Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
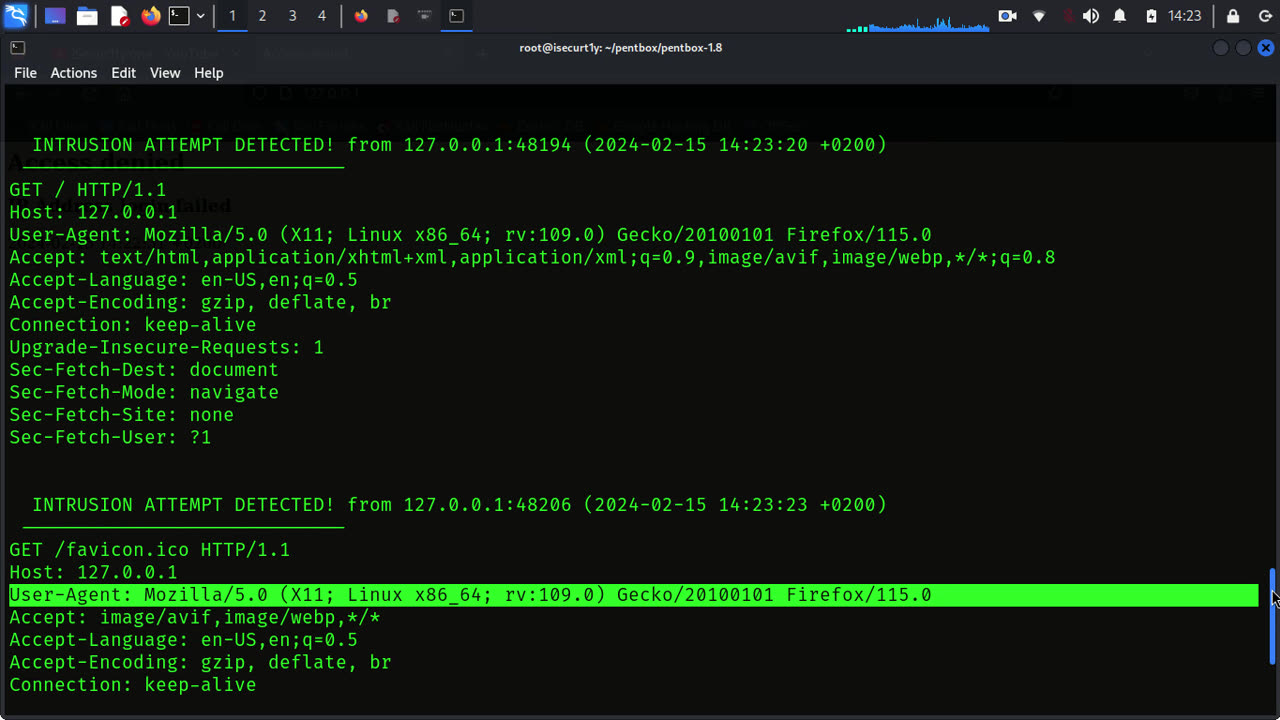
Catching Hackers with Honeypots: What is a Honeypot?
1 year ago
69
The answer is, “sometimes.” While the honeypot may appear to be a legitimately unprotected source of data to some, highly experienced hackers may be able to tell the difference between a legitimate vulnerable system and a honeypot, in what is known as “fingerprinting.” Once a honeypot is fingerprinted, a hacker
Loading comments...
-
 2:56:28
2:56:28
IsaiahLCarter
17 hours ago $9.00 earnedThe Tri-State Commission, Election Weekend Edition || APOSTATE RADIO 033 (Guest: Adam B. Coleman)
45.7K6 -
 15:03
15:03
Demons Row
12 hours ago $12.46 earnedThings Real 1%ers Never Do! 💀🏍️
61.7K22 -
 35:27
35:27
megimu32
16 hours agoMEGI + PEPPY LIVE FROM DREAMHACK!
181K15 -
 1:03:23
1:03:23
Tactical Advisor
19 hours agoNew Gun Unboxing | Vault Room Live Stream 044
266K41 -
 19:12
19:12
Robbi On The Record
20 hours ago $23.21 earnedThe Loneliness Epidemic: AN INVESTIGATION
96.1K109 -
 14:45
14:45
Mrgunsngear
1 day ago $151.02 earnedFletcher Rifle Works Texas Flood 30 Caliber 3D Printed Titanium Suppressor Test & Review
155K35 -
 17:17
17:17
Lady Decade
1 day ago $12.51 earnedMortal Kombat Legacy Kollection is Causing Outrage
101K24 -
 35:51
35:51
Athlete & Artist Show
1 day ago $14.16 earnedIs Ryan Smith The Best Owner In The NHL?
106K17 -
 22:56
22:56
American Thought Leaders
2 days agoCharles Murray: I Thought Religion Was Irrelevant to Me. I Was Wrong.
86.1K64 -
 36:22
36:22
Brad Owen Poker
21 hours agoGIGANTIC $17,000+ Pot In BOBBY’S ROOM! TRAPPING Top Pro w/FULL HOUSE!! Big Win! Poker Vlog Ep 326
87.7K16