Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
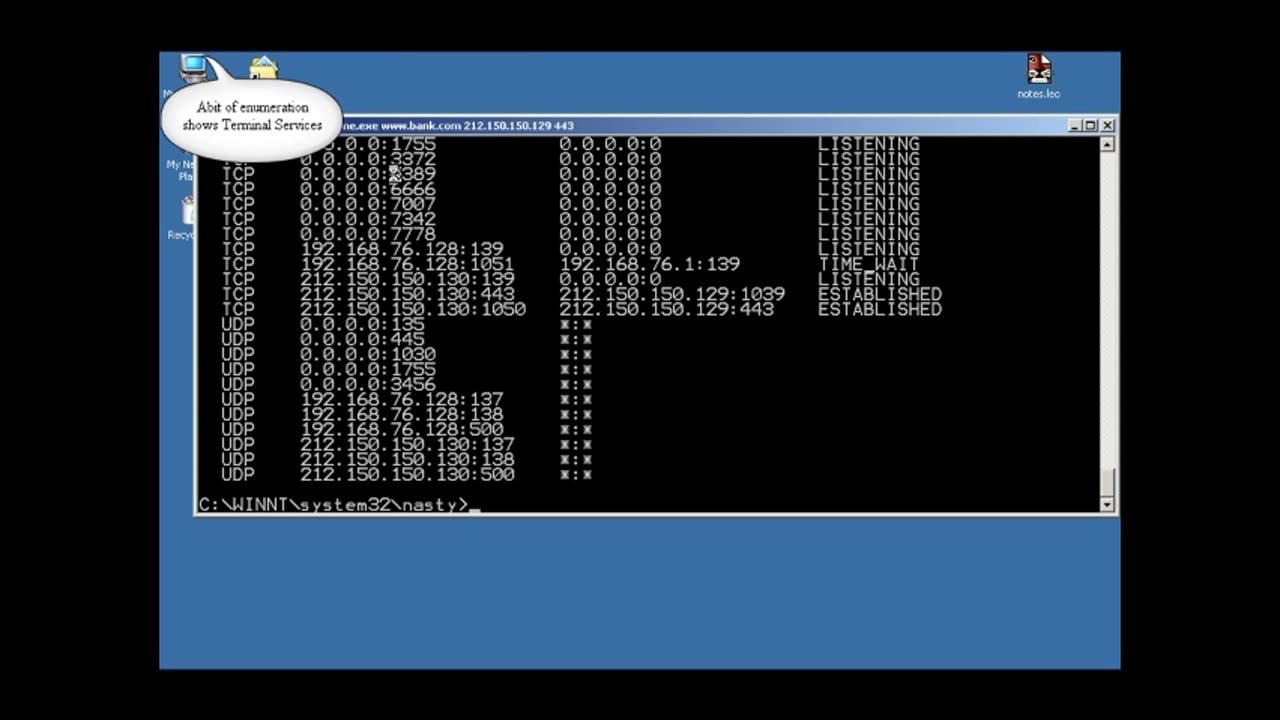
A Penetration Attack Reconstructed
Loading comments...
-
 1:37:52
1:37:52
Glenn Greenwald
6 hours agoInternational Rage—From EU To Brazil—Over Zuckerberg’s Vow To End Censorship; Lee Fang On Financial Interests Behind H1B & LA Mayor Skipping Town | SYSTEM UPDATE #386
52.2K36 -
 LIVE
LIVE
Flyover Conservatives
20 hours agoInauguration Danger: Is Trump Walking Into a Trap? - Sheriff Richard Mack | FOC Show
731 watching -
 LIVE
LIVE
Precision Rifle Network
1 day agoS4E1 - Guns & Grub - Back like a bad rash!
69 watching -
 1:11:22
1:11:22
Common Threads
4 hours ago $2.04 earnedLIVE DEBATE: Trump Pushes U.S. Expansion, Cali Fires Spark Political Outrage
21K6 -
 54:46
54:46
LFA TV
8 hours agoThe LA Apocalypse | TRUMPET DAILY 1.9.25 7pm
21.1K10 -
 57:50
57:50
theDaily302
13 hours agoThe Daily 302-CORY GAUTEREAUX
26.5K -
 9:49
9:49
Tundra Tactical
3 hours ago $1.58 earnedISIS ATTACK Screams Incompetence.
24.5K3 -
 47:51
47:51
Anthony Pompliano
1 day ago $7.72 earnedRegulators Tried To End Bitcoin?!
60.5K7 -
 LIVE
LIVE
BSparksGaming
8 hours agoMarvel Rivals Season 1 is ALMOST HERE! Time to Grind!
391 watching -
 45:26
45:26
Kimberly Guilfoyle
6 hours agoBreaking News Coverage of LA Fires, Live with Asm Bill Essayli & Jennifer Kelly | Ep. 187
53.1K66