Premium Only Content
Sublist3r Tutorial: Discover Subdomains with Ease
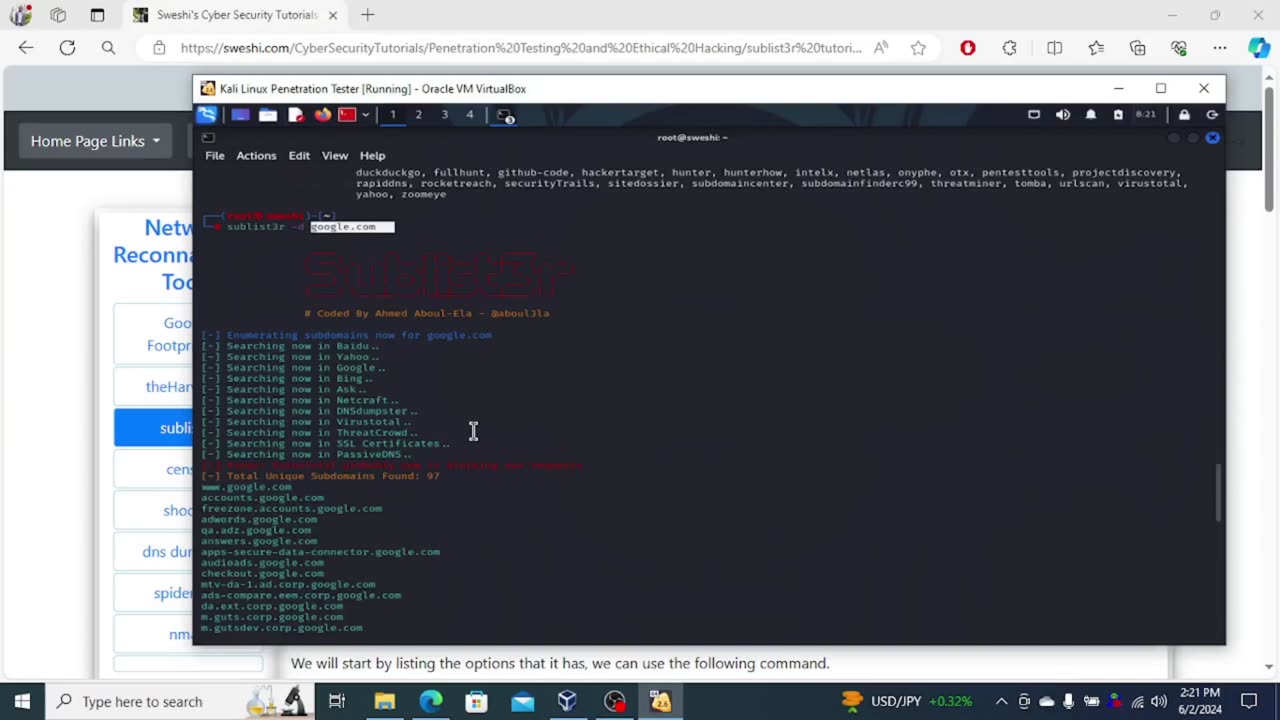
Sublist3r (commonly stylized as Sublist3r) is a tool included in Kali Linux for enumerating subdomains of websites, helping cybersecurity professionals in reconnaissance tasks.
SUBLISTER
00:17 - sublister introduction
01:00 - searching for subdomains of google
01:45 - results
02:12 - saving the results
02:38 - searching for domain names with open ports
03:25 - conclusion
Reconnaissance tutorials
Google Footprinting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/GoogleFootprinting.php
theHarvester tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/theHarv3ster%20-%20Network%20Reconnaissance%20tool%20tutorial.php
sublister tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sublist3r%20tutorial.php
censys free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/censys%20tutorial.php
shodan free tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/shodan%20tutorial.php
dns dumpster tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dns%20dumpster%20tutorial.php
spiderfoot tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/spiderfoot%20tutorial.php
nmap tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Nikto web server scanning Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Dirbuster web directory scanner Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/dirbuster%20tutorial.php
Nmap port scanner:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nmap%20tutorial.php
Legion port scanner and vulnerability scanning tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/legion%20tutorial.php
hping3 packet crafting tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/hping3%20tutorial.php
amap scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/amap%20tutorial.php
masscan fast port scanner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/masscan%20tutorial.php
netcat tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/netcat%20tutorial.php
VULNERABILITY SCANNING TUTORIALS
Nessus tenable tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nessus%20tenable%20essentials%20tutorial.php
Nikto tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/nikto%20tutorial.php
Exploit tools:
Metasploit beginner tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/metasploit%20tutorial.php
SQL Map tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/sqlmap%20tutorial.php
routersploit tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/routersploit.php
FORENSIC INVESTIGATION TOOLS:
Wireshark Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/wireshark%20tutorial.php
LastActivityView tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/lastActivityView%20tutorial.php
Process Monitor Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/Process%20Monitor%20Tutorial.php
Autoruns Tutorial:
https://sweshi.com/CyberSecurityTutorials/Penetration%20Testing%20and%20Ethical%20Hacking/autoruns%20tutorial.php
-
 20:46
20:46
Jasmin Laine
1 day agoJoe Rogan Drops NUKE—Carney’s Secret Deal + 100,000 Kamloops Homes at Risk
1.93K15 -
 4:00
4:00
Mrgunsngear
1 day ago $13.87 earnedFirst They Came For Glock, Now They're Coming For The Ruger RXM
7.54K15 -
 1:42:46
1:42:46
Lara Logan
1 day agoINJECTING TRUTH INTO THE VACCINE DEBATE with Del Bigtree | Ep 43 | Going Rogue with Lara Logan
6.79K31 -
 12:55
12:55
Cash Jordan
18 hours agoNYC Busses 'MOBBED' by Millionaires... as "Communist" Mayor VOWS to END AMERICA
38215 -
 LIVE
LIVE
Major League Fishing
1 day agoLIVE! MLF Toyota Series Championship!
698 watching -
 18:54
18:54
Bearing
1 day agoNew York COMMUNIST TAKEOVER 🚨 Zoran Mamdani’s Revolution 💥
3.12K65 -
 1:05:26
1:05:26
Man in America
1 day ago“Poseidon” Doomsday Sub, Microplastics & The War on Testosterone w/ Kim Bright
40.2K55 -
 12:15
12:15
Degenerate Jay
20 hours agoIs GTA 6 In Trouble?
226 -
 LIVE
LIVE
FyrBorne
14 hours ago🔴Battlefield 6 Live M&K Gameplay: Who's Hunting Who?
759 watching -
 LIVE
LIVE
Times Now World
5 days agoVladimir Putin LIVE | Putin rushes to help Maduro, sends Wagner Group | US-Venezuela News | Trump
99 watching