Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
Special report: How does U.S. CIA conduct cyberattacks on other countries?
2 years ago
18
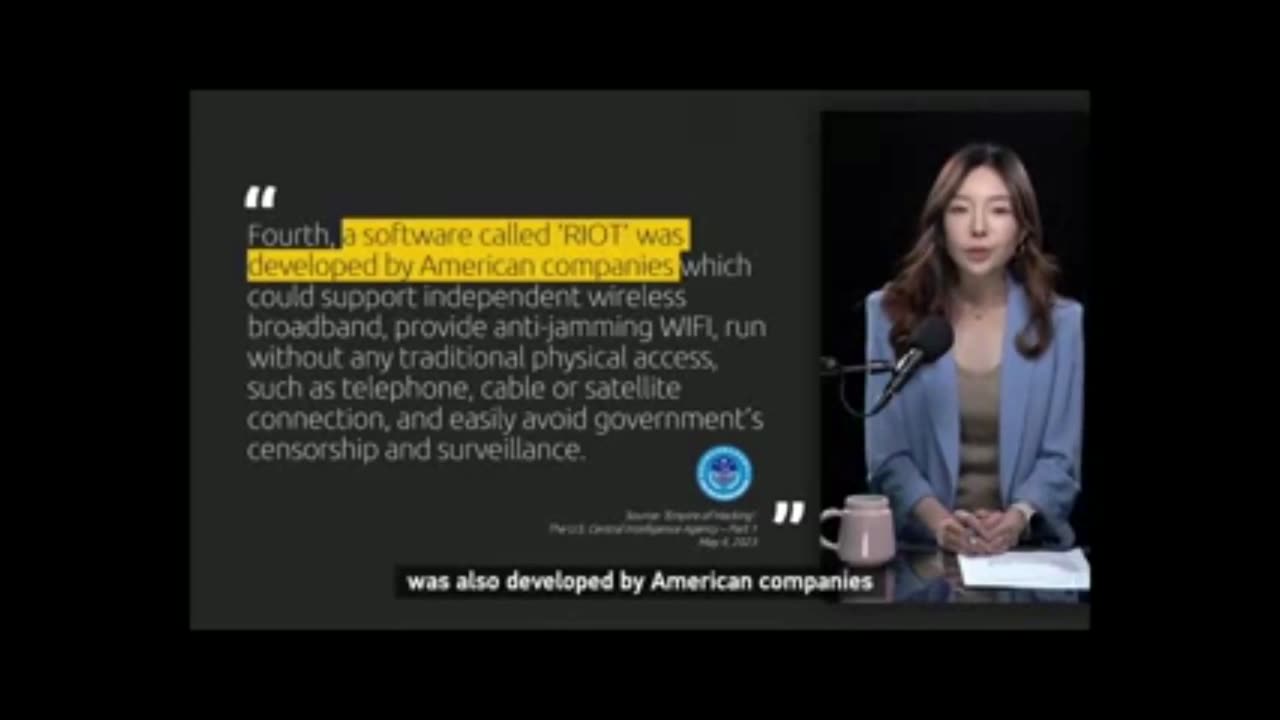
China's National Computer Virus Emergency Response Center (CVERC) and 360 Total Security (360) jointly released an investigative report on Thursday, revealing the U.S. Central Intelligence Agency's (CIA) cyber-attack weapons, analyzing its cyber attacks and espionage activities, and disclosing the process of such incidents occurring in China and other countries with real cases. CGTN's "Facts Tell" brings you the details.
Loading comments...
-
 LIVE
LIVE
SOLTEKGG
1 hour ago🔴LIVE - Battlefield 6 - Going Pro in RED SEC
406 watching -
 11:37
11:37
tactical_rifleman
2 days agoRare Breed BEATS THE ATF | FRT-15 | Tactical RIfleman
62.9K21 -
 LIVE
LIVE
Pepkilla
2 hours agoMore GOLD Camo's PLEASE Grind Call Of Black Ops 7
131 watching -
 1:35:54
1:35:54
LexTronic
1 hour agoMetroid Prime Remastered
2.73K -
 12:32
12:32
MetatronGaming
16 hours agoBLIGHT looks AMAZING - Trailer Reaction
11.9K10 -
 LIVE
LIVE
ProRedmanX
1 hour agoSunday Morning Coffee & Chaos ☕ | PUBG -> BF6 -> ??? #goonsquad
70 watching -
 5:23
5:23
Memology 101
22 days ago $12.56 earnedReporter HUMILIATES Kamala Harris over "WORLD-CLASS" dodge during interview
13.3K44 -
 LIVE
LIVE
ItsJustChrisTV
1 hour agoRescue Rangin'! Lets (try to) Save Some Folks!
82 watching -
![[Arc Raiders] Time for Some Keys, Increase This Stash, Scrappy and Tables Are All Max. Time for More](https://1a-1791.com/video/fwe2/ac/s8/1/4/g/x/C/4gxCz.0kob-small-Arc-Raiders-Time-for-Some-K.jpg) 1:11:44
1:11:44
Palermozeto
1 hour ago[Arc Raiders] Time for Some Keys, Increase This Stash, Scrappy and Tables Are All Max. Time for More
1.77K -
 LIVE
LIVE
The Sufari Hub
3 hours ago🔴WE ARE FEATURED - TTS ACTIVE - BLACK OPS 7 EXTRACTION MODE - LEVEL GRINDING
78 watching