Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
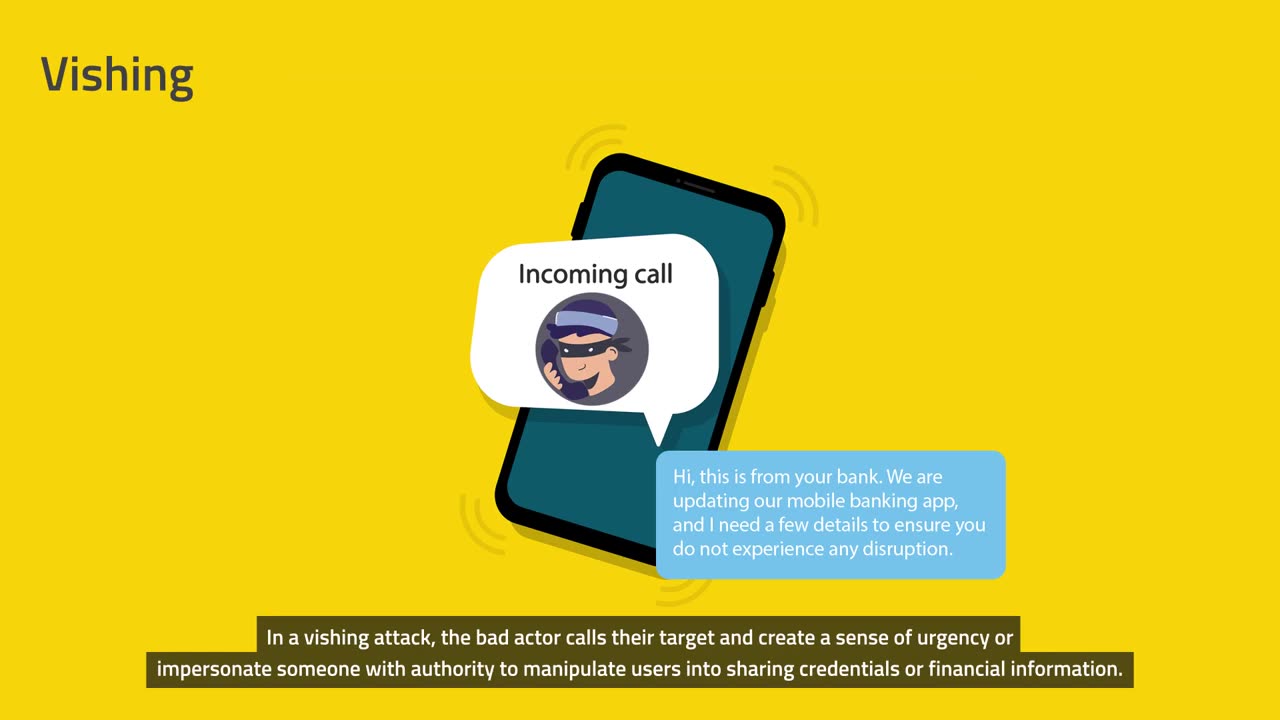
Techniques used by the hacker | cybersecurity awareness
1 year ago
9
This video provides essential aspects about Phishing, Vishing, and SMiShing including,
• What is Phishing?
• What is SMiShing?
• What is Vishing?
• Phishing indicators
Loading comments...
-
 1:27:11
1:27:11
Omar Elattar
9 hours agoThe Dating Expert: "I've Helped 4,000 Men Find LOVE!" - The #1 Alpha Trait Women Secretly Crave!
9.41K -
 LIVE
LIVE
VOPUSARADIO
9 hours agoPOLITI-SHOCK! "END THE FED, END THE LIES & END THE DEEP STATE ONCE AND FOR ALL"!
163 watching -
 1:43:38
1:43:38
LumpyPotatoX2
4 hours agoRumble Creator Round-Table - Let's Talk About It
14.4K2 -
 32:38
32:38
The Mel K Show
7 hours agoMel K & Dr. James Thorp, MD | Sacrifice: The Targeting of the Most Vulnerable | 7-24-25
21.1K10 -
 1:12:41
1:12:41
Donald Trump Jr.
6 hours agoFrom Crypto to AI, There's a New American Energy Revival, Interviews with Asher Genoot & Sen McCormick | TRIGGERED Ep.261
148K53 -
 52:11
52:11
ZeeeMedia
9 hours ago"Meaningful Deep State Prosecution" ft. Robert Barnes | Daily Pulse Ep. 73
32.2K8 -
 8:10
8:10
MattMorseTV
6 hours ago $2.48 earnedThey just CAVED.
23.8K24 -
 14:55
14:55
Tundra Tactical
6 hours ago $0.44 earnedTundra's EXPLOSIVE SIG Meme Review
11.4K1 -
 3:01:22
3:01:22
Joker Effect
3 hours agoThe told me to go to H3LL...... well... I am here and causing chaos now. HORROR GAMEPLAY ONLY! :)
13.6K5 -
 LIVE
LIVE
Mally_Mouse
5 hours agoLet's Hang!! --10K Follower Celebration!!!
61 watching