Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
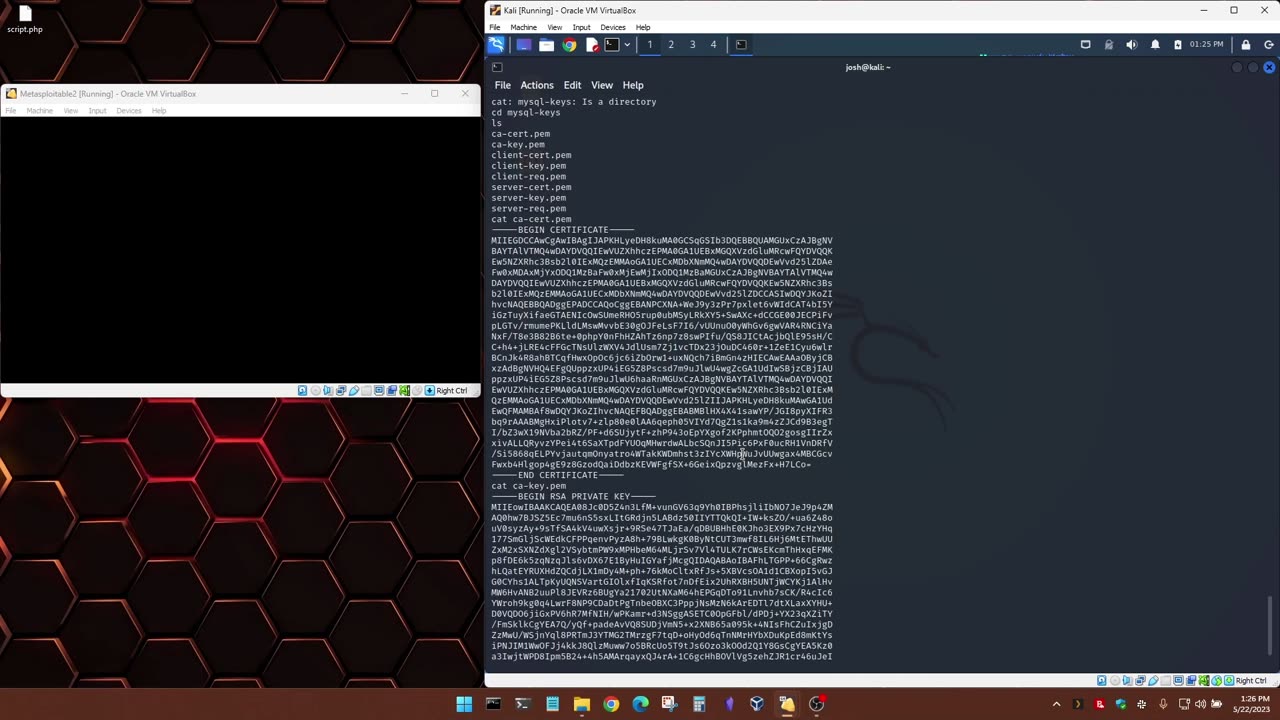
Using nmap and Metasploit
Loading comments...
-
 LIVE
LIVE
BonginoReport
1 hour agoCornhusker Clink & A Sizzling Border Wall Deter Illegals - Nightly Scroll w/ Hayley Caronia (Ep.116)
12,359 watching -
 LIVE
LIVE
Dr Disrespect
7 hours ago🔴LIVE - DR DISRESPECT - IMPOSSIBLE 5 CHICKEN DINNER CHALLENGE - FEAT. VISS
1,221 watching -
 LIVE
LIVE
The Jimmy Dore Show
42 minutes agoTrump Administration Sends Accused Pedo BACK TO ISRAEL! Ukrainians Now OVERWHELMINGLY Oppose War!
4,662 watching -
 DVR
DVR
TheCrucible
2 hours agoThe Extravaganza! Ep. 24 (8/20/25)
14.3K1 -
 1:18:42
1:18:42
Kim Iversen
2 hours agoUFO Base Area 51 Catches Fire… Is It a Massive Cover-Up?!
5.04K29 -
 1:51:18
1:51:18
Redacted News
2 hours ago"There will be consequences!!!" Trump issues big threat to Putin ahead of peace summit | Redacted
84.7K43 -
 53:14
53:14
Candace Show Podcast
2 hours agoThe MOST MORAL Blackmail In The World | Candace EP 231
18.8K80 -
 1:11:28
1:11:28
vivafrei
4 hours agoMatt Taibbi Getting "Westfalled"? Kathy Hochul Fighting for Illegals! Mamdani Minority Report & MORE
70K30 -
 2:03:39
2:03:39
Pop Culture Crisis
4 hours agoWTF Happened to Miley Cyrus? HARRY POTTER Set Images, Sydney Sweeney Hater EXPOSED | Ep. 901
18.4K18 -
 10:17
10:17
MattMorseTV
4 hours ago $5.37 earnedTrump's DOJ just DROPPED a NUKE.
23.8K33