Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
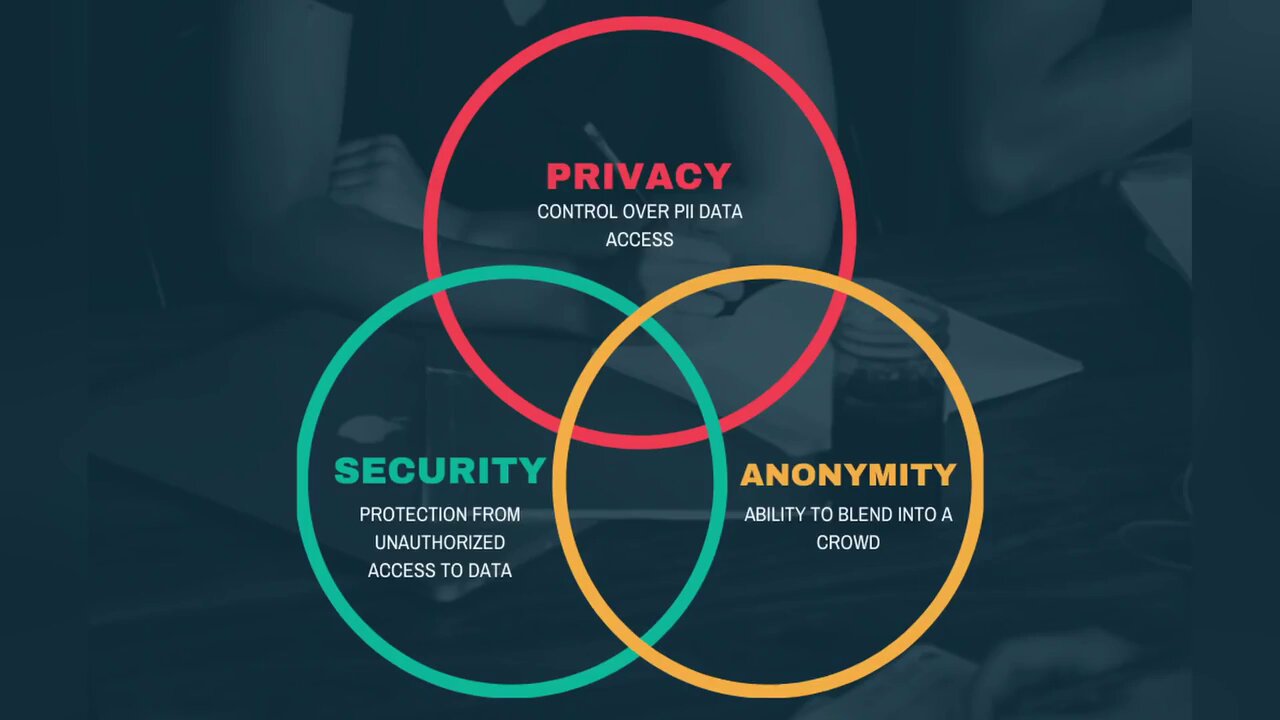
How To Properly Threat Model
1 year ago
14
Credit to Techlore for making this video:
https://odysee.com/@techlore:3/threat-modeling-101-the-video-i-wish-i:e
Loading comments...
-
 1:02:31
1:02:31
Timcast
3 hours agoTrump Raises TARIFF On China To 145% , China PANICS As Trump Isolates Nation, Market STILL In Chaos
199K137 -
 27:43
27:43
Standpoint with Gabe Groisman
2 days agoWill Trump Tariffs Cause A Recession?
42 -
 52:23
52:23
Sean Unpaved
3 hours agoGreen Jackets & Hardwood: Masters Tournament Tee-Off, Jokic on Malone, Luka's Big Night In Dallas
35.6K2 -
 2:00:26
2:00:26
The Charlie Kirk Show
3 hours agoBetter Know Your Bonds + Decoupling China | Cardone, Ganz, Sedra | 4.10.25
82.3K15 -
 2:13:54
2:13:54
Steven Crowder
6 hours ago🔴 How Trump's Massive Tariff Announcement Destroyed China & the Left
441K249 -
 1:06:18
1:06:18
Ben Shapiro
3 hours agoEp. 2177 - TRUMP U-TURN WIN: Tariff War Paused, China Isolated!
30.9K25 -
 44:14
44:14
The Rubin Report
4 hours agoLiberals Saddened as AOC’s Hypocrisy to ‘Fight Oligarchy’ Is Exposed
112K49 -
 1:28:51
1:28:51
Rebel News
2 hours ago $2.13 earnedEzra at Poilievre's rally, Carney's links to China, Libs target legal gun owners | Rebel Roundup
27.5K8 -
 1:03:45
1:03:45
TheAlecLaceShow
4 hours agoGuests: Alex Marlow & Braeden Sorbo | Trump Hits China with 125% Tariffs | The Alec Lace Show
14.1K -
 57:31
57:31
The Tom Renz Show
2 hours agoRFK & MAHA, the House is Doing Something, & Robots for Mars!
17.4K1