Premium Only Content
Augmented Cyber Warrior & Trust Community (TC) Operator Kit
CYVA Research is a cybersecurity innovation, strategic research and development firm. Our focus is developing disruptive cybersecurity, privacy and liberty technologies and strategies for our clients. CYVA’s internationally patented Self-Determining Digital Persona™ (SDDP™) technology is an owner-operator controlled, intelligent (AI/MI), self-protecting, self-governing, self-monetizing mobile identity agent (HW/SW). The SDDP™ provides, augments people and communities with the capabilities to protect, control and monetize their identity and information assets wherever they exist post-decryption. We call this Human Digital Liberty™. These capabilities are the foundation in forwarding disruptive innovate approaches to the challenges of security, privacy, and liberty in our presently hostile cyberspace.
It is critical our SOF warriors have the capabilities to protect and control their identities and information assets e.g., pictures, messages, target data, geo-location, identity attributes wherever they exist post-decryption across hostile environments and distributed domains (JADC2). Cyberspace is a domain of war. Our warriors and their families have long been priority targets for our enemies who have skillfully exploited our fundamentally flawed data fabric, our presently, by big tech design, primitive-weak dumb data objects.
Augmented Cyber Warrior™: operator tools to conduct irregular cyber warfare, HUMINT, C5ISR and strategically counter enemy unrestricted hybrid warfare.
CYVA’s Augmented Cyber Warrior™ and TC Operator Kit™ capabilities include the formation and management of ad hoc compartmental smartphone-based Trust Communities (TCs) of human and machine entities (IoT) to provide an asymmetric advantage for SOF operators engaged in irregular cyber warfare, ISR, HUMINT, information operations and supporting, working with resistance fighters.
Security Rule #1: Trust No One
Especially do not trust anyone or entity that does not respect the right of people to protect and control their personal information wherever it exists, does not respect, and support the U.S. Constitution, Bill of Rights, and a strong military.
Our Escalating Cybersecurity Catastrophe is Entirely Manmade
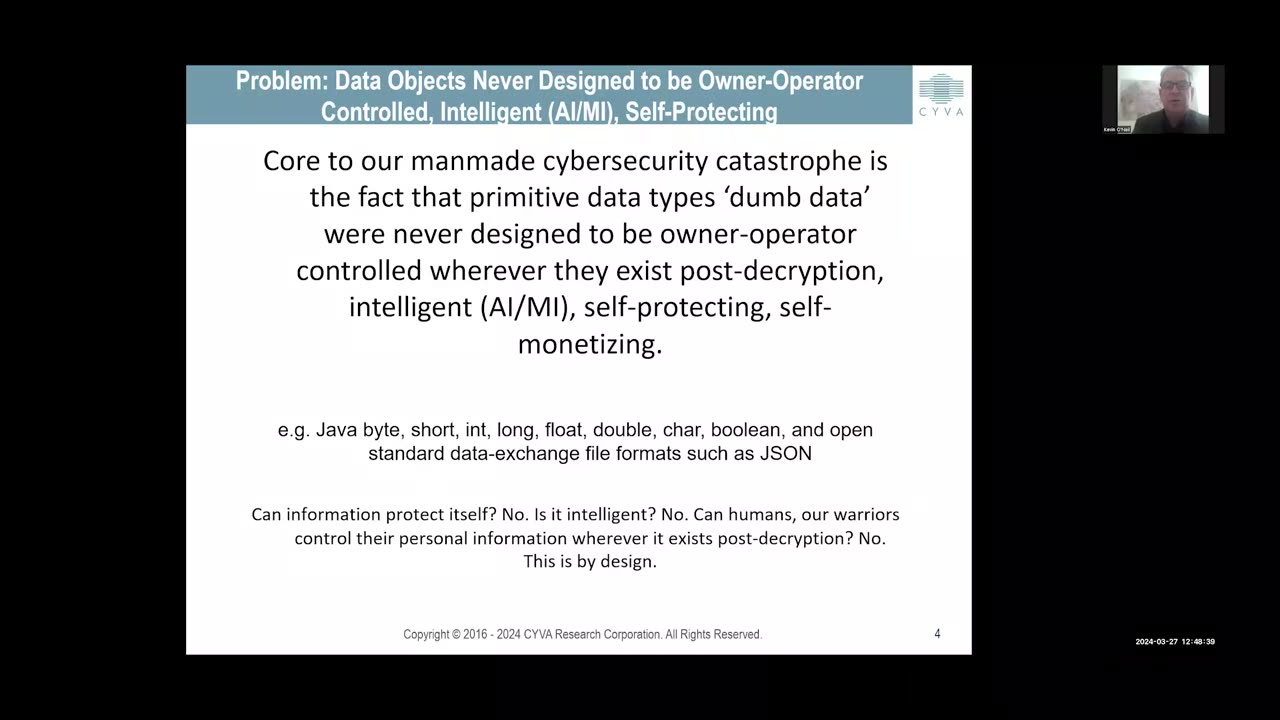
No end in sight to cyber-attacks and data breaches with devastating impact . Why? At the core of this unending catastrophe is data. Our data is weak, vulnerable, easy prey. This is by design . Data can be used for us (good) and against us (evil). We presently have little if any control over the mass collection and exploitation of our, by design primitive-weak dumb data, our human digital existence.
-
 13:52
13:52
Comedy Dynamics
1 day agoSam Tallent Roasting the Audience
44.5K2 -
 16:28
16:28
Nikko Ortiz
16 hours agoPainful Fails That HURT To Watch...
38.7K9 -
 9:40
9:40
MattMorseTV
15 hours ago $17.13 earnedAbsolutely NO ONE saw this coming…
21.8K74 -
 2:04:53
2:04:53
Side Scrollers Podcast
20 hours agoHasan Piker Goes FULL Propaganda + Kirsche & Craig Make “The List” + More | Side Scrollers
51.8K7 -
 17:59
17:59
GritsGG
15 hours ago15 Win Streak on Warzone! Journey to 4000 Wins!
13.9K -
 7:40
7:40
Blabbering Collector
2 days agoLEAKED: Draco Malfoy, Hooch, Neville Longbottom! | Harry Potter HBO Show Update, Wizarding News
48.7K4 -
 LIVE
LIVE
Lofi Girl
3 years agolofi hip hop radio 📚 - beats to relax/study to
306 watching -
 2:28:53
2:28:53
Inverted World Live
11 hours agoMurder Tourism, Truth Police, & ChatGPT Weddings | Ep. 141
258K18 -
 2:58:44
2:58:44
TimcastIRL
11 hours agoTrump DOJ Opens Probe Into Democrat Swalwell For Mortgage Fraud | Timcast IRL
230K167 -
 2:51:50
2:51:50
Laura Loomer
10 hours agoEP156: Trump Sounds The Alarm On The Nigerian Christian Genocide
81.9K80