Premium Only Content
🔐 Brute Force Hashing & SHA256 Explained!
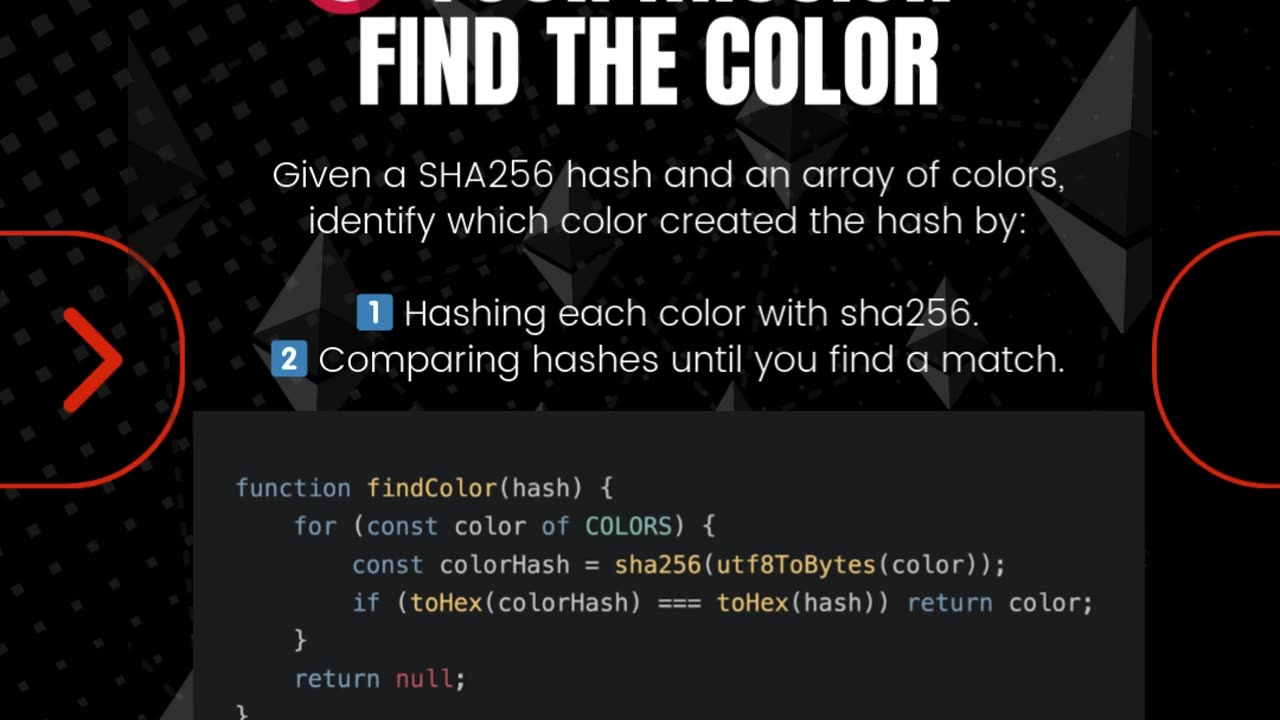
Ever wondered how data is protected in the digital world? Enter cryptographic hash functions like SHA256! These one-way functions transform input into unique, fixed-length hashes that are nearly impossible to reverse. But here’s the twist—hackers can brute-force their way to the original input using precomputed Rainbow Tables or by guessing common inputs. That’s where salting comes in, adding a random, unique value to the input to make cracking it virtually impossible. 🛡️
In our task, we’re unraveling the mystery of a hash by matching it to a color from a predefined list. Using tools like utf8ToBytes, sha256, and toHex, we loop through each possible color, hash it, and compare it to find the match. It’s a fun, hands-on way to see the power of cryptography in action—and understand why it’s so crucial in keeping our digital world secure. Ready to crack the code? 🔐✨
-
 15:30
15:30
IsaacButterfield
17 hours ago $0.22 earnedViolent Immigrant Crime Is Exploding in Australia
1K8 -
 8:37
8:37
DBoss_Firearms
7 hours agoHow hard is it to shoot with a G-Flex Trigger?
11 -
 1:05:17
1:05:17
BonginoReport
4 hours agoWhite House Claps Back At Sabrina Carpenter - Nightly Scroll w/ Hayley Caronia (Ep.189)
96.7K21 -
 1:06:50
1:06:50
TheCrucible
5 hours agoThe Extravaganza! EP: 69 (12/03/25)
66.6K17 -
 1:08:49
1:08:49
Kim Iversen
4 hours agoEpstein Island: What's With The Creepy Medical Chair and Masks?
41.2K33 -
 23:54
23:54
Jasmin Laine
5 hours agoCarney’s WORST Day EVER—BOOED, Fact-Checked, and Forced to FLEE the House
24.6K17 -
 1:59:47
1:59:47
Redacted News
5 hours agoDeep State Coup Coming for Trump? New JFK Files Released and NATO Preparing Attack on Russia
163K109 -
 7:31:43
7:31:43
Dr Disrespect
10 hours ago🔴LIVE - DR DISRESPECT'S TRIPLE THREAT CHALLENGE - ARC RAIDERS • BF6 • FORTNITE
102K8 -
 1:00:57
1:00:57
Russell Brand
7 hours agoThe Vaccine Ideology Unmasked | Dr Peter McCullough - SF658
128K39 -
 1:11:25
1:11:25
vivafrei
6 hours agoKash Patel's Jacket-Gate! Pfizer Whistleblower Qui Tam on Appeal! Meanwhile in Canada! AND MORE!
70.4K45