Windows 11 Remote Security-Testing/Fuzzing
Windows 11 Remote Security-Testing/Reverse-Engineering
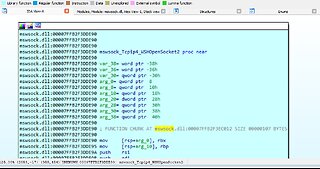
I Injected A Spoofed Crafted Packet That I Programmed Myself To Sent Remotely Over The Network Into The Remote Windows 11 System , It Reached The loopback-interface Which Is Commonly Used For Applications/Services Communication on eachother inside the Windows System . And the Inbound Ports that are Filtered By The Firewall are also inside that specific Internal System Network Communication Segment . But I Bypassed It To Land A Packet Inside Internally And Triggered Some Interesting Responses Which Would Also Show On The DoSvc (Windows Update Delivery Optimization Port 7680) Service . That Triggered The IP Adress And Port 7680 To Reach A Remote IP/Port Adress Which I Can Specify To Spoof . So This Is In Development Still For Security Testing And Finding Bugs . I Will Go Into More Of It Persistently. Maybe Modification On The Packet Could Lead To ( RCE Remote Code Execution) On The Remote Target System.
#exploitdevelopment #exploit #zeroday #vulnerability #networking #network #windows11 #windows #system #systems #cybersecurity #security #securitytesting #hacker #hacking #hack #remote #injection #packet #wireshark #traffic #data #technology #digital #it #port #scanning
-
 13:25
13:25
xenjin450
11 months agoReverse-Engineering (Windows Update Delivery Optimization) Protocol & Bypass UAC DoSvc
35 -
 21:27
21:27
xenjin450
11 months agoWindows XP/Vista/7/8/10 Remote SMB Exploitation - Gain Full Remote System Access To Windows Systems
491 -
 40:24
40:24
Computer Solutions
7 months ago360 Total Security Tested 11.9.23
11 -
 2:27
2:27
infosectrain01
9 months agoWhat is Evil-Winrm | Evil-winrm Tool For Penetration Testing
47 -
 38:46
38:46
Computer Solutions
8 months agoMicrosoft Defender Antivirus Tested 10.25.23
9 -
 2:15
2:15
Professor K
9 months agoAllow an inbound port thru a Windows Firewall
4 -
 14:02
14:02
Professor K
9 months agoAnalyzing the Windows Registry for Evidence Using CSI Linux
20 -
 21:31
21:31
AllHackingCons
1 year agoFull speed Fuzzing Reducing Fuzzing Overhead through Coverage guided Tracing
-
 38:19
38:19
Computer Solutions
6 months agoTrend Micro Maximum Security Tested 12.16.23
3 -
 9:03
9:03
Dan On Dev - Hack Software Engineering Leadership
1 year agoWhy All Pen-Testing Services S_ck! Find out before you compare vendors
36