Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
Configuring and Securing ACR and AKS
5 years ago
38
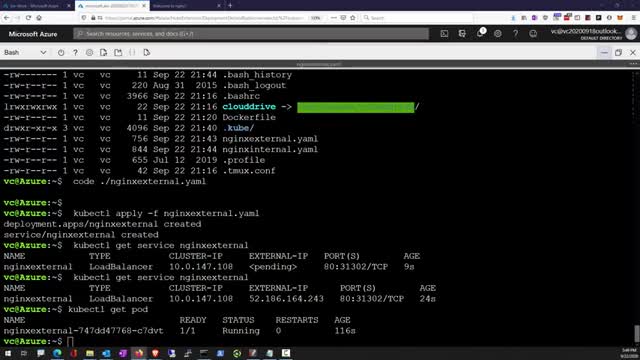
You have been asked to deploy a proof of concept with Azure Container Registry and Azure Kubernetes Service. Specifically, the proof of concept should demonstrate:
Using Dockerfile to build an image.
Using Azure Container Registry to store images.
Configuring an Azure Kubernetes Service.
Securing and accessing container applications both internally and externally.
Loading comments...
-
 5:55
5:55
Legacy Springs Dexters
5 years ago $0.01 earnedsecuring duck house on creek
67 -
 2:17
2:17
TheTechCatalyst
5 years agoConfiguring a Webex Meetings Profile Picture
68 -
 9:46
9:46
MattMorseTV
17 hours ago $24.50 earnedTrump just SHUT DOWN a $287,000,000 FRAUD RING.
38.6K98 -
 LIVE
LIVE
JakRazGaming
48 minutes agoPlaying Hogwarts Legacy!! Playthrough Stream 4
97 watching -
 1:16
1:16
From Zero → Viral with AI
21 hours agoAI Isn’t Killing Work. It’s Killing the Wrong Kind of Work.
995 -
 2:47:27
2:47:27
Squaring The Circle, A Randall Carlson Podcast
20 hours agoEPIC! Randall & Sabin Howard, Master Sculptor Known As "Michelangelo of America," talk WAR or PEACE!
1.48K -
 22:42
22:42
Benjamin Sahlstrom
1 day ago $18.01 earnedHow To Refill 1lb Portable Propane Tanks!
110K15 -
 46:39
46:39
The Bold Lib
1 day agoOwen Shroyer: BOLDTALK W/Angela Belcamino
9.31K23 -
 7:57
7:57
Blackstone Griddles
1 day agoDouble Barrel Sausage Sandwich | Blackstone Griddles
26.2K1 -
 32:24
32:24
Forrest Galante
13 hours agoHunting and Eating The World's WORST Fish (Everglades At Night)
109K7