Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
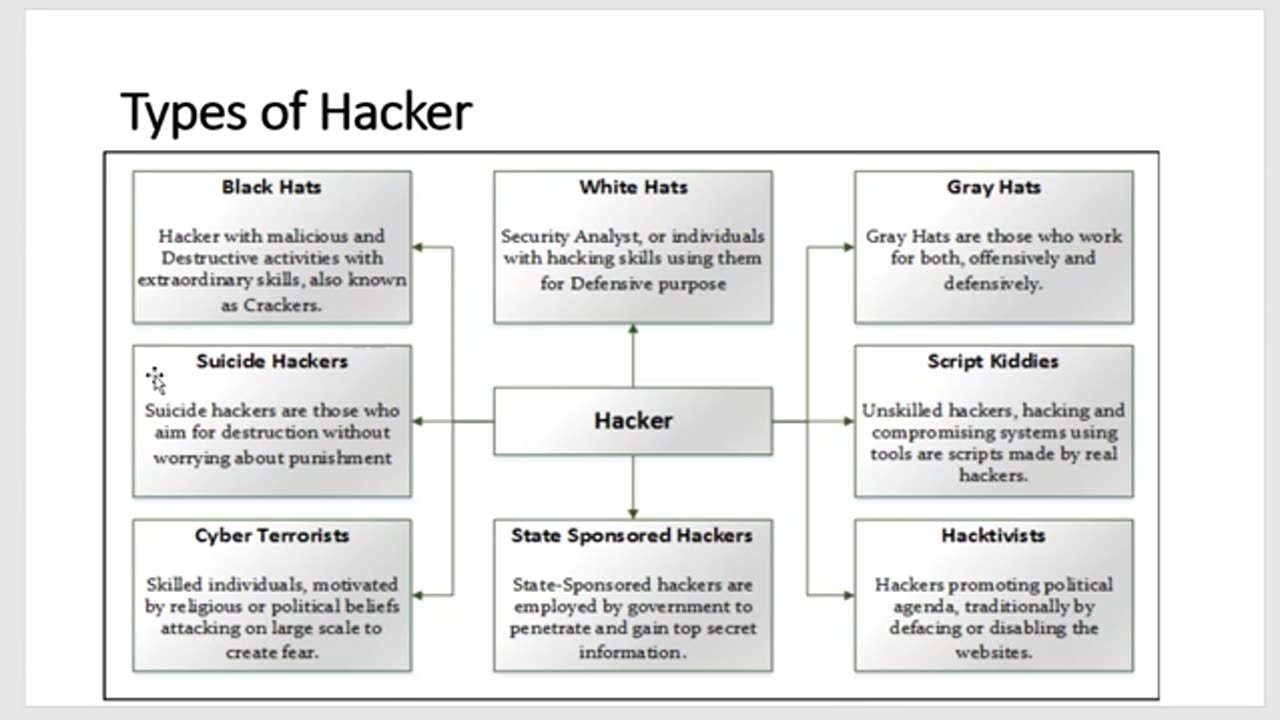
Ethical Hacking part-1
1 year ago
41
It's only for you learn ethical hacking conseps don't use this skill to unbetter thinking
Loading 1 comment...
-
 LIVE
LIVE
ttvglamourx
5 hours ago $0.26 earnedPLAYING WITH VIEWERS !DISCORD
78 watching -
 LIVE
LIVE
TheManaLord Plays
7 hours agoMANA SUMMIT - DAY 2 ($10,200+) | BANNED PLAYER SMASH MELEE INVITATIONAL
194 watching -
 LIVE
LIVE
Jorba4
2 hours ago🔴Live-Jorba4- The Finals
78 watching -
 LIVE
LIVE
BBQPenguin_
2 hours agoSOLO Extraction. Looting & PVP
32 watching -
 1:57:14
1:57:14
vivafrei
19 hours agoEp. 280: RFK Jr. Senate Hearing! Activist Fed Judges! Epstein Victims DEBACLE! & MORE! Viva & Barnes
72.9K78 -
 LIVE
LIVE
GritsGG
3 hours agoTop 250 Ranked Grind! Dubulars!🫡
114 watching -
 5:31
5:31
WhaddoYouMeme
1 day ago $3.35 earned$8,000/hr Dating Coach Loses Everything (Sadia Kahn)
20.2K8 -
 LIVE
LIVE
Ouhel
5 hours agoSunday | CoD 4 | CAMPAIGN PLAYTHROUGH | Nostalgia Kick
58 watching -
 13:14
13:14
DEADBUGsays
1 day agoThe Murder of Veronica Kaye | Cold#11
16.9K4 -
 14:53
14:53
Adam Does Movies
20 hours ago $1.55 earnedIs There Any Saving Jurassic World?
15.2K2