Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
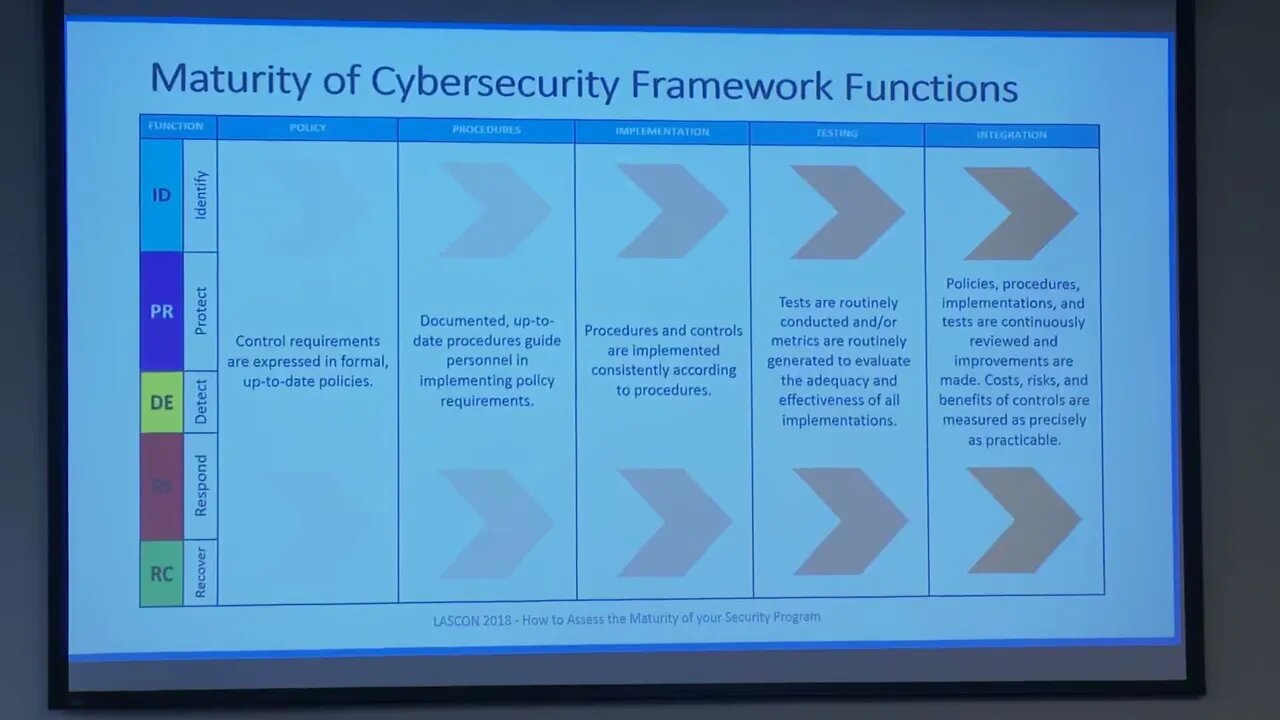
How to Assess the Maturity of your Security Progra
Loading comments...
-
 1:18:10
1:18:10
vivafrei
2 hours agoTom Homan "Bribery" Scandal Smells Like Russia-Gate 3.0! Ostrich Farm Update! Tommy Robinson & MORE!
85.4K32 -
 1:43:33
1:43:33
The Quartering
3 hours agoLiberal MELTDOWN As Trump Does The Impossible, Charlie Kirk Day, TPUSA Halftime Show & More
80.6K48 -
 LIVE
LIVE
StoneMountain64
3 hours agoBattlefield 6 Flick Keybind is WILD
108 watching -

The HotSeat
3 hours agoTrump "The Peacemaker", Unless You're Antifa!!! Part II
6.12K -
 LIVE
LIVE
Film Threat
1 day agoVERSUS: TRON: ARES VS. TRON LEGACY VS. TRON! BATTLE ON THE GRID! | Film Threat Versus
115 watching -
![[Ep 768] Trump: The President of Peace | Schumer Looking Worse by the Day | Columbus Day](https://1a-1791.com/video/fwe2/d0/s8/1/g/Q/s/q/gQsqz.0kob-small-Ep-768-Trump-The-President-.jpg) LIVE
LIVE
The Nunn Report - w/ Dan Nunn
1 hour ago[Ep 768] Trump: The President of Peace | Schumer Looking Worse by the Day | Columbus Day
255 watching -
 LIVE
LIVE
Owen Shroyer
1 hour agoOwen Report - 10-13-2025 - Senate Town Hall with Lindsey Graham Opponent Mark Lynch
1,994 watching -
 2:50:34
2:50:34
Side Scrollers Podcast
5 hours agoTony Blair SHILLS For Digital ID + UK BLOCKS 4Chan + Hasan DogGate ESCALATES + More | Side Scrollers
38.1K8 -
 1:01:37
1:01:37
DeVory Darkins
4 hours ago $26.48 earnedHostages released as Trump delivers historic speech... Portland descends into bizarre protest
106K79 -
 1:04:25
1:04:25
Jeff Ahern
2 hours ago $0.02 earnedMonday Madness with Jeff Ahern
17.7K4