Premium Only Content
Cyber Security Tool BETTERCAP | Cyber Security Education | Security Measures in Description
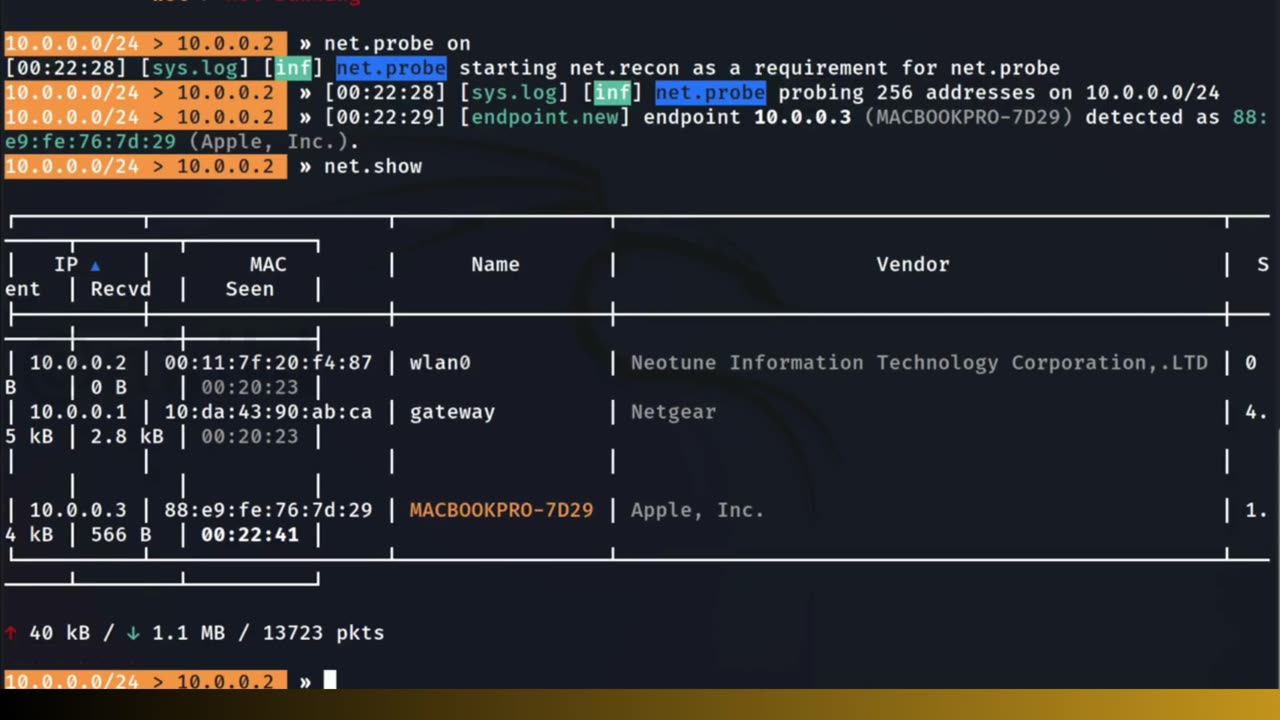
BETTERCAP is a powerful network manipulation and penetration testing tool that is commonly used in Kali Linux, a popular operating system for ethical hacking and security testing.
Bettercap allows security professionals and researchers to perform various network-related activities, such as network sniffing, spoofing, password capturing, and man-in-the-middle attacks.
Here are some key features and capabilities of Bettercap:
Network Sniffing: Bettercap can capture network traffic and analyze it for security analysis purposes. It can intercept and log network packets, allowing you to inspect the contents of the traffic flowing through the network.
Man-in-the-Middle Attacks: Bettercap facilitates man-in-the-middle (MITM) attacks, where it can position itself between a client and a server, intercepting and manipulating the communication between them. This capability is useful for testing the security of network devices, identifying vulnerabilities, and capturing sensitive information.
Password Capturing: Bettercap has the ability to capture login credentials, including usernames and passwords, by sniffing network traffic. This feature can be used to test the security of applications and systems by demonstrating the risk of transmitting sensitive data over unsecured networks.
DNS Spoofing: It can spoof DNS responses, allowing an attacker to redirect network traffic to malicious websites or perform phishing attacks by impersonating legitimate websites. This capability helps in identifying vulnerabilities in network configurations and applications that rely on DNS.
SSL/TLS Stripping: Bettercap can strip SSL/TLS encryption from secure connections, exposing the underlying plaintext traffic. This can be useful for testing the security of applications and services that rely on secure communication protocols.
Web Interface: Bettercap provides a web-based interface that allows users to easily interact with its features and view real-time network traffic and analysis. The web interface provides a user-friendly way to configure and control the tool.
It's important to note that Bettercap should only be used in a legal and ethical manner, with appropriate authorization and consent. It is primarily intended for security professionals, network administrators, and researchers who are responsible for testing and securing their own systems or performing authorized security assessments.
To protect yourself from potential BETTERCAP attacks, consider implementing the following security measures:
Encryption: Use secure protocols such as HTTPS, SSH, and VPNs to encrypt your network traffic. Encryption makes it difficult for attackers to intercept and manipulate your data.
Strong Passwords: Ensure that you use strong, unique passwords for all your accounts. Avoid using easily guessable passwords or reusing passwords across different platforms.
Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring a second verification step, such as a code sent to your mobile device, in addition to your password.
Be Wary of Untrusted Networks: Avoid connecting to untrusted or public Wi-Fi networks, especially for sensitive activities like online banking or accessing personal accounts. If you must use such networks, consider using a VPN for an added layer of encryption.
Regular Software Updates: Keep your operating system, applications, and security software up to date with the latest patches and updates. This helps protect against known vulnerabilities that attackers may exploit.
Firewalls: Configure and maintain firewalls on your network devices and systems. Firewalls act as a barrier between your network and potential threats, helping to block unauthorized access.
Network Monitoring: Regularly monitor your network for any suspicious activity or unexpected behavior. Implement intrusion detection and prevention systems (IDS/IPS) to detect and block potential attacks.
Security Awareness: Educate yourself and your team about common phishing techniques and social engineering attacks. Be cautious when clicking on links or downloading files from untrusted sources.
Disable Unused Services: Disable any unnecessary network services or protocols that you are not using. This reduces the attack surface and minimizes the potential for exploitation.
Regular Security Audits: Conduct regular security audits and penetration testing on your network and systems. This helps identify vulnerabilities and provides an opportunity to address them before they can be exploited.
Remember, while these measures can significantly improve your security posture, it's essential to stay vigilant and informed about the latest security threats and best practices.
-
 8:36
8:36
Dr. Nick Zyrowski
5 hours agoHow to Tighten Loose Skin Naturally (No Surgery Needed)
3721 -
 1:17:34
1:17:34
Sean Unpaved
3 hours agoNFL Sunday Showdown: Browns' Brutal Blitz Best? Dart's Daring Debut Dawns, Bears Breakthrough!
18.3K -
 6:33
6:33
Tundra Tactical
3 hours ago $0.04 earnedStupid Gun Myths & Questions Ep. 1 🛑NEW SERIES!!🛑
94 -
 LIVE
LIVE
Jeff Ahern
1 hour agoMonday Madness with Jeff Ahern
87 watching -
 1:34:59
1:34:59
Russell Brand
2 hours agoTrump Hails Charlie Kirk A Martyr As 100,000 PACK Arizona Stadium To Honor “American Hero” - SF637
175K46 -
 1:58:55
1:58:55
The Charlie Kirk Show
3 hours agoThe Charlie Memorial Aftermath | Benny Johnson, Sortor, Brick Suit | 9.22.2025
164K125 -
 1:56:39
1:56:39
Right Side Broadcasting Network
5 hours agoLIVE REPLAY: White House Press Secretary Karoline Leavitt Holds a Press Briefing - 9/22/25
78K31 -
 1:15:59
1:15:59
JuicyJohns
7 hours ago $0.21 earned🟢#1 REBIRTH PLAYER 10.2+ KD🟢
18.5K -
 45:33
45:33
The White House
5 hours agoPress Secretary Karoline Leavitt Briefs Members of the Media, Sep. 22, 2025
34.6K24 -
 1:05:07
1:05:07
Timcast
3 hours agoTrump Orders DOJ Bondi To Prosecute Democrats In Public Statement
200K122