Premium Only Content
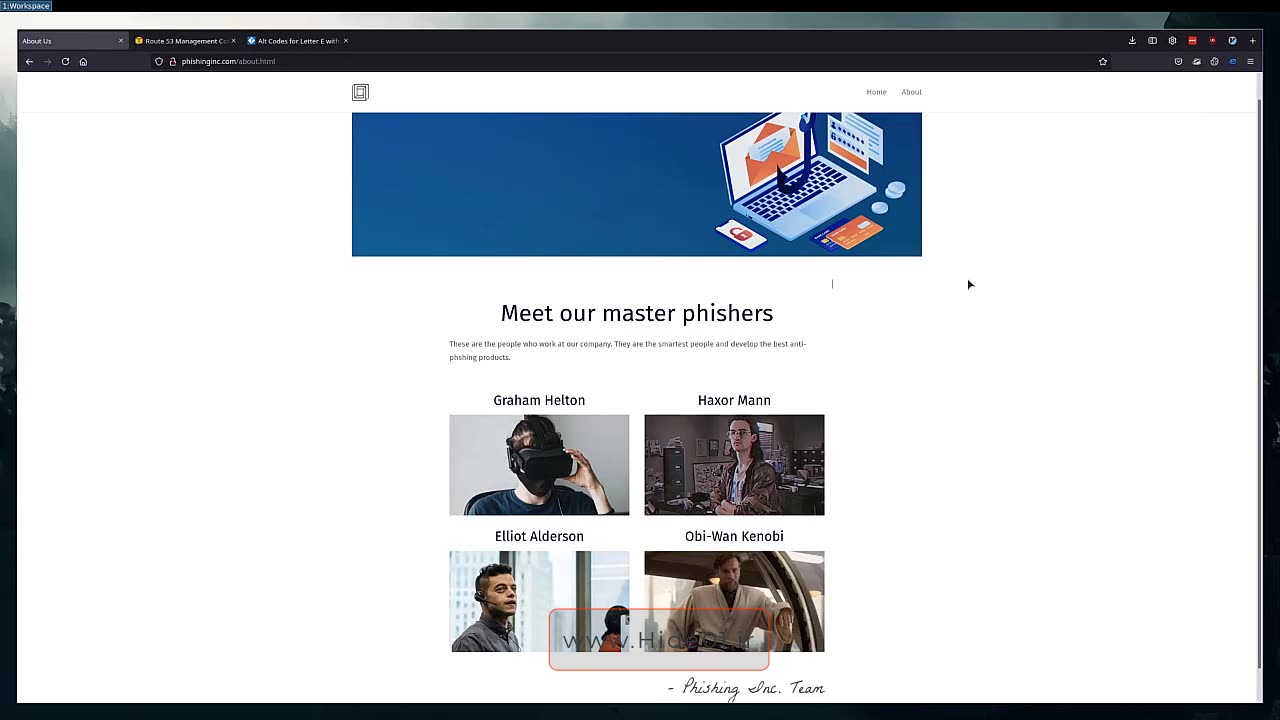
Part 2: Researching Your Target
In the second part of the practical assessment for the Phishing Assessment Course, participants delve into the critical phase of "Researching Your Target." This essential component of the course focuses on developing the skills and knowledge required to gather in-depth information about potential targets for phishing attacks.
During this phase, participants will learn how to:
Identify Target Personas: Understand the importance of profiling potential victims by their roles, responsibilities, and online presence. Recognize the significance of tailoring phishing campaigns to specific personas.
Gather Personal Information: Explore various open-source intelligence (OSINT) techniques and tools to collect data about the target, such as email addresses, social media profiles, job titles, and more.
Assess Digital Footprints: Analyze online footprints left by the target to uncover potential vulnerabilities and entry points for phishing attacks.
Social Engineering: Explore the art of social engineering and its application in crafting convincing phishing messages tailored to the target's interests, affiliations, or behaviors.
Ethical Considerations: Emphasize the importance of ethical behavior and respect for privacy laws and regulations while conducting research and crafting phishing campaigns.
By the end of Part 2, participants will have acquired the knowledge and skills necessary to comprehensively research and understand their potential phishing targets, enabling them to create more convincing and targeted phishing simulations in subsequent stages of the course. This phase ensures that ethical hackers and cybersecurity professionals are well-prepared to assess and strengthen an organization's defenses against phishing threats.
#PhishingAssessment
#CybersecurityTraining
#EthicalHacking
#InformationSecurity
#PhishingSimulation
#OnlinePrivacy
#CyberThreats
#OSINT
#SocialEngineering
#DigitalFootprint
#TargetedPhishing
#SecurityAwareness
#CyberDefense
#PhishingAwareness
#InfoSecEducation
#EthicalHacker
#CyberRisk
#DataProtection
#SecurityTraining
#CyberSkills
-
 3:10:46
3:10:46
Ellie_roe
7 hours agoEllie and Errys Halloween Spooktacular || Random Horror Games
24.2K1 -
 50:27
50:27
Sarah Westall
9 hours agoBig Banks Caught Rigging Market, IMF tells World to “Buckle Up” w/ Andy Schectman
43.6K17 -
 13:54
13:54
Degenerate Jay
16 hours ago $1.15 earned5 Best Superhero Movies To Watch On Halloween
22.9K5 -
 59:03
59:03
NAG Podcast
9 hours agoSarah Fields: BOLDTALK W/Angela Belcamino
39.4K9 -
 1:21:41
1:21:41
Glenn Greenwald
11 hours agoGlenn Takes Your Questions: On the Argentina Bailout, Money in Politics, and More; Plus: Journalist Jasper Nathaniel on Brutality and Settler Attacks in the West Bank | SYSTEM UPDATE #541
92K47 -
 3:10:08
3:10:08
Barry Cunningham
9 hours agoPRESIDENT TRUMP TO USE NUCLEAR OPTION? FOOD STAMPS END! | SHUTDOWN DAY 31
55.6K45 -
 1:06:56
1:06:56
BonginoReport
17 hours agoThe Battle Between Good & Evil w/ Demonologist Rick Hansen - Hayley Caronia (Ep.168)
105K39 -
 1:12:57
1:12:57
Kim Iversen
11 hours agoBill Gates Suddenly Says “Don’t Worry About Climate Change”?
94.1K67 -
 1:05:12
1:05:12
Michael Franzese
11 hours agoI Waited 50 Years to Tell You What Happened on Halloween 1975
47.6K20 -
 1:07:15
1:07:15
Candace Show Podcast
11 hours agoINFILTRATION: Charlie Kirk Was Being Tracked For Years. | Candace Ep 256
97.6K415