Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
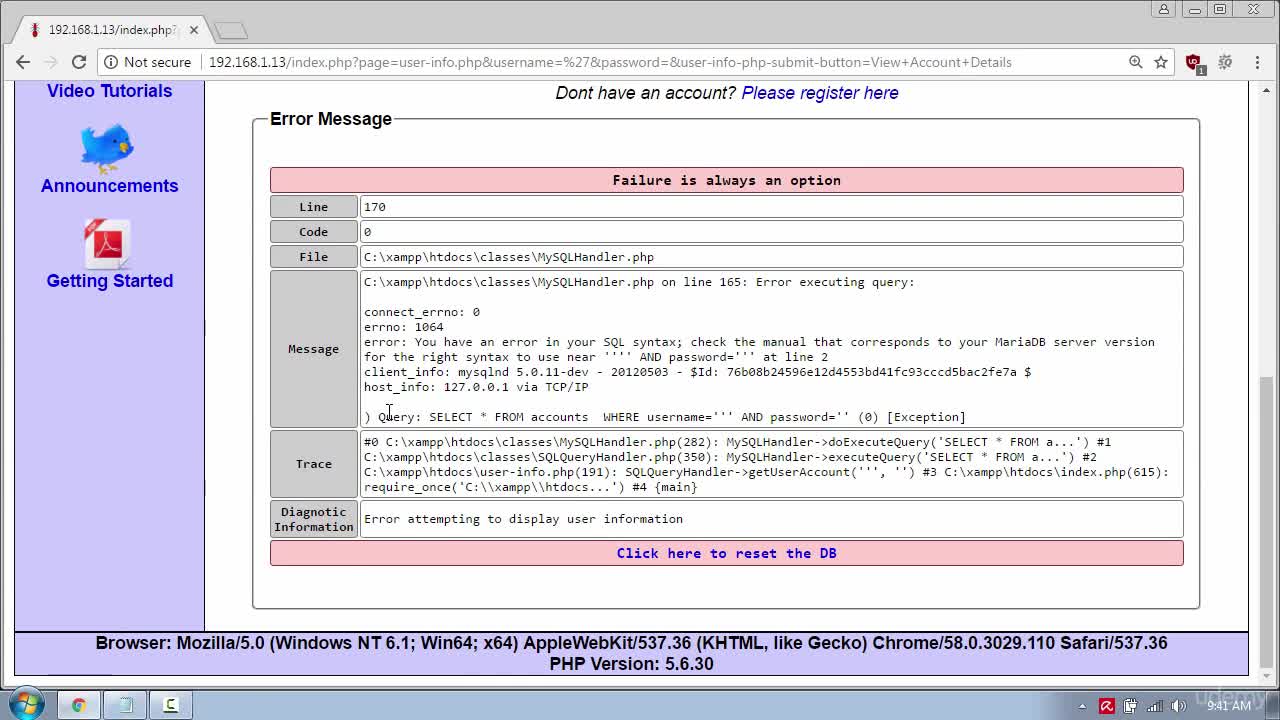
Web Hacking for Beginners part 7 - Understanding How SQL Injection Attacks Work
4 years ago
17
Web Hacking for Beginners part 7 - Understanding How SQL Injection Attacks Work
Loading comments...
-
 9:27
9:27
Dellers
4 years ago $0.01 earnedSwift for Beginners Part 6
74 -
 9:54
9:54
Dellers
4 years agoSwift for Beginners Part 3
44 -
 7:52
7:52
Dellers
4 years agoSwift for Beginners Part 9
25 -
 5:28
5:28
Dellers
4 years ago $0.03 earnedSwift for Beginners Part 1
117 -
 LIVE
LIVE
The Charlie Kirk Show
1 hour agoJUDGMENT DAY 2025: The Election Results Stream
17,468 watching -
 LIVE
LIVE
MattMorseTV
2 hours ago🔴Election Day LIVE COVERAGE.🔴
1,887 watching -
 LIVE
LIVE
Due Dissidence
7 hours agoLIVE: ELECTION RESULTS From NYC, NJ, and VA - Trump Approval CRATERS, Kash's Private Jet CRASH OUT
1,364 watching -
 1:03:37
1:03:37
BonginoReport
2 hours agoElection Night Showdown Spotlight - Nightly Scroll w/ Hayley Caronia (Ep.170)
82.8K16 -
 LIVE
LIVE
Edge of Wonder
2 hours agoSupernatural Forces & Giants Built Great Pyramid of Egypt
130 watching -
 1:24:03
1:24:03
Kim Iversen
3 hours agoAn Islamist Socialist in NYC? The Panic Is Epic | Neocons To Tucker: 'Love Israel OR ELSE'
72.1K90