Premium Only Content
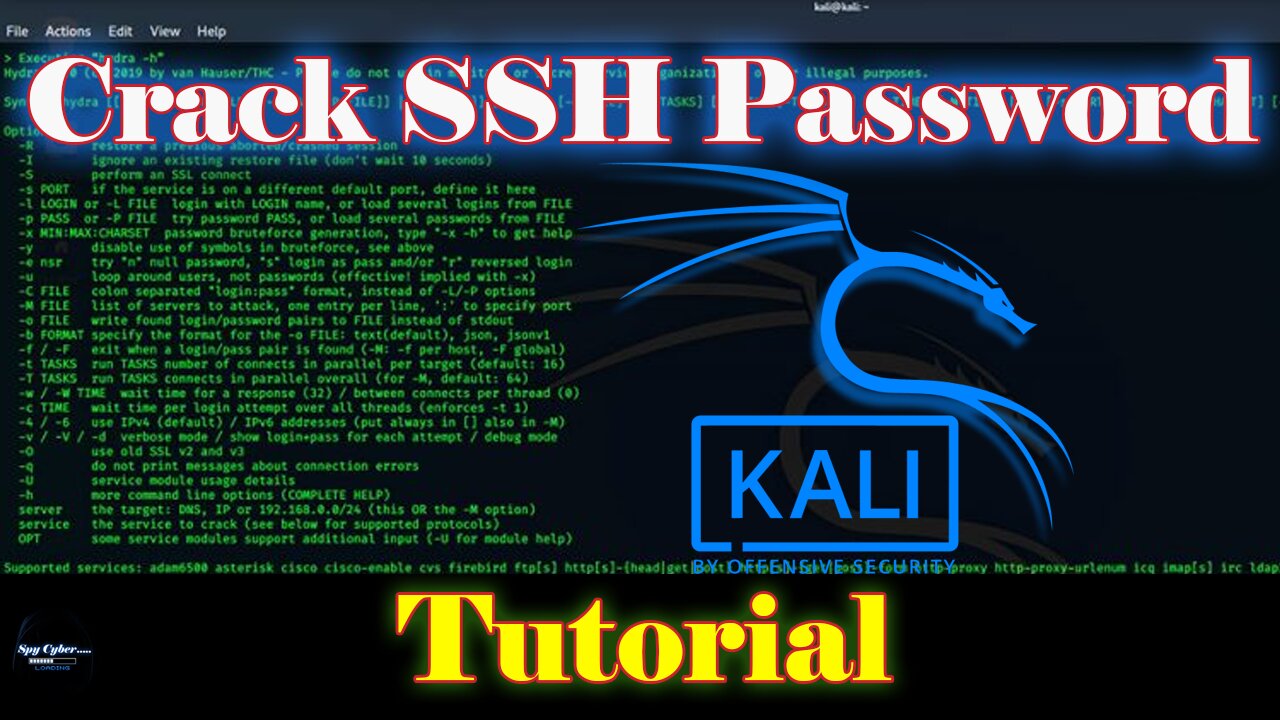
Hacking SSH is Easy in Kali Linux // Cybersecurity 2024
A cryptographic network protocol called Secure Shell Protocol (SSH) is used to run network services safely over an unprotected network. Command-line execution and remote login are two of its uses. The client-server architecture—that is, the SSH client and the SSH server is the foundation of SSH protocols.
The SSH Bruteforce attack Since Kali Linux is mostly used for advanced penetration testing and security auditing, we shall use it in this post.
Initially, in order to reach the compromised machine, we require the machine's address, also known as its IPV4 address. Following that, we require a username and a matching password. The brute force technique is used in this case, and we create the two username and password
Notes:
https://github.com/SpyCyber/Notes
Join Spycyber's growing community
-------------------------------------------------------------------------
Facebook: https://www.facebook.com/spycyber.us
Reddit: https://www.reddit.com/r/spycyber/
Quora: https://spycyber.quora.com/
GitHub: https://github.com/SpyCyber
TikTok: https://www.tiktok.com/@spycyber_official
Website: https://spycyber.us/
#cybercrime #lazyscript #kali_linux #linux #hacking #IT #cybersecurity #windowsserver #Networking #CCNA #CCNP #InformationTechnology #ITCertifications #spycyber
Disclaimer: This video is for educational purposes only. I own all the equipment used for this demonstration.
-
 16:11
16:11
RealMetatron
19 hours agoHasan Piker got HUMBLED in New York
7.43K5 -
 LIVE
LIVE
Viss
3 hours ago🔴LIVE - Helping Those That Need It Today - Arc Raiders!
153 watching -
 43:37
43:37
The Rubin Report
3 hours agoTriggernometry Hosts Try to Hide Their Shock at Sam Harris’ Charlie Kirk Claim
29.7K28 -
 LIVE
LIVE
SOLTEKGG
2 hours ago🟢 Live: Pro Player Returns to Battlefield 6 RED SEC
45 watching -
 LIVE
LIVE
StevieTLIVE
3 hours agoFriday Warzone HYPE: Come Chill, Chat, and Watch Me Fry
33 watching -
 1:00:57
1:00:57
Dr. Eric Berg
3 days agoThe Dr. Berg Show LIVE - November 21, 2025
19.9K9 -
 LIVE
LIVE
Film Threat
19 hours agoWICKED FOR GOOD + SISU 2 + LOADS OF REVIEWS! | Film Threat Livecast
79 watching -
 1:39:56
1:39:56
The Mel K Show
3 hours agoMORNINGS WITH MEL K - Globalists Continue to Pursue Agenda 2030-While Americans are Being Easily Distracted 11-21-25
18.5K5 -
 1:02:43
1:02:43
VINCE
5 hours agoDid The Democrats Really Just Commit Treason? | Episode 174 - 11/21/25 VINCE
211K220 -
 1:01:48
1:01:48
Benny Johnson
4 hours agoHow To Fix The Biggest Crisis In America: Housing | Saving The American Dream for Young People 🇺🇸
55.4K80