Premium Only Content
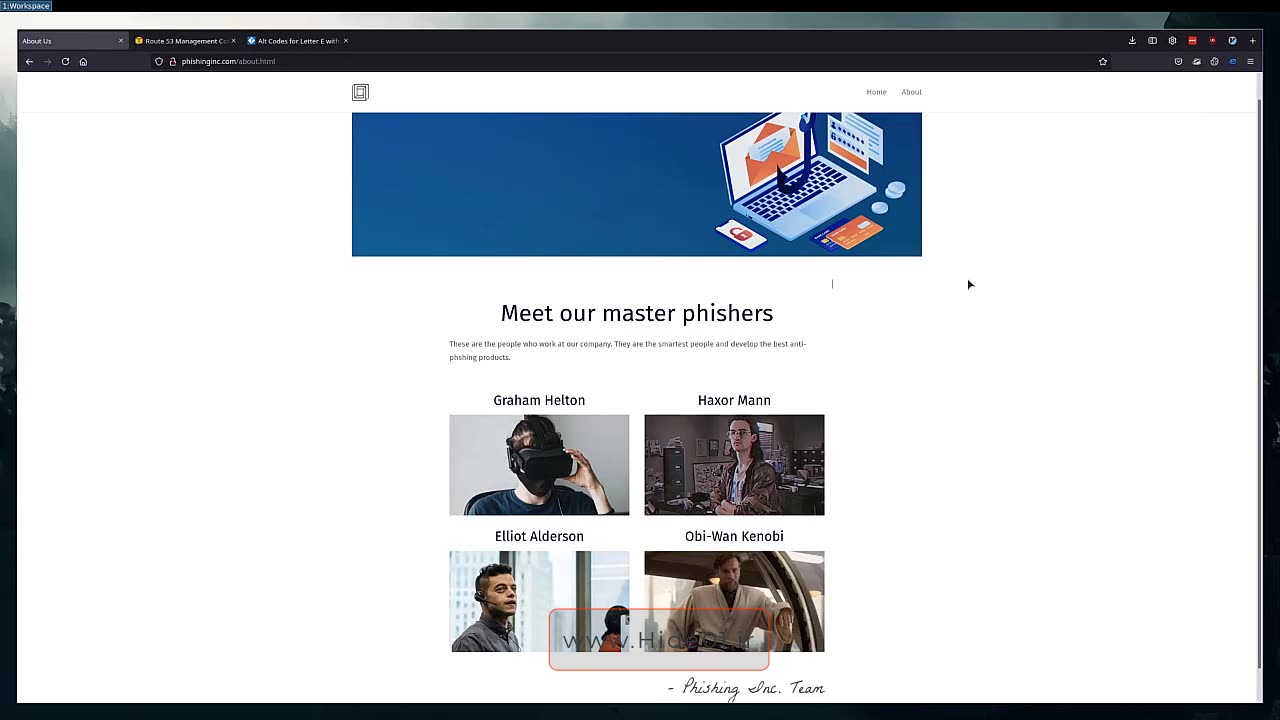
Part 2: Researching Your Target
In the second part of the practical assessment for the Phishing Assessment Course, participants delve into the critical phase of "Researching Your Target." This essential component of the course focuses on developing the skills and knowledge required to gather in-depth information about potential targets for phishing attacks.
During this phase, participants will learn how to:
Identify Target Personas: Understand the importance of profiling potential victims by their roles, responsibilities, and online presence. Recognize the significance of tailoring phishing campaigns to specific personas.
Gather Personal Information: Explore various open-source intelligence (OSINT) techniques and tools to collect data about the target, such as email addresses, social media profiles, job titles, and more.
Assess Digital Footprints: Analyze online footprints left by the target to uncover potential vulnerabilities and entry points for phishing attacks.
Social Engineering: Explore the art of social engineering and its application in crafting convincing phishing messages tailored to the target's interests, affiliations, or behaviors.
Ethical Considerations: Emphasize the importance of ethical behavior and respect for privacy laws and regulations while conducting research and crafting phishing campaigns.
By the end of Part 2, participants will have acquired the knowledge and skills necessary to comprehensively research and understand their potential phishing targets, enabling them to create more convincing and targeted phishing simulations in subsequent stages of the course. This phase ensures that ethical hackers and cybersecurity professionals are well-prepared to assess and strengthen an organization's defenses against phishing threats.
#PhishingAssessment
#CybersecurityTraining
#EthicalHacking
#InformationSecurity
#PhishingSimulation
#OnlinePrivacy
#CyberThreats
#OSINT
#SocialEngineering
#DigitalFootprint
#TargetedPhishing
#SecurityAwareness
#CyberDefense
#PhishingAwareness
#InfoSecEducation
#EthicalHacker
#CyberRisk
#DataProtection
#SecurityTraining
#CyberSkills
-
 1:05:42
1:05:42
Dear America
2 hours agoShould Christians Celebrate Halloween?
5.07K3 -
 2:03:24
2:03:24
The Culture War with Tim Pool
3 hours agoAntifa Is A Terror Organization, Crackdown Coming As Leftists Defend Violence | The Culture War
134K118 -
 28:39
28:39
Afshin Rattansi's Going Underground
5 days agoThe Trump Plan to Save US Economic Hegemony You Haven’t Heard Of (Jim Rickards)
6.8K2 -
 LIVE
LIVE
Lara Logan
15 hours agoROSEANNE UNLEASHED: Bolder Than Ever, Plus an Exclusive Peak at Her New Show | Roseanne Barr | Ep 39
535 watching -
 1:14:27
1:14:27
Steven Crowder
4 hours agoTrump Gets Screwed out of Nobel Prize - And They're Actually Thrilled About It
187K263 -
 46:24
46:24
The Rubin Report
3 hours agoListen to Dem Stutter as He’s Forced to Admit Trump Did the Impossible
34.5K19 -
 17:13
17:13
Neil McCoy-Ward
1 hour ago🚨 NATO Just Announced WHAT?!
2.3K9 -
 LIVE
LIVE
The Shannon Joy Show
3 hours agoCountdown To SJ Live - Hey Fam Town Hall 12pm ET LIVE! Tune In HERE
39 watching -
 1:36:51
1:36:51
The Mel K Show
2 hours agoMORNINGS WITH MEL K -Grand Conspiracy Against the People of the United States Unfolds 10-10-25
16.9K6 -
 1:02:15
1:02:15
Dr. Eric Berg
4 days agoThe Dr. Berg Show LIVE October 10, 2025
26.3K9