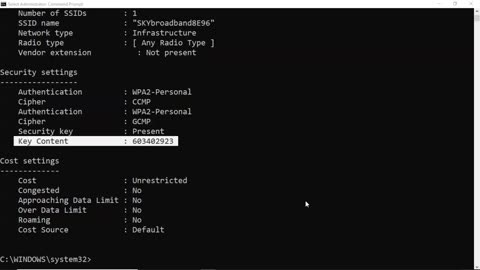
Dumping Wi-Fi Credentials Using netsh
Dumping Wi-Fi Credentials Using netsh
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
19
views
Analyzing the Windows Registry for Evidence
Analyzing the Windows Registry for Evidence
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
3
views
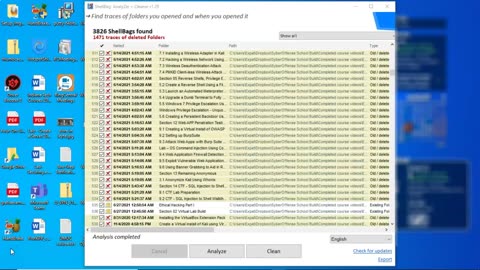
Using Shellbags to View Hidden or Deleted Folders
Using Shellbags to View Hidden or Deleted Folders
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
1
view
Email Header Analysis
Email Header Analysis
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
3
views
Memory Forensics Using the Volatility Framework
Memory Forensics Using the Volatility Framework
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
4
views
Extracting Thumbnail Images From a Suspects Machine
Extracting Thumbnail Images From a Suspects Machine
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
1
view
Gathering Windows System Information Using Live-Forensicator
Gathering Windows System Information Using Live-Forensicator
Introduction to Using Ghidra
Introduction to Using Ghidra
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
3
views
Install Ghidra on CSI Linux
Install Ghidra on CSI Linux
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
14
views
Automated Recon Enumeration Using nmapAutomator
Automated Recon Enumeration Using nmapAutomator
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
33
views
Authorize a Windows 2016 DHCP Server
Authorize a Windows 2016 DHCP Server
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
42
views
Basic Linux Commands Everyone Needs to Know
Basic Linux Commands Everyone Needs to Know
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
8
views
Backup and restore Group Policy Objects in Active Directory
Backup and restore Group Policy Objects in Active Directory
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
109
views
Before You Install Active Directory...Watch This Video!
Before You Install Active Directory...Watch This Video!
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
75
views
Basic website configuration using IIS in Windows Server 2019
Basic website configuration using IIS in Windows Server 2019
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
4
views
Brute Force the SMB Password on a Windows Server
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
4
views
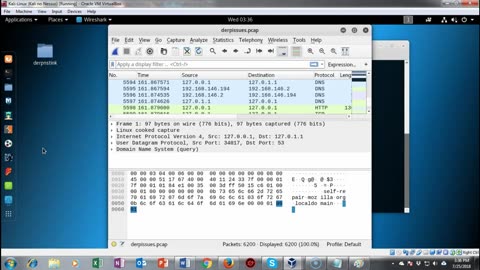
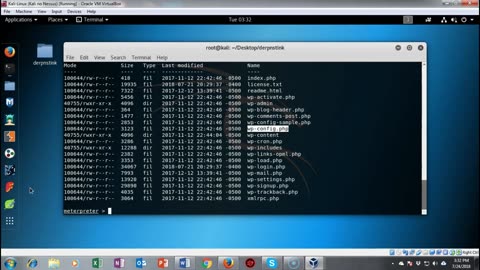
Capture the Flag - Derpnstink - Walkthrough Part II
Capture the Flag - Derpnstink - Walkthrough Part II
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
19
views
Capture the Flag - DerpnStink - Walkthrough Part I
Capture the Flag - DerpnStink - Walkthrough Part I
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
20
views
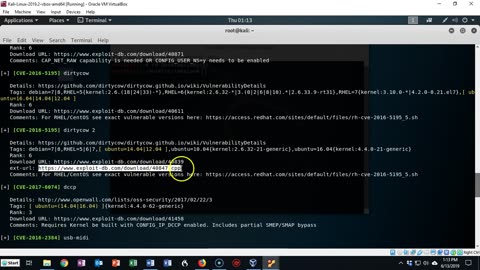
Capture the Flag - DC-1 - Footprinting, Enumeration
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
6
views
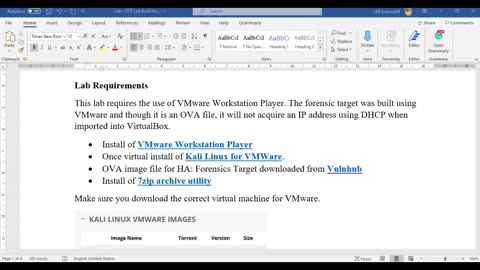
Capture the Flag - HA Forensics - Lab Build
Capture the Flag - HA Forensics - Lab Build
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
10
views
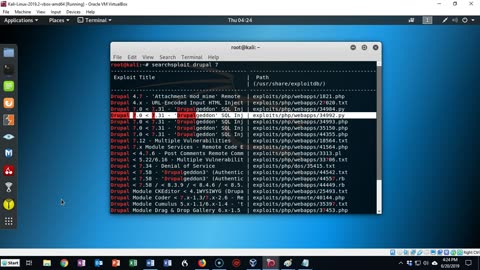
Capture the Flag - Lampiao - Exploitation, Privilege Elevation
Capture the Flag - Lampiao - Exploitation, Privilege Elevation
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
24
views
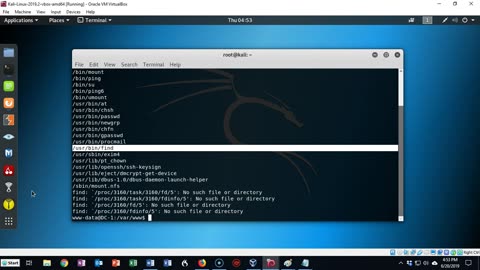
Capture the Flag - DC-1- Exploitation, Privilege Elevation
Excerpt video from one of my many online courses.
1000+ videos on hacking, operating systems, digital forensics, and Microsoft applications
https://www.syberoffense.net - Official course site.
Have online courses for sale? Contact Syberoffense at info@syberoffense.com
Facebook - https://www.facebook.com/sybertraining
9
views