Premium Only Content
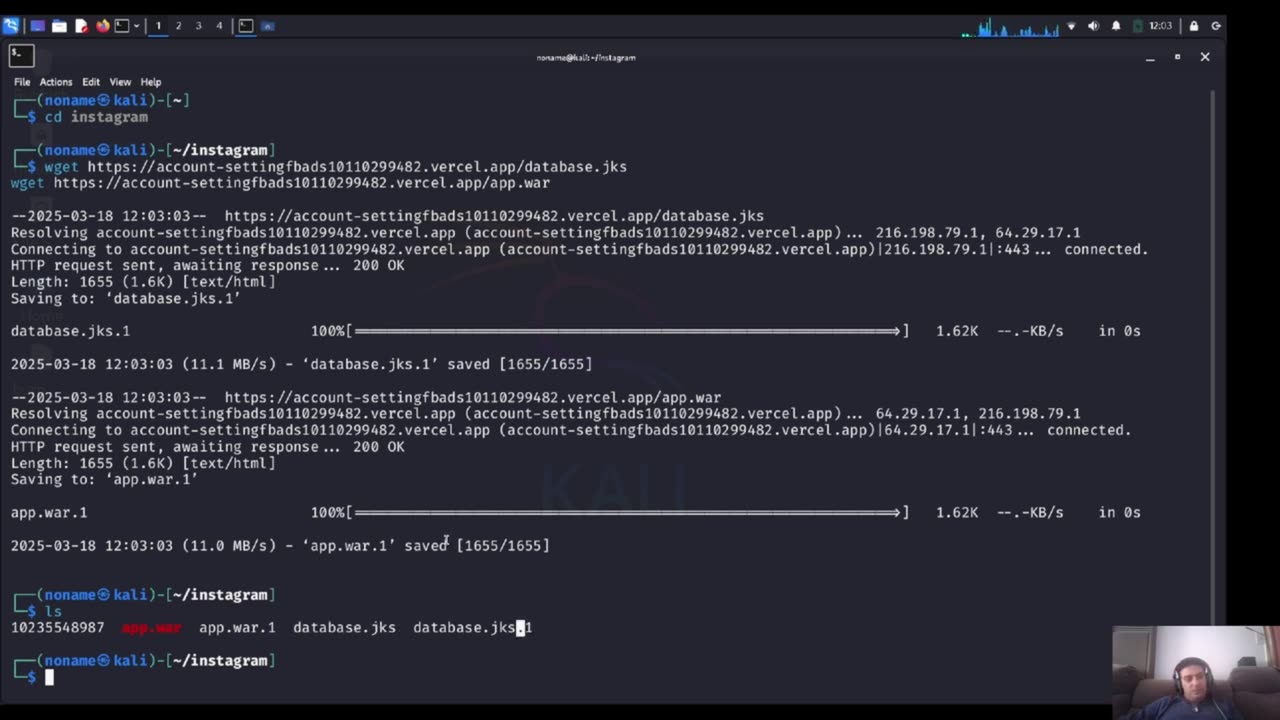
Trace back a hacker Part 2 of 2 Analysis - 18-3-2025
🔥 Trace Back a Hacker - Part 2 of 2: Analysis 🔥
In Part 1, we gathered intelligence and reconnaissance data. Now, in Part 2, we take it a step further by analyzing the hacker’s digital footprint, tracking their movements, and uncovering their methods. This episode focuses on forensic analysis, network tracing, and intrusion detection techniques used by cybersecurity professionals.
🔍 What You’ll Learn:
Log file analysis for suspicious activities
Network traffic monitoring and packet inspection
Digital forensics techniques to track attackers
Identifying malicious scripts, exploits, and backdoors
Tools like Wireshark, Splunk, and forensic frameworks
🎯 Who is this for?
Cybersecurity analysts, ethical hackers, IT security professionals, and anyone interested in cyber forensics & digital investigations.
🚀 Missed Part 1? Watch it now to learn about gathering intelligence before diving into analysis!
#TraceHacker #CyberSecurity #EthicalHacking #PenetrationTesting #CyberForensics #NetworkSecurity #OSINT #InfoSec #ThreatAnalysis #CyberThreats #RedTeam #BlueTeam #CyberAwareness #DigitalInvestigation #StMonicaITDon't
forget to subscribe to our YouTube channel for video tutorials, live sessions, and more interactive content.
Welcome to CyberSec Insights: Your Guide to Cybersecurity and Hacking Tricks!
Explore the fascinating world of cybersecurity with our comprehensive blog. Designed for everyone from beginners to seasoned professionals, we provide the latest security trends, hacking techniques, and practical tips to protect yourself and your organization. Our in-depth tutorials, expert advice, and real-world applications will enhance your skills and keep you ahead in the ever-evolving cyber landscape.
Join us on a journey to uncover the secrets of cybersecurity, empowering you with the tools and knowledge to secure the digital realm. Stay informed, stay safe!
#ciscorouter #cisco #router #routersetup #cybersecurity #cyberprotection #cybersecurityawareness #technology #technicalsupport #msp #microsoft #apple #informationsecurity #informationtechnology #stmonicait
-
 1:27:58
1:27:58
Coin Stories with Natalie Brunell
15 hours agoQuantum Threat to Bitcoin? Pysh & Lepard Break Down Quantum, A.I. Displacement and Growing Socialism
1181 -
 3:53
3:53
WildCreatures
3 days ago $0.15 earnedSwimming With the Giants, Whale Sharks of Darwin Island
1.1K3 -
 12:09
12:09
Actual Justice Warrior
17 hours agoTEEN Mob ATTACKS Domino's Pizza
2.08K16 -
 18:59
18:59
Nate The Lawyer
1 day ago $0.77 earnedDon Lemon Spreads Lie: Crossing Border Illegally Isn’t a Crime. FACT CHECK
13.3K26 -
 2:04:30
2:04:30
Side Scrollers Podcast
19 hours agoGold’s Gym CONTROVERSY & BOYCOTT + Craig ADMITS DEFEAT + More | Side Scrollers
63.4K14 -
 1:26:06
1:26:06
MattMorseTV
18 hours ago $0.13 earned🔴Trump's Press Conference MASSIVE UPDATE.🔴
14.7K67 -
 21:39
21:39
Nikko Ortiz
3 days agoI Take A North Korean Shooting
53.7K8 -
 LIVE
LIVE
Lofi Girl
3 years agolofi hip hop radio 📚 - beats to relax/study to
193 watching -
 2:14:13
2:14:13
FreshandFit
16 hours agoShe Was Given Extravagant Gifts And STILL Friendzoned Him +EXPOSED
203K46 -
 1:16:07
1:16:07
Man in America
13 hours agoOperation Gladio: The CIA, Mossad & City of London’s Plan for a New World Order
35K36