Premium Only Content
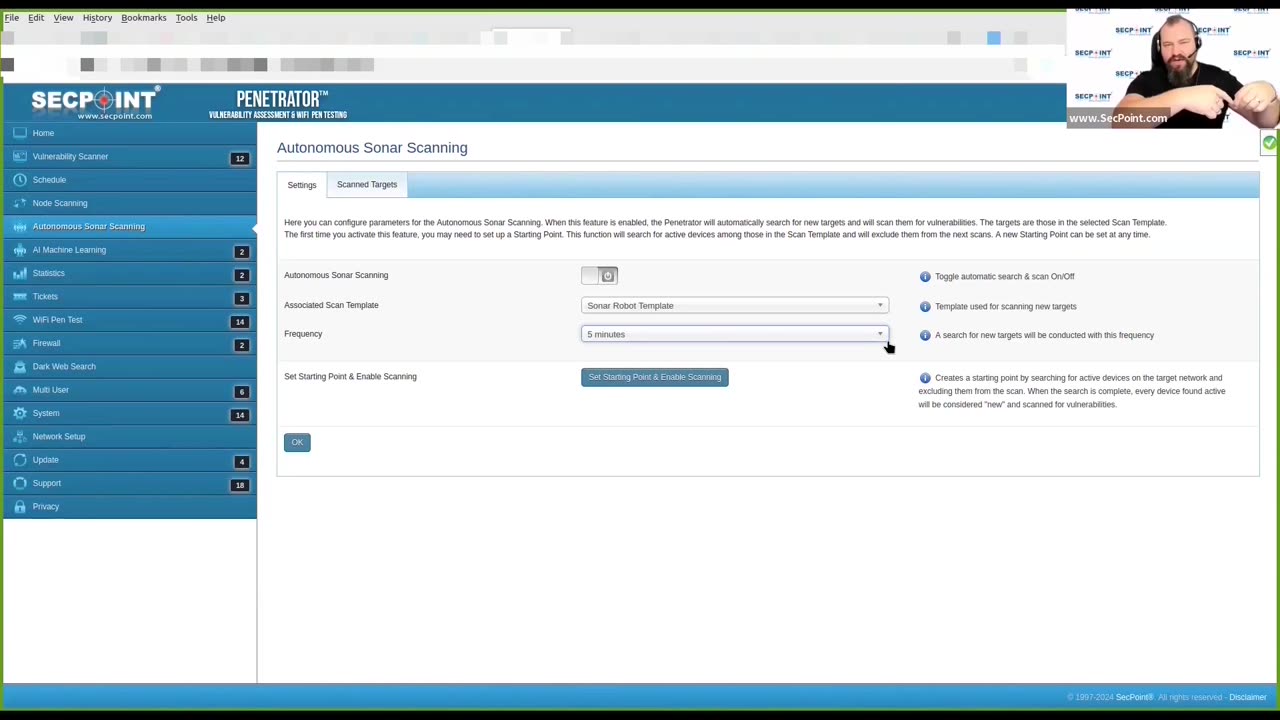
🛡️ SecPoint® Penetrator – Sonar Detect Hostile Devices
In this video, we show how the powerful Sonar feature in the SecPoint Penetrator can help detect unauthorized or hostile devices connected to your network.
Quickly identify suspicious activity such as:
✅ A new Linux device appearing on a Windows-only environment
✅ Unknown systems joining your network segment
✅ Devices plugged in without permission – potential insider threats
The Sonar scan is ideal for securing sensitive environments by actively monitoring connected devices and flagging anomalies before damage is done.
💻 Key Features of the SecPoint Penetrator:
✅ Authenticated Vulnerability Scanning via SSH
✅ Supports Cisco, Linux, NetBSD, OpenBSD & FreeBSD
✅ Detects Missing Patches, Weak Configurations & More
✅ Customizable Reports – Export in .txt, .html, .pdf formats
✅ Fully On-Premise – No cloud, no data leaks
✅ Easy compliance with 33+ scanning profiles
✅ Includes Dark Web Search & WiFi Testing
🔗 Explore More:
https://www.secpoint.com/penetrator.html
🎁 Try Our Free Online Vulnerability Scan:
https://www.secpoint.com/free-vulnerability-scan.php
https://www.secpoint.com/contact-me.php
📣 Stay Connected:
🔹 Twitter (X): https://x.com/secpoint
🔹 LinkedIn: https://www.linkedin.com/company/secpoint
👍 Like, Share & Subscribe for the latest in cybersecurity and vulnerability scanning!
#CyberSecurity #SecPoint #Penetrator #SonarScan #HostileDeviceDetection #NetworkMonitoring #InsiderThreat #VulnerabilityScanner #ITSecurity #CyberDefense
-
 19:56
19:56
GritsGG
12 hours agoSpectating Random Solo Players in a Bot Lobby!
411 -
 LIVE
LIVE
Lofi Girl
2 years agoSynthwave Radio 🌌 - beats to chill/game to
229 watching -
 16:22
16:22
BlabberingCollector
2 days agoHarry Potter HBO: Addressing Some New Rumors!
401 -
 4:01:30
4:01:30
Badlands Media
19 hours agoThe Narrative Ep. 37: The Sovereign War
156K32 -
 11:23:54
11:23:54
SpartakusLIVE
12 hours agoMega SOLO Spartan Stream - 12 hours?! HA || Variety Later?!
100K -
 DVR
DVR
Rallied
5 hours ago $15.67 earnedSolo Warzone Challenges All Night
39.3K3 -
 4:53:38
4:53:38
Due Dissidence
15 hours agoTaibbi DEFENDS Weiss-CBS Deal, Pakman Producer SPILLS TEA, Massie CALLS OUT Trump Informant Claims
26.4K34 -
 2:33:47
2:33:47
TheSaltyCracker
7 hours agoMedia Silent on Metro Attack ReeEEStream 9-07-25
142K271 -
 56:27
56:27
Sarah Westall
8 hours agoEnd of Aging, Hydrogen Bomb Research, Serial Killers & Violent Behavior, Bipolar Research w/Dr Walsh
37.2K6 -
 4:36:53
4:36:53
MattMorseTV
10 hours ago $15.67 earned🔴Sunday Gaming🔴
68.4K5