Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
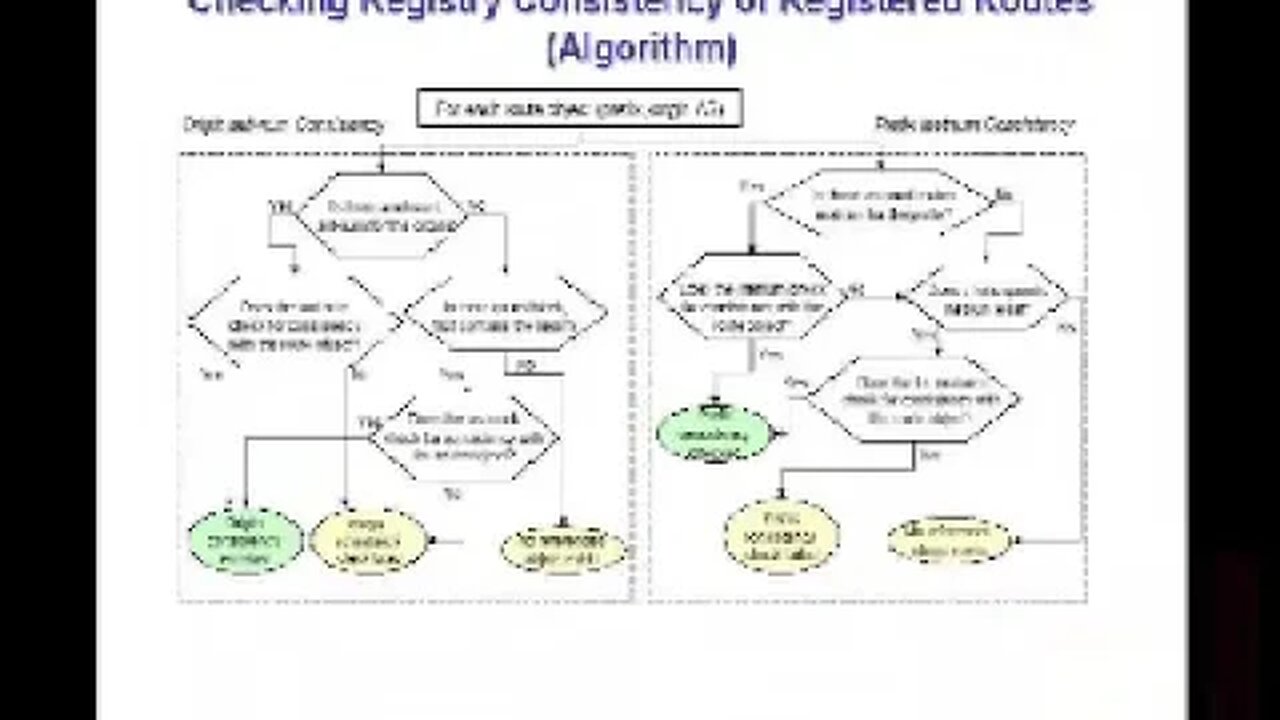
A Comparative Analysis of BGP Anomaly Detection and Robustness Algorithms
Loading comments...
-
 LIVE
LIVE
SpartakusLIVE
11 hours agoTOXIC Solos on ARC Raiders || Friday Night HYPE - WZ or Redsec Later?
413 watching -
 2:15:42
2:15:42
TheSaltyCracker
4 hours agoWoke is DEAD ReeEEStream 11-07-25
68.2K152 -
 1:29:13
1:29:13
Sarah Westall
3 hours agoThe City of London: Infiltration, Intimidation & Centralized Power w/ Mike Harris
10.9K7 -
 10:14:18
10:14:18
Dr Disrespect
13 hours ago🔴LIVE - DR DISRESPECT - ARC RAIDERS - AGAINST ALL DANGER
163K24 -
 32:09
32:09
ThisIsDeLaCruz
1 day ago $0.01 earnedFalling In Reverse: Christian Thompson’s Stage Tech Revealed
17.1K2 -
 LIVE
LIVE
SynthTrax & DJ Cheezus Livestreams
1 day agoFriday Night Synthwave 80s 90s Electronica and more DJ MIX Livestream 80s Night / Late Night Nostalgia
377 watching -
 4:05:52
4:05:52
Nerdrotic
8 hours ago $0.18 earnedHollywood REGRET | Disney's Predator | The Feminist Avengers - Friday Night Tights 379
45.9K15 -
 2:36:22
2:36:22
Mally_Mouse
4 days agoFriend Friday!! 🎉 - Let's Play! - MIMESIS
14.4K2 -
 41:20
41:20
MattMorseTV
5 hours ago $0.39 earned🔴Schumer just BACKSTABBED his OWN VOTERS. 🔴
26.2K56 -
 3:33:34
3:33:34
MissesMaam
5 hours ago*Spicy* Friend Friday with Mally_Mouse!! 💚✨
6.91K3