Premium Only Content
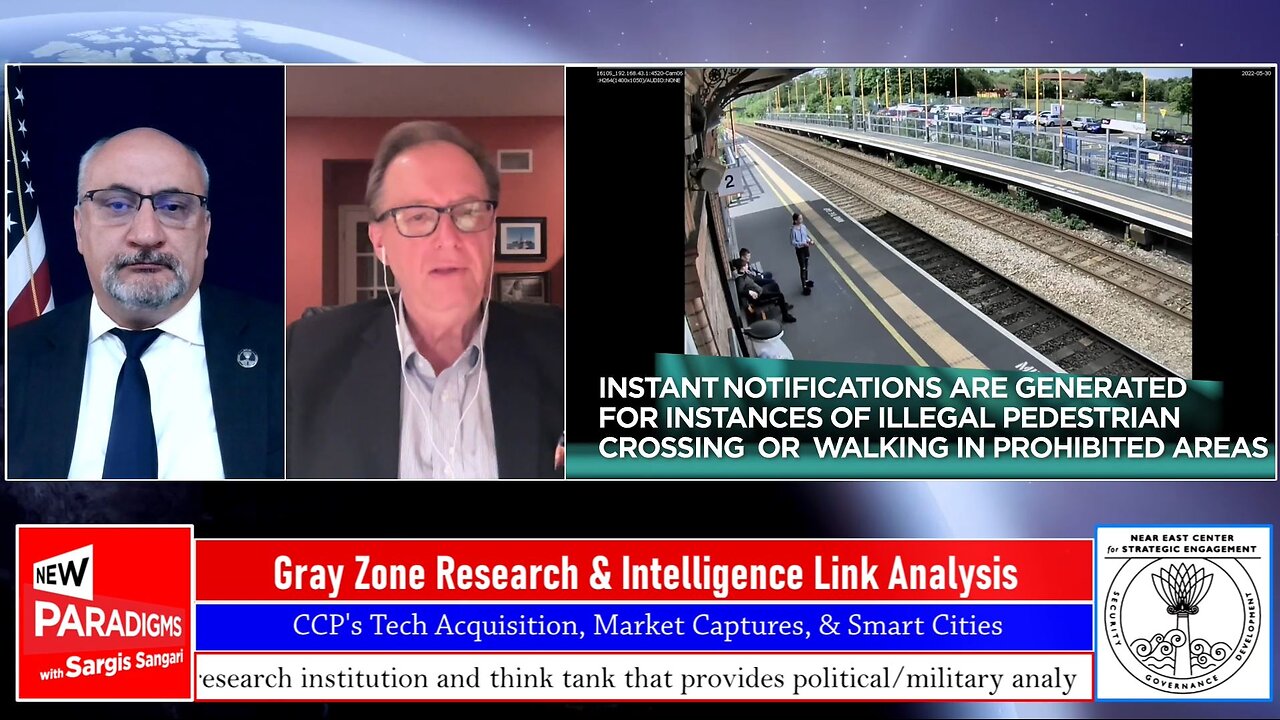
Don Ulsch- NEC-SE Director of China 863, CCP’s “Smart Cities”, New Paradigms w/Sargis Sangari EP 195
On Tuesday, 14 MAY 24, on the 195th episode of New Paradigms with Sargis Sangari, we had the privilege of hearing from Don Ulsch, a renowned figure in the field of China's technological and geopolitical strategies. As the NEC-SE Director of China 863, founder and chief analyst of the China 863 Analyst, a contributing author to SkyTop Media Group, and a U.S. Senate Committee on Foreign Relations Advisor, his insights are highly valued. He founded the China Poll in 2021, which runs weekly on LinkedIn and has amassed some 30,000 followers from hundreds of government and corporate entities worldwide, including inside China. Don and I discussed the Chinese Communist Party's (# CCP) influence on tech acquisitions, market captures, and the future of "Smart Cities."
For China to successfully engage in nation-building, advanced technologies are required because, besides #infrastructure, China will contribute to #eCommerce platforms. This mission is China's 2035 plan: a 13,000 satellite constellation capable of providing Internet-enabling services. These Chinese services will contribute to the local economies of the target nations.
China needs technology to achieve global power. The CCP applies technology to leverage existing markets, uses markets to capture and drive opportunity in developing nations, uses the opportunity to shape geopolitical fusion, uses geopolitical Block-Fusion like the Shanghai Corporation Organization (#SCO) to structure local economies, uses structured economy to build its brand authority, uses brand authority to fuel strategic growth and smart-cities and deploys criminal management systems to target jurisdictions.
China needs to improve its technology innovation. Therefore, they must "acquire" advanced technologies through #cyberespionage, #equity investment, #merger and #acquisition, and international #jointventures. CCP has implemented a massive, widespread collection effort to help narrow the technology innovation gap.
The U.S. should have looked more closely at what China has been doing in the Middle East, particularly the #China-Pakistan Economic Corridor, a $62 billion infrastructure program that includes #telecommunications technology partnering and #spacescience research. In addition, Pakistan is sharing research on defense technology platforms with China.
China's engagement with the Taliban in Afghanistan is a strategic move aimed at ensuring its domestic tranquility. Reports suggest that China has reached an agreement with the Taliban, wherein the latter has agreed not to harbor Islamic jihadists intent on crossing the China-Afghanistan border in western China, home of the Muslim Uyghurs. This agreement, with promises of more power and economic support from China, is a clear example of how China leverages geopolitical alliances to protect its interests and maintain stability.
This process will result in investment in Afghanistan. China is known to take advantage of many opportunities. Also, while the Taliban does exert a certain level of independence, keeping its public distance from #Beijing, China's massive corruption machine, coupled with Afghanistan's lucrative #opioid business, it will ensure that despite any cultural, religious, or other differences the two powers may have, these issues will be resolved through nation-building economics.
China's eCommerce and #BeltandRoad strategy can only succeed with advanced technologies. We could have worked with our allies to diminish the flow of technology intellectual property in its many forms, thereby increasing China's cost of nation-building and constricting its access to the necessary technologies. Over several decades, it would have been possible to address the problem of China's expansion through a combination of remedies.
In 2012 and 2013, Don Ulsch was the Central Intelligence Agency's nation-state cyber security threat advisor. Don is the former co-chairman of the American Bar Association's Privacy Subcommittee and served on several U.S. government cybersecurity and critical infrastructure task forces.
-
![Aug Day #10 of RCP 🤟 [FR/ENG] 🫶 Some Fortnite then Demos then continue on StarRupture 🫶 🤟](https://1a-1791.com/video/fww1/81/s8/1/O/0/c/-/O0c-y.0kob-small-Aug-Day-10-of-RCP-FRENG-Som.jpg) 4:24:45
4:24:45
Deaf Gamer Girl
11 hours agoAug Day #10 of RCP 🤟 [FR/ENG] 🫶 Some Fortnite then Demos then continue on StarRupture 🫶 🤟
48K2 -
 6:59:09
6:59:09
Reidboyy
15 hours ago $11.55 earnedBattlefield 6 #1 POV (Watch and Learn)
87.3K3 -
 2:25:42
2:25:42
TheSaltyCracker
10 hours agoThey So Mad ReEEeStream 8-10-25
124K273 -
 2:27:39
2:27:39
vivafrei
18 hours agoEp. 276: Epstein Subpoenas &Trump E.O! Bondi Offers Reward for Maduro Arrest? MADNESS IN CANADA!
145K137 -
 2:23:55
2:23:55
Barry Cunningham
13 hours agoPRESIDENT TRUMP IS NOT PLAYING AROUND...AND THE LIBNUTS CAN'T STOP HIM!
100K64 -
 22:02
22:02
Stephen Gardner
19 hours ago🔥JUST IN: Trump BETRAYAL plot EXPOSED!
121K306 -
 38:32
38:32
The Why Files
21 days agoThe Real CIA Vol. 1: 693 Pages of Secret Crimes
130K60 -
 49:12
49:12
MattMorseTV
16 hours ago $22.72 earned🔴Zelenskyy is NOT HAPPY about Trump’s NEW DEAL.🔴
128K158 -
 1:03:49
1:03:49
Warren Smith - Secret Scholar Society
4 days ago"You are on the brink" - My Conversation with Nick Fuentes
91.5K64 -
 8:05
8:05
Tactical Advisor
17 hours agoNEW Best Budget AR15 | PSA Guardsman (FIRST LOOK)
84K29