Premium Only Content
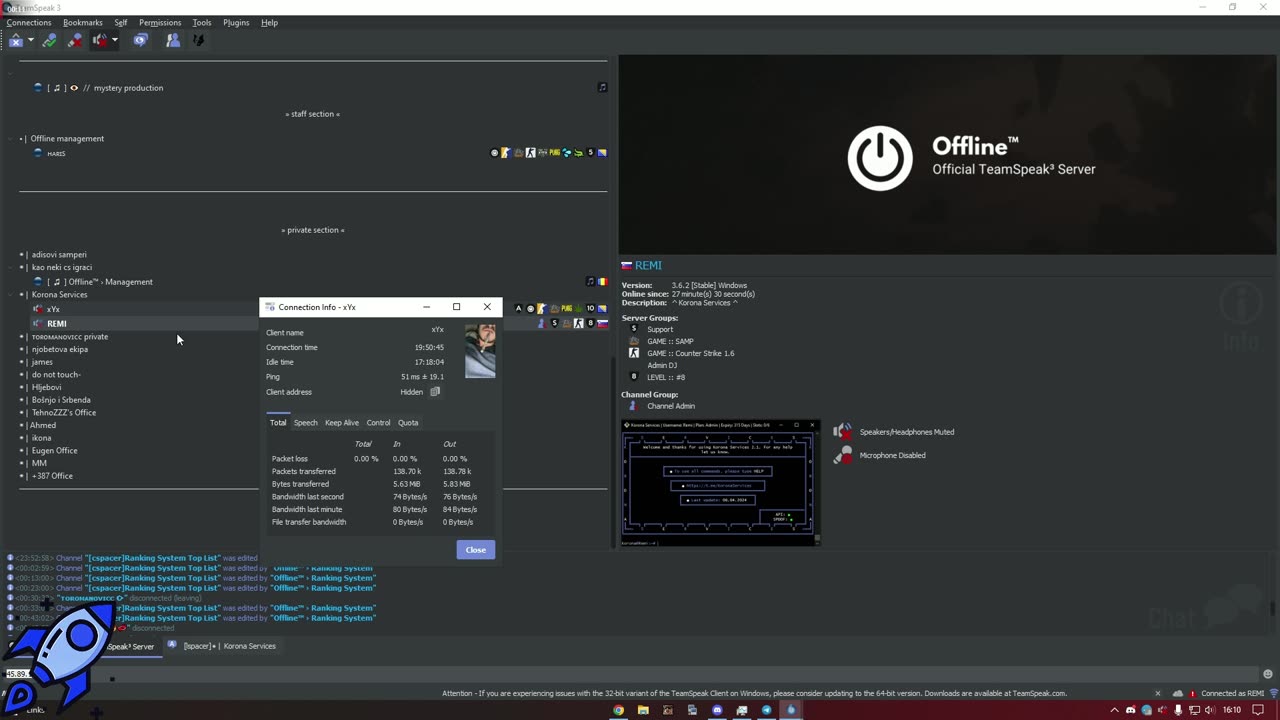
Unveiling the Vulnerabilities: Attacking Teamspeak3 Voice Servers | https://lkxstress.su/
Websites:
https://lkxstress.su/
https://lkxstresse.ru
https://lkxstress.ru
https://t.me/addlist/o256hsAqEgYzODY8 - LKX Group Folder 😂
ddos,ts3,ddos saldırısı,ddos attack,what is ddos,ddos attacks,loddos,ts3parki ddos attack,dos vs ddos,how to ddos,ddos yiyor,ddos nedir,elraen ddos,ddos atıyor,what is a ddos,elraenn ddos,flundar ddos,ts3 apk,ddos a website,elraen vs ddos,elraenn vs ddos,ts3 açma,loddos nedir,vds saldırı ddos,ts3 küfür,ts3 kurma,ts3 remix,elraen ddos yiyor,elraenn ddos yiyor,what is a ddos attack,elraen flundar ddos,ts3 kavgası,ts3 android, teamspeak3,ddos,teamspeak,teamspeak3 saldiri ddos attack tim (yusuf gg),teamspeak3 attack,teamspeak 3 server,kostenloser teamspeak,teamspeak 3 server setup,kostenloser teamspeak 3 server,ddos saldırısı,kostenloser teamspeak server,teamspeak 3 server ohne hamachi,kostenlos einen teamspeak server erstellen [24/7],loddos,teamsperak mit vollen rechten gratis,ddos schutz,vds saldırı ddos,loddos nedir,ts3parki ddos attack,loddos ile saldırı, Teamspeak3
Voice servers
Server security
Cybersecurity
Ethical hacking
Penetration testing
Network security
Cyber attacks
Vulnerability assessment
Exploitation techniques
Information security
Hacking tools
Exploit development
Malware analysis
Reverse engineering
Social engineering
Phishing attacks
Denial of service
Distributed denial of service
Network protocols
TCP/IP
UDP
Port scanning
Firewall bypass
Intrusion detection
Intrusion prevention
Web security
SQL injection
Cross-site scripting
Cross-site request forgery
Man-in-the-middle attacks
Packet sniffing
Encryption
Cryptography
Public key infrastructure
SSL/TLS
VPN
Proxy servers
Tor network
Anonymity online
Dark web
Cybercrime
Cyber law
Digital forensics
Incident response
Threat intelligence
Cyber threat hunting
Security operations center
Security awareness
Risk management
Compliance standards
GDPR
HIPAA
ISO 27001
NIST framework
Penetration testing methodologies
White box testing
Black box testing
Grey box testing
Red teaming
Blue teaming
Purple teaming
Vulnerability management
Patch management
Cybersecurity frameworks
OWASP Top 10
Nmap
Metasploit
Burp Suite
Wireshark
Kali Linux
Backdoor
Rootkit
Trojan horse
Botnet
Ransomware
Phishing email
Spear phishing
Whaling attack
Business email compromise
Identity theft
Password cracking
Brute force attack
Dictionary attack
Rainbow table
Two-factor authentication
Multi-factor authentication
Biometric authentication
Security tokens
Smart cards
Security policies
Access control
Least privilege principle
Defense in depth
Zero trust security
Information assurance
Endpoint security
Network segmentation
Security architecture
Cyber hygiene
Secure coding
Secure development lifecycle
Threat modeling
Security testing
Security audits
Compliance audits
Security controls
Incident handling
Forensic analysis
Chain of custody
Data breach
Data leakage
Data exfiltration
Insider threat
Insider trading
Insider risk
Security incidents
Security breaches
Zero-day vulnerability
Exploit kits
Vulnerability scanning
Vulnerability exploitation
Vulnerability disclosure
Responsible disclosure
Coordinated vulnerability disclosure
Full disclosure
Non-disclosure agreement
Threat actor
Advanced persistent threat
Nation-state cyber attacks
Cyber espionage
Cyber sabotage
Cyber terrorism
Hacktivism
Cyber warfare
Cyber deterrence
Cyber resilience
Cyber insurance
Cyber risk assessment
Cyber risk management
Cyber threat intelligence
Cyber threat assessment
Cyber threat modeling
Cyber threat landscape
Cyber threat hunting
Cybersecurity awareness
Cybersecurity training
Cybersecurity education
Cybersecurity certifications
Certified Ethical Hacker (CEH)
Certified Information Systems Security Professional (CISSP)
CompTIA Security+
Certified Information Security Manager (CISM)
Certified Information Systems Auditor (CISA)
Offensive Security Certified Professional (OSCP)
Certified Cloud Security Professional (CCSP)
Certified Information Privacy Professional (CIPP)
Certified Secure Software Lifecycle Professional (CSSLP)
GIAC Security Essentials (GSEC)
Certified Network Defense Architect (CNDA)
Certified Incident Handler (GCIH)
Certified Intrusion Analyst (GCIA)
Certified Penetration Tester (GPEN)
Certified Web Application Penetration Tester (GWAPT)
Certified Mobile Application Security Tester (GMOB)
Certified Forensic Analyst (GCFA)
Certified Reverse Engineering Analyst (GREM)
Certified Digital Forensics Examiner (CDFE)
Certified Cyber Threat Intelligence Analyst (CCTIA)
Certified Cyber Forensics Professional (CCFP)
Certified Cybersecurity Practitioner (CCP)
Certified Cyber Forensics Professional (CCFP)
Certified Cybersecurity Analyst (CCA)
Certified Cybersecurity Engineer (CCE)
Certified Cybersecurity Architect (CCA)
Certified Cybersecurity Manager (CCM)
Certified Cloud Security Specialist (CCSS)
Certified Network Security Specialist (CNSS)
Certified Application Security Specialist (CASS)
Certified Web Security Specialist (CWSS)
Certified Mobile Security Specialist (CMSS)
Certified Cloud Security Professional (CCSP)
Certified Cyber Defense Professional (CCDP)
Certified Information Systems Risk and Compliance Professional (CISRCP)
Certified Information Security Governance Professional (CISGP)
Certified Information Security Incident Handler (CISIH)
Certified Information Security Operations Professional (CISOP)
Certified Information Security Risk Management Professional (CISRMP)
Certified Information Security Management Systems Lead Auditor (CISMSLA)
Certified Information Security Management Systems Lead Implementer (CISMSLI)
Certified Information Privacy Manager (CIPM)
Certified Information Privacy Technologist (CIPT)
Certified Information Privacy Professional/Europe (CIPP/E)
Certified Information Privacy Professional/United States (CIPP/US)
Certified Information Privacy Professional/Asia (CIPP/A)
Certified Information Privacy Professional/Canada (CIPP/C)
Certified Information Privacy Professional/Information Technology (CIPP/IT)
Certified Information Privacy Professional/Government (CIPP/G)
Certified Information Privacy Professional/Healthcare (CIPP/H)
Certified Information Privacy Professional/Academy (CIPP/A)
Certified Information Privacy Professional/Banking (CIPP/B)
Certified Information Privacy Professional/Management (CIPP/M)
Certified Information Privacy Professional/Public Sector (CIPP/P)
Certified Information Privacy Professional/Private Sector (CIPP/S)
Certified Information Privacy Professional/Privacy Program Management (CIPP/PPM)
Certified Information Privacy Professional/Privacy Technology (CIPP/PT)
Certified Information Privacy Professional/Privacy Law (CIPP/
https://lkxstress.su/
https://lkxstress.su/
https://lkxstress.su/https://lkxstress.su/
https://lkxstress.su/
https://lkxstress.su/
https://lkxstress.su/
https://lkxstress.su/
https://lkxstresse.ru
-
 15:17
15:17
IsaacButterfield
6 hours ago $0.22 earnedAustralia’s Most Hated Politician
4922 -
 4:28
4:28
MudandMunitions
12 hours agoSHOT Show 2026 Is Locked In and I’m a Gundie Nominee!
31 -
 1:19:44
1:19:44
Chad Prather
19 hours agoWhen God Shakes the Room: Bold Faith in a Fearful World
52.7K41 -
 LIVE
LIVE
LFA TV
13 hours agoLIVE & BREAKING NEWS! | FRIDAY 11/21/25
2,715 watching -
 58:40
58:40
Julie Green Ministries
3 hours agoLIVE WITH JULIE
61.7K135 -
 1:01:10
1:01:10
Crypto Power Hour
12 hours ago $2.34 earnedAnimus Bitcoin Technology
20.7K8 -
 2:22:18
2:22:18
Game On!
19 hours ago $2.87 earnedAnother FOOTBALL FRIDAY! Weekend Preview And BEST BETS!
17.9K1 -
 31:55
31:55
ZeeeMedia
20 hours agoHow Gold & Silver Fight Against Digital ID ft. Bill Armour | Daily Pulse Ep 148
23.3K9 -
 13:29
13:29
Clintonjaws
16 hours ago $17.94 earnedCNN Host Stops Show & Plays Surprise Clip Forcing Democrat To Correct Lie
52.6K26 -
 14:55
14:55
World2Briggs
20 hours ago $2.61 earnedThe 10 U.S. Cities Americans Can No Longer Afford — 2025 Edition
20.4K1