Why Country All Over The World Hate U.S.A. Intelligence CIA-DOJ-FBI Killing Agencies
Do You Trust the FBI, CIA, DOJ, ATF, IRS and Other Government in general after all the recent evidence of conspiracy being exposed ? Spies, Informants and New Enemies Intelligence agencies are influencing governments and spying on countries with no regard for the law. And they are able to remain nearly invisible, in the process. Are they the new superpowers ?
The Answer is No or Yes, I do. Of course, the follow up question would be — Why or Why Not ?
And the answer is that the aforementioned agencies have a great number of people, (Special Agents, Operators, whatever sobriquet you choose to use) who defend this nation and its citizens from the evil intent of those who wish to destroy us. What we see reported in the news is an anomaly, a small group of individuals who have compromised their ethics, their morality, and their oath of office for political or financial gain. And because of their perfidy, they have disgraced not only themselves, but the agencies with which they are affiliated with the taint of scandal. We see these agencies more oftentimes than not portrayed as some sinister entity whose agents are at the heart of some dark, clandestine conspiracy. And because of this, we tend to view all who are employed by these agencies as morally compromised and inherently evil. However, there are those whose names grace a marble wall in anonymity that reflect the unseen heroism of self sacrifice. There are those whose names are etched in stone on monuments across this nation who gave their lives to protect those in the communities they served. They had families; they had children; they had hopes and dreams, just like the rest of us. But they took an oath to protect and to serve. And sadly, at times, that oath requires that they sacrifice their lives, so that we may live ours.
What we see portrayed in movies and on the nightly news is a microcosm, an anomaly of the whole. For the most part these men and women do a job most of us can't…or won't do. But when we need their expertise in solving a murder, catching a violent criminal or preventing a catastrophic event from enveloping this nation these men and women and the agencies they represent, are the first ones we call. We rely on them because we trust them. And I for one, do not see that trust as being misplaced.
The last time intelligence agencies commanded as much power as they do today was during the Cold War. Technological innovations mean that more sophisticated warfare is now a reality. It is not just about Russia and the USA anymore. We may be entering a new era of unrest.
The U.S.A. has lost more spies and informants since 2022 than at any other time since the Cold War. Leaders of German intelligence agencies also acknowledge that they have once again fallen upon tough times. Money, data and access are proving to be major factors in determining who actually wields power. The 2016 U.S. election made this clear: U.S. intelligence agencies are certain that Russian intelligence helped elect Donald Trump.
But the U.S. has lost old spheres of influence and allies are increasingly pursuing their own agendas. Can President Biden make his country a force for order in the world, again? And what does that mean for political hot spots and potential conflicts with China, Iran, and Russia? And for allies like Saudi Arabia and Turkey? Will Western intelligence agencies regain the power they once exerted? Wars fought with drone and hacker attacks, increasingly delegated power, and surveillance could push these conflicts to their tipping point.
The Left/Right paradigm isn't only exposed by race and immigration issues. The Left and Right are in lockstep on every issue that really matters: The IRS. Income tax. Federal Reserve system. Endless wars. Endless expansion of tyranny and ever contracting liberty. Chronically wide-open borders. Suicidal immigration policies. Don't you see? The democrats and republicans exist only to provide the illusion of choice. A strong "us versus them" simulation in every election. It's ritualized tribalism. But the joke is, it doesn't matter which team wins, because both sides have the same agenda. God, guns and gays are phony "issues" to bolster the illusion of "difference" between the parties. The only thing that makes all this possible is that people aren't aware of the scam. Just knowing they are either "Team Red" or "Team Blue" liberates them from the responsibility of having to actually know or think anything. Then they feel righteous when their team wins, or despondent when they loose. It's no coincidence that the system works exactly like sports. There comes a point when ignorance and apathy become treason. We are past that point, people.
On a scale of 1-10 with ten being the most, how much do you trust the IRS, FBI, CIA, SEC, NSA and why should someone issue an Executive Order to have them consolidated into a new streamlined efficiently running division of the US Government?
Wow, what a stunning level of incompetence this would demonstrate if Donald Trump were to merge domestic law enforcement (FBI) and foreign intelligence (CIA) and tax administration (IRS—which is really about revenue collection, not intelligence), and the SEC (administering stocks and trading commercially). It would be like merging the US State Department, your local animal shelter, the Fire Departments around the US, and the office that issues business licenses for each State. It would be fricking crazy and incompetent. For Trump to do this, he’d be a negative 100. It wouldn’t “streamline” or improve efficiency, it would substantially decrease efficiency. And of course, where would this leave all of the other intelligence agencies (NGA, DIA, NRO, etc.)?
Here are two basic rules that are proven over and over and over and over again:
Don’t mix domestic law enforcement and foreign intelligence: that’s what dictators do. Gotta keep ’em separate. They’re two different fields with standards and roles.
“Streamlining" by combining agencies so there is only one is usually a way to produce worse performance and corruption. We could have one giant police force all around the US administered by the Federal government. Or we can have sheriff departments (that administer jails), prison officials (for people convicted of felonies), local police departments (who investigate crimes), state police (who cover the jurisdictional gaps in between police departments), and Federal law enforcement (FBI, Federal Marshalls service, etc.)—which is what we have now. It makes it much harder to get corruption that works because the redundant and overlapping agencies police each other. The question of “who will police the police?” is a critical one. And when local police know their work is seen by State officers and the FBI can insert itself than it helps to keep people less corrupt and pay more attention to detail. If you want to build widgets, think about centralizing your processes. But if you’re going to give people guns and badges with the authority to arrest people or use deadly force, than provide a lot of checks and balances.
Section 702’s Unconstitutional Domestic Spying Program Must End A few months ahead of its expiration this fall, the Biden administration has announced its intention to seek renewal of Section 702 of the Foreign Intelligence Surveillance Act (FISA)—an invasive and unconstitutional law that cannot continue to exist in its current form.
On its face, Section 702 allows the government to conduct surveillance inside the United States so long as the surveillance is directed at foreigners currently located outside the United States. It also prohibits intentionally targeting Americans. Nevertheless, the NSA routinely (“incidentally”) acquires innocent Americans' communications without a probable cause warrant. In fact, FISA Court judges who approve Section 702 surveillance never learn about, let alone approve, the targets of surveillance under Section 702, and they rely entirely on certifications from the executive branch that downplay the nature of incidental surveillance of Americans. Then, rather than “minimize” the sharing and retention of Americans’ data, as Congress required, the NSA routinely shares such data with the FBI, CIA, and National Counterterrorism Center, and all agencies retain it for at least five years. Since Section 702 was last reauthorized in 2018, it has only become clearer that this provision is a rich source of warrantless government access to Americans’ phone calls, texts, and emails.
In this way, Section 702’s mass surveillance of Americans and the availability of that information to law enforcement isn’t just “incidental”—it's the primary function of the program. What should we do about a program where the byproduct of the program becomes the primary benefit to the government?
As early as 2011, the FISA Court held that the NSA's collection of Internet communications violated the Fourth Amendment because, despite targeting foreign communications, the agency was still collecting approximately 56,000 American emails a year. And yet, this collection continued. In 2021 alone, the FBI conducted up to 3.4 million warrantless searches of Section 702 data to find Americans’ communications. Congress and the FISA Court have imposed modest limitations on these “backdoor searches,” but according to several recent FISA Court opinions, the FBI has engaged in “widespread violations” of even these minimal privacy protections.
In addition to stopping the unconstitutional surveillance, Section 702 also needs new measures of transparency to enable future audits and accountability of these secretive programs. FISA has long contained procedures for private parties to sue over surveillance that violates their rights, including a mechanism for considering classified evidence while preserving national security. But, in lawsuit after lawsuit, the executive branch has sought to avoid these procedures, and the judiciary, including the Supreme Court, has adopted cramped readings of the law that create a de facto national security exception to the Constitution.
EFF is far from alone in this fight to reform Section 702. Not only are we joined by a large number of civil liberties and civil rights groups, even members of the Executive Branch’s Privacy and Civil Liberties Oversight Board (PCLOB) have announced that this program should not continue as is. PCLOB member Travis LeBlanc said at a conference, “Given what I have seen and what I know, I do have several concerns about a clean reauthorization without significant, common-sense reforms to safeguard privacy and civil liberties.”
Section 702 has become something Congress never intended: a domestic spying tool. Congress should consider ending the program entirely, but certainly not reauthorize Section 702 without critical reforms, including true accountability and oversight.
At Congressional Hearing, PCLOB Members Suggest Bare Minimum of 702 Reforms Last week, the House Judiciary Subcommittee on Crime and Federal Government Surveillance held a hearing on “Fixing FISA: How a Law Designed to Protect Americans Has Been Weaponized Against Them,” ahead of the December 2023 expiration of the Section 702 surveillance authority. The three witnesses, Michael E. Horowitz (Inspector General, U.S. Department of Justice), Sharon Bradford Franklin (Chair, U.S. Privacy and Civil Liberties Oversight Board), and Beth A. Williams (Board Member, U.S. Privacy and Civil Liberties Oversight Board) all sketched out their visions for the good, the bad, and the ugly about the invasive surveillance power.
The witnesses managed to use the hearing to sketch out a vision for what a minimally sufficient bill to reform Section 702 would look like. However, they were not nearly as skeptical as we are of the necessity of domestic law enforcement’s use of these powers–especially when the information collected under 702 could be obtained by law enforcement with a warrant through more traditional avenues.
Section 702 allows the government to conduct surveillance inside the United States by vacuuming up digital communications so long as the surveillance is directed at foreigners currently located outside the United States. It also prohibits intentionally targeting Americans. Nevertheless, the NSA routinely (“incidentally”) acquires innocent Americans' communications without a probable cause warrant. Once collected, the FBI can search through this massive database of information by “querying” the communications of specific individuals.
Previously the FBI alone reported conducting up to 3.4 million warrantless searches of Section 702 data in 2021 using Americans’ identifiers. Congress and the FISA Court have imposed modest limitations on these backdoor searches, but according to several recent FISA Court opinions, the FBI has engaged in “widespread violations” of even these minimal privacy protections.
A just-published transparency report from the Office of the Director of National Intelligence (ODNI) includes a “recalculation” of these statistics, reporting instead just under 3 million searches for 2021, and around 120,000 and 800,000 for 2022 and 2020 respectively. The report says that a single cybersecurity investigation in 2021 involving attempts to “compromise critical infrastructure” led to “approximately 1.9 million queries related to potential victims—including U.S. persons—[and] accounted for the vast majority of the increase in U.S. person queries conducted by FBI over the prior year.”
But we should be far from reassured by these revised estimates of warrantless, backdoor searches of the 702 databases. First, even the lowest reported figure—nearly 120,000 searches in 2022—is still a whole lot of warrantless searches of Americans’ private communications. Second, the methodology used in this new report requires additional scrutiny. For example, it says that the FBI’s new counting method includes “deduplication,” where “instances in which the same query term was run multiple times, whether by the same user or by different users” are apparently treated as only one search. There’s no reason to consider that the right way to count, though. If police conducted separate warrantless searches of a person’s house on Monday, Wednesday, and Friday, a court would likely treat that as three separate violations of the person’s Fourth Amendment rights.
Regardless of the exact numbers, the disturbing history of overreach is why it’s so urgent that civil society, concerned people, and lawmakers act to pass legislation that radically reforms Section 702 before we’re stuck with another 4 years of warrantless backdoor searches of U.S. data.
The Good Suggestions:
Chair of the PCLOB Sharon Bradford Franklin had three vital recommendations for the committee to consider before voting on legislation to renew Section 702.
Reduce the volume of “incidental collection.” The act of reducing the volume of U.S. persons’ data being swept up by Section 702 would also involve getting an accurate estimate of just how wide-reaching the problem is, something on which we are incapable of getting accurate figures at the moment.
End backdoor searches of data on U.S. persons by requiring judicial review before domestic law enforcement agencies like the FBI are able to query information about individual U.S. persons, regardless of whether the search is reasonably likely to return information on foreign intelligence or is being used to gather evidence of a crime committed on U.S. soil.
Permanently revoke the now defunct authorization to conduct “abouts” collection which was paused by the NSA in 2017 amid civil liberties concerns. These are collections of information not sent to or from a target but are communications “about” or which make reference to a surveillance target. Franklin believes we should not rest easy on the NSA’s pause of this procedure, but should ban it explicitly in any 702 renewal legislation.
These three suggestions are a good starting point, but much more work needs to be done to address the over-classification and government secrecy that hinders accountability, enables abuse, and prevents people from suing to address harms done by government surveillance.
The Bad Suggestions:
Government representatives are always quick to testify to the legitimacy and utility of these programs by vaguely referencing classified events or attacks that intelligence agencies thwarted thanks to this program. Part of the problems of over-classification and extreme secrecy is that we’re expected to take their word for it rather than be brought into the process of understanding whether and when these programs actually provide some utility and are not–like Section 215 of the USA FREEDOM Act–touted as absolutely necessary until their authorities expire with little to no pushback from the national security apparatus.
PLCOB member Beth Williams also suggested that Section 702 was not a “bulk” collection program because it required specific targeting of individuals for surveillance–a claim that EFF contests as being an absolute myth.
Even worse, Williams suggested Section 702 and its invasive surveillance capabilities–vacuuming up and reviewing communications, presumably with people overseas, should be used as a tool for vetting hopeful immigrants to the United States as well as being people vetted for government jobs. This might give immigration services the ability to audit entire communication histories before deciding whether an immigrant can enter the country. This is a particularly problematic situation that could cost someone entrance to the United States based on, for instance, their own or a friend’s political opinions—as happened to a Palestinian Harvard student when his social media account was reviewed when coming to the U.S. to start his semester.
Our 702 Reform Wishlist:
In addition to ending warrantless backdoor searchers, Section 702 also needs new measures of transparency to enable future audits and accountability of these secretive programs. FISA has long contained procedures for private parties to sue over surveillance that violates their rights, including a mechanism for considering classified evidence while preserving national security. But, in lawsuit after lawsuit, the executive branch has sought to avoid these procedures, and the judiciary, including the Supreme Court, has adopted cramped readings of the law that create a de facto national security exception to the Constitution. We need real accountability, and that includes the opportunity to contest surveillance in court.
Internal Documents Show How Little the FBI Did to Correct Misuse of Section 702 Databases The Federal Bureau of Investigation (FBI) has released internal documents used to guide agency personnel on how to search the massive databases of information collected under the Foreign Intelligence Surveillance Act, including communications collected without a warrant under Section 702. Despite reassurances from the intelligence community about its “culture of compliance,” these documents depict almost no substantial consideration of privacy or civil liberties. They also suggest that in the years before these guidelines were written, even amidst widespread FBI misuse of the databases to search for Americans’ communications, there were even fewer written guidelines governing their use. Above all, FBI agents can still search for and read Americans’ private communications collected under Section 702, all without a warrant or judicial oversight.
Section 702 allows the government to conduct surveillance inside the United States by vacuuming up digital communications so long as the surveillance is directed at foreigners currently located outside the United States. It also prohibits intentionally targeting Americans. Nevertheless, the NSA routinely (“incidentally”) acquires innocent Americans' communications without a probable cause warrant. Once collected, the FBI can search through this massive database of information by “querying” the communications of specific individuals.
In 2021 alone, the FBI conducted up to 3.4 million warrantless searches of Section 702 data to find Americans’ communications. Congress and the FISA Court have imposed modest limitations on these “backdoor searches,” but according to several recent FISA Court opinions, the FBI has engaged in “widespread violations” of even these minimal privacy protections.
After a string of scandals, these newly released documents demonstrate some of the steps the FBI took to train personnel who apparently did not understand how to stay within the law’s extremely broad mandate. Namely, to query the collected communications of U.S. persons only if they are investigating foreign intelligence, a crime, or both, still without judicial review. According to FBI director and media reports, these guidelines led to a significant drop in unauthorized searches, but even this “dramatic” drop still allegedly resulted in over two hundred thousand warrantless searches of Americans’ private communications in 2022 alone. That’s two hundred thousand too many; Congress should close the “backdoor loophole” and require the FBI to get a search warrant.
In addition to stopping the unconstitutional surveillance, Congress needs to include robust new transparency measures into any reauthorization of Section 702 to enable future audits and accountability of these secretive programs. FISA has long contained procedures for private parties to sue over surveillance that violates their rights, including a mechanism for considering classified evidence while preserving national security. But, in lawsuit after lawsuit, the executive branch has sought to avoid these procedures, and the judiciary, including the Supreme Court, has adopted cramped readings of the law that create a de facto national security exception to the Constitution.
EFF is far from alone in this fight to reform Section 702. Not only are we joined by a large number of civil liberties and civil rights groups, even members of the Executive Branch’s Privacy and Civil Liberties Oversight Board (PCLOB) have announced that this program should not continue as is. PCLOB member Travis LeBlanc said at a conference, “Given what I have seen and what I know, I do have several concerns about a clean reauthorization without significant, common-sense reforms to safeguard privacy and civil liberties.”
Section 702 has become something Congress never intended: a domestic spying tool. Congress should consider ending the program entirely, but certainly not reauthorize Section 702 without critical reforms, including true accountability and oversight.
Even New World Order Likely Can't Sue the NSA or FBI to Protect His Rights In a stunning revelation, a sitting U.S. Congressman has publicly identified himself as the subject of likely illegal surveillance by the NSA and FBI. During a hearing on the question of renewal the controversial mass NSA spying authorities known as FISA Amendments Act section 702, Rep. Darin LaHood of Illinois revealed: “the member of Congress who was wrongly queried multiple times solely by his name was in fact me.” It seems Rep. LaHood was one of the Congresspersons identified in a footnote (footnote 92) in a recent government report about the mass spying program which stated that an intelligence analyst improperly repeatedly searched 702 data “using only the name of a U.S. congressman.”
What’s equally stunning is that despite absolutely knowing that he was spied upon – something that is extremely rare given the level of secrecy around 702 – neither Rep. LaHood nor anyone else illegally spied upon will likely get a chance to seek a remedy in a court. That’s not just because 702 is poorly drafted and has been even more poorly executed. It’s because of how governmental secrecy has now metastasized to completely prevent anyone from stopping illegal NSA spying of them, much less get any other legal remedy.
Quite simply, governmental secrecy now renders moot many of the accountability and oversight mechanisms for national security surveillance that exist on paper in FISA as well as in the U.S. constitution.
A Little History – EFF in the Courts
One of EFF’s highest priorities for nearly two decades is making sure you can have a private conversation online. And specifically, we want to ensure that individuals can seek judicial accountability for violations of their constitutional and statutory rights committed through the government’s warrantless foreign intelligence surveillance inside the United States.
EFF’s work on this issue predates the passage of Section 702 itself. Our 2006 lawsuit, Hepting v. AT&T, relied on first-hand evidence from whistleblower Mark Klein to show that the telecommunications companies were copying the contents of Internet traffic at the behest of the NSA. Congress essentially mooted this lawsuit in 2008 by granting the companies retroactive immunity as part of the FISA Amendments Act, which also instituted Section 702. Not to be deterred, and at the specific suggestion of key members of Congress, EFF again sued on behalf of AT&T customers, this time seeking to hold the government itself accountable. That lawsuit, Jewel v. NSA, powered on for 14 years, bolstered by the Snowden revelations and the flood of additional public information about the NSA’s mass spying programs.
Jewel v. NSA and the Locking of the Courthouse Door
The Jewel lawsuit came to an end last year, not because the judiciary disagreed with our arguments about the unconstitutionality or illegality of the government’s surveillance. It ended but because the courts validated the government’s claims that a program known and debated across the world is somehow too secret to be challenged in open court by members of the public affected by it. Specifically, the Supreme Court refused to grant certiorari and reconsider a Ninth Circuit decision (and an underlying district court ruling) that held that the common law state secrets privilege blocked our clients’ efforts to prove that their data was intercepted, such that they had standing to sue. A similar case brought by the ACLU on behalf of Wikimedia was also rejected.
As Jewel illustrates, the judiciary has used secrecy to create a broad national-security exception to the Constitution, FISA, and 702 itself that allows all Americans to be spied upon by their government and denying them any viable means of challenging that spying. And now that impacts a sitting member of Congress directly.
This exception rests on a pair of misinterpretations of common law and statutory procedures for dealing with supposedly secret evidence. First, courts have allowed the government to invoke the state secrets privilege in Section 702 cases, despite Congress’ express creation of a statutory method for a federal court to secretly review evidence of claimed illegal surveillance, 50 U.S.C. § 1806(f). Second, the courts have expanded the scope of that privilege to effectively allow the government to claim secrecy over widely known facts, and end litigation involving these facts, based on little more than its own say-so.
Congress Can Reopen the Courthouse Doors to Surveillance Victims
With the upcoming sunset of Section 702, Congress has the opportunity to correct these mistakes. Congress can and should reaffirm its intention to create actual, useable accountability measures for the inevitable circumstances when individuals are wrongly surveilled or impacted by surveillance, and reopen the courthouse doors to individuals trying to protect their rights.
First, Congress can expressly override the Supreme Court’s mistaken statutory interpretation of FISA Section 1806 in FBI v. Fazaga, 142 S. Ct. 1051 (2022). Contrary to the Court’s holding in Fazaga, Congress clearly intended for individuals to be able to seek redress when they were wrongfully surveilled and, to do that, intended Section 1806(f) to displace the state secrets privilege in lawsuits in which evidence relating to electronic surveillance is relevant. The Supreme Court’s ruling essentially makes FISA’s promise of individual redress for violations of surveillance law a dead letter. Congress should reaffirm the rightful interpretation of the statute and correct the Supreme Court’s mistake.
Second, even when the state secrets privilege can apply, Congress can make clear that the case should not be dismissed. As far back as 2009, Congress debated the State Secrets Protection Act, H.R. 984, 110th Cong. (2009), which would have created procedures for courts to securely review evidence that the government claims is secret, and prevent cases from being dismissed based on state secrecy until plaintiffs have had an opportunity to discover all non-privileged evidence. Congress should revive these reforms and consider including them as part of any renewal or reform to Section 702.
In short, the courts have effectively blocked individuals from seeking the judicial accountability that Congress intended. Representative LaHood is just the latest in a long line of people who know they were surveilled but cannot do anything about it. It’s good that he has a position of authority over the NSA—it’s unlikely they will do that specific surveillance again. But the rest of us deserve to access the courts to protect our constitutional rights too.
These are just a small subsection of the needed reforms to ensure accountability and oversight of Section 702. Spying on the whole world is a bad idea because everyone deserves privacy of their communications. But as the now two decades of NSA mass spying demonstrates, spying on the whole world while protecting the constitutional rights of Americans just cannot be done. It’s time to stop the charade and let this authority expire.
We Need Answers About the CIA’s Mass Surveillance The Central Intelligence Agency has been collecting American’s private data without any oversight or even the minimal legal safeguards that apply to the NSA and FBI, an unconstitutional affront to our civil liberties.
According to a declassified report released yesterday by the Privacy and Civil Liberties Oversight Board (PCLOB), the CIA’s surveillance program is reminiscent of the mass surveillance programs conducted by the NSA, though the details released thus far paint a disturbing picture of potential wide-scale violations of people’s privacy. To start, the CIA program has apparently been conducted outside the statutory reforms and oversight of the intelligence community instituted after revelations by Edward Snowden in 2013. The newly declassified CIA data collection program is carried out in conjunction with Executive Order 12333 and is therefore subject to even less oversight than the woefully under-supervised NSA surveillance programs subject to the Foreign Intelligence Surveillance Act. The whos, whats, whys, and hows of this semi-disclosed CIA program are still unknown, and the public deserves the right to know exactly what damage has been done. Senators Ron Wyden and Martin Heinrich are already pressing for the release of even more information. In a partially-redacted letter sent to the Director of National Intelligence and the CIA Director on April 13, 2021, the senators have called for the public release of the full report about the CIA’s surveillance, which remains classified. The senators’ letter also demands answers about how the agency collects the data, what data is being collected, and the rules governing its storage and retention.
From that letter and a PCLOB “Staff Recommendations” document, we know that the CIA collects a vast amount of data, often on U.S. persons, without any clear guidelines about data retention and without substantial oversight of analysts querying information about U.S. citizens. The program seems to exist outside the jurisdiction of either courts or Congress–given that even the Senate Intelligence Committee was left in the dark about this program.
According to PCLOB’s staff recommendations, when an analyst attempts to look at information relating to an American citizen, a “pop-up box will appear to remind the analysts that an F[oreign] I[ntelligence] purpose is required for such a query. However, analysts are not required to memorialize the justification for their queries. As a result, auditing or reviewing U.S. Person (USP) queries is likely to be challenging and time-consuming.” So, not only is there no way of preventing curious and prying eyes of CIA agents from pulling up data about their friends and family–there’s no good way to audit agents’ activity after the fact. And we shouldn’t be surprised that this might be happening. In the past, NSA officers often used their invasive surveillance powers to spy on significant others. In response, the PCLOB staff recommended for the CIA to employ “automated tools” to assist in the auditing and compliance monitoring involving all of that U.S. data.
“The declassification is urgent,” the Senators’ letter states—we agree.
In their letter, Wyden and Heinrich inquire as to the nature of the CIA’s relationship to its “sources,” perhaps a reference to whether the CIA might be getting some of its data from the same place as the NSA—through secretive agreements with private companies. In 2013, it was reported that the CIA paid $10 million a year in order to gain access to AT&T’s call data.
In addition to new declassifications and clarity on the scope of this program, the government needs to act fast to prevent the CIA from continuing to circumvent constitutional rights. If we learn, in fact, that the CIA is purchasing this data, then Congress should work fast to pass the Fourth Amendment is Not for Sale Act. Intended to prevent government agencies and law enforcement from buying data harvested from apps—data they otherwise could not get without a warrant—the bill may also work to prevent the CIA from purchasing the phone records of U.S. persons in bulk.
Regardless of the CIA’s legal justification or technical means of collection and storage, Congress must act fast to ensure the Fourth Amendment’s vitality in the modern age.
Your Messaging Service Should Not Be a DEA Informant A new U.S. Senate bill would require private messaging services, social media companies, and even cloud providers to report their users to the Drug Enforcement Administration (DEA) if they find out about certain illegal drug sales. This would lead to inaccurate reports and turn messaging services into government informants.
The bill, named the Cooper Davis Act, is likely to result in a host of inaccurate reports and in companies sweeping up innocent conversations, including discussions about past drug use or treatment. While explicitly not required, it may also give internet companies incentive to conduct dragnet searches of private messages to find protected speech that is merely indicative of illegal behavior.
Most troubling, this bill is a template for legislators to try to force internet companies to report their users to law enforcement for other unfavorable conduct or speech. This bill aims to cut down on the illegal sales of fentanyl, methamphetamine, and counterfeit narcotics. But what would prevent the next bill from targeting marijuana or the sale or purchase of abortion pills, if a new administration deemed those drugs unsafe or illegal for purely political reasons? As we've argued many times before, once the framework exists, it could easily be expanded.
The Bill Requires Reporting to the DEA
The law targets the “unlawful sale or distribution of fentanyl, methamphetamine” and “the unlawful sale, distribution or manufacture of a counterfeit controlled substance.”
Under the law, providers are required to report to the DEA when they gain actual knowledge of facts about those drug sales or when a user makes a reasonably believable report about those sales. Providers are also allowed to make reports when they have a reasonable belief about those facts or have actual knowledge that a sale is planned or imminent. Importantly, providers can be fined hundreds of thousands of dollars for a failure to report.
Providers have discretion on what to include in a report. But they are encouraged to turn over personal information about the users involved, location information, and complete communications. The DEA can then share the reports with other law enforcement.
The law also makes a “request” that providers preserve the report and other relevant information (so law enforcement can potentially obtain it later). And it prevents providers from telling their users about the preservation, unless they first notify the DEA.
We Have Seen This Reporting Scheme Before
The bill is modeled off existing law that requires similar reporting about child sexual abuse material (CSAM). Lawmakers also previously tried and failed to use this reporting scheme to target vaguely defined terror content. This bill would port over some of the same flaws.
Under existing law, providers are required to report actual knowledge of CSAM to a group called the National Center for Missing and Exploited Children, a quasi-governmental entity that later forwards on some reports to law enforcement. Companies base some of their reporting on matches found by comparing digital signatures of images to an existing database of previously removed CSAM. Notably, this new bill requires reporting directly to the DEA, and the content at issues (drug sales) is markedly harder and more subjective to identify. While actual CSAM is unprotected by the First Amendment, mere discussion of drug use is protected speech. Due to the liability they would face for failing to report, some companies may overreport using content-scanning tools that we know have large error rates in other contexts.
Despite strong challenges, the existing CSAM reporting law has so far survived Fourth Amendment scrutiny because the government does not explicitly compel providers to search through their users’ communications (it only requires reporting if providers decide to search on their own). However, some applications of existing law have violated the Constitution—specifically, when providers make a report without fully examining the material they are reporting. In those cases, law enforcement has been deemed to have exceeded the scope of the private search by providers, which should require a warrant.
Like with this bill, a separate piece of the existing CSAM law requires providers to preserve user content after making a report. But there is increasing recognition that this compelled preservation constitutes a Fourth Amendment seizure that removes a user’s rights to delete their own content.
We Should Strengthen the Privacy of User Communications, Not Weaken Them
After years of attempts to weaken privacy, lawmakers should focus their interest on strengthening protections for user content. Under the 1986 Electronic Communications Privacy Act (ECPA), providers are generally restricted from handing over user information to law enforcement without some kind of legal process—whether it be a warrant, court order, or subpoena. However, this bill creates another carveout.
Rather than carving up ECPA, we need to update and strengthen the decades-old protections. EFF has been making this argument for more than a decade. And states like California have charted a path forward and will hopefully continue.
More immediately, if lawmakers do not abandon the Cooper Davis Act, the worst aspects must be avoided. When considering amendments, lawmakers should:
Make the reporting scheme entirely voluntary
Require the DEA to delete reports that contain innocent content, and prevent the DEA from targeting individual purchasers based on a report
Commission a study and create a sunset date to see if this reporting scheme even serves its stated purpose
At minimum, require the government to get a warrant for the lengthy preservation of content associated with a report
Make it easier for companies to notify their users about preservation requests, similar to the NDO Fairness Act
The EARN IT Bill Is Back, Seeking To Scan Our Messages and Photos In a free society, people should not have their private correspondence constantly examined. U.S. lawmakers, we would hope, understand that individuals have the right to a private conversation without the government looking over their shoulder.
So it’s dismaying to see a group of U.S. Senators attempting for a third time to pass the EARN IT Act (S. 1207)—a law that could lead to suspicionless scans of every online message, photo, and hosted file. In the name of fighting crime, the EARN IT Act treats all internet users like we should be in a permanent criminal lineup, under suspicion for child abuse.
What The New “EARN IT” Does
The EARN IT Act creates an unelected government commission, stacks it with law enforcement personnel, and then tasks it with creating “best practices” for running an internet website or app. The act then removes nearly 30-year-old legal protections for users and website owners, allowing state legislatures to encourage civil lawsuits and prosecutions against those who don’t follow the government’s “best practices.”
As long as they somehow tie changes in law to child sexual abuse, state lawmakers will be able to avoid longstanding legal protections, and pass new rules that allow for criminal prosecutions and civil lawsuits against websites that don’t give police special access to user messages and photos. Websites and apps that use end-to-end encryption to protect user privacy will be pressured to remove or compromise the security of their services, or they’ll face prosecutions and lawsuits.
If EARN IT passes, we’re likely to see state lawmakers step in and mandate scanning of messages and other files similar to the plan that Apple wisely walked away from last year.
There’s no doubt the sponsors intend this bill to scan user messages, photos, and files, and they wrote it with that goal in mind. They even suggested specific scanning software that could be used on users in a document published last year. The bill also makes specific allowances to allow the use of encryption to constitute evidence in court against service providers.
Bill Language Purporting To Protect Encryption Doesn’t Do The Job
Under pressure, the bill sponsors did add language that purports to protect encryption. But once you take a closer look, it’s a shell game. The bill clearly leaves room to impose forms of “client-side scanning,” which is a method of violating user privacy by sending data to law enforcement straight from user devices, before a message is encrypted. EFF has long held that client-side scanning violates the privacy promise of end-to-end encryption, even though it allows the encryption process to proceed in a narrow, limited sense. A 2021 paper by 10 leading technologists held that client-side scanners are a danger to democracy, amounting to “bugs in our pockets.”
The Chat-Scanning Software Being Pushed By This Bill Doesn’t Work
But the available evidence shows that scanning software that looks for Child Sexual Abuse Material, or CSAM, is far from perfect. Creators of scanning software say they can’t be fully audited, for legal and ethical reasons. But here’s the evidence so far:
Last year, a New York Times story showed how Google’s CSAM scanners falsely accused two fathers of sending child pornography. Even after the dads were explicitly cleared by police, Google kept their accounts shut down.
Data being sent to cops by the U.S. National Center for Missing and Exploited Children (NCMEC)—the government agency that will be tasked with analyzing vastly more user data if EARN IT passes—is far from accurate. In 2020, the Irish police received 4,192 reports from NCMEC. Of those, only 852 (20.3%) were confirmed as actual CSAM. Only 9.7% of the reports were deemed to be “actionable.”
A Facebook study found that 75% of the messages flagged by its scanning system to detect child abuse material were not “malicious,” and included messages like bad jokes and memes.
LinkedIn reported 75 cases of suspected CSAM to EU authorities in 2021. After manual review, only 31 of those cases—about 41%—involved confirmed CSAM.
The idea of subjecting millions of people to false accusations of child abuse is horrific. NCMEC will export those false accusations to vulnerable communities around the world, where they can be wielded by police forces that have even less accountability than law enforcement in the United States. False accusations are a price that EARN IT supporters seem willing to pay.
We need your support to stop the EARN IT Act one more time. Digital rights supporters sent more than 200,000 messages to Congress to kill earlier versions of this bill. We’ve beaten it twice before, and we can do it again.
There are currently dangerous proposals that could mandate client-side scanning schemes in the U.K. and European Union, as well. But we don’t need to resign ourselves to a world of constant surveillance. In democratic nations, supporters of a free, secure, and private internet can win—if we speak up now.
EFF, International Allies Warn That Proposed UN Cybercrime Treaty, Rather Than Making Us More Secure, Could Legitimize Intrusive Surveillance and Drag Down Global Privacy and Free Expression Standards.
EFF and international allies Access Now, Article 19, Epicenter, and Global Partners Digital are in Vienna this week and next for the fifth round of negotiations on the proposed UN Cybercrime Treaty, along with the over 100 representatives of Member States hashing out a new draft text.
While we have not yet been allowed to speak on the floor—or even sit in the same room as delegates—that has not stopped us from speaking out for users about the lack of human rights protections, the criminalization of online speech, the fostering of greater surveillance powers, and other dangers posed by the treaty in its current form.
At a livestreamed briefing yesterday in Vienna, we provided a reality check on how the talks have moved in troubling directions and challenged negotiators to seize this rare opportunity—negotiating a UN Treaty only happens every other decade—to draft a cybercrime treaty that does not undermine, but actually protects, privacy and free expression.
Briefing highlights: Katitza Rodriguez, Policy Director for Global Privacy, EFF
One big issue we're facing is that there isn't an effective global system in place to make sure human rights are enforced. Not many governments want to limit their own power to spy and track people closely. Because of this, the Convention might end up legitimizing intrusive surveillance power that invades people's private lives and infringe upon their rights.
Barbora Bukovská, Senior Director for Law and Policy, ARTICLE 19
We are really concerned that many provisions of this treaty restrict freedom of expression. States must not lose sight of the fact that content offenses, if coupled with surveillance powers and other restrictions, will create international carte blanche for those who want to use use this tool to restrict freedom of expression globally.
Raman Jit Singh Chima, Senior International Counsel and Global Cybersecurity Lead, Access Now
Our view is simple. Any UN cybercrime treaty should make us more cyber secure, it should not make us less cyber secure. A key part of any such international legal framework should look at the human beings involved in cyber security, namely security researchers, digital security trainers, as well as journalists who investigate vulnerabilities and gaps in computer systems. Unfortunately, our view is that the present text of the UN Cybersecurity Treaty process, unless drastically improved, would in fact make us less cyber secure.
Failing to provide legal protection for security researchers—whether in the form of heightened intent requirements for core cyber-dependent crimes (particularly unauthorized access) or a standalone, legitimate security research "safe harbour" mandate—would be a mistake that the global information security community can ill afford.
Tanja Fachathaler, Policy Advisor, Epicenter. works
(The UN Convention) aims to set global standards to fight cybercrime but it could also, if it were to fail, set a global standard for how we all lose our privacy. We urgently need strong safeguards and these unfortunately so far are not in place. The way many provisions at the moment are drafted is very broad, and it does not rule out the use of government hacking.
We advocate for an explicit requirement to be added that any investigative powers must be conducted in ways not to compromise the security of digital communications and services.
Ellie McDonald, Global Engagement and Advocacy Lead, Global Partners Digital
The reason that many countries say that they are engaging in this process is precisely because they want to strengthen cooperation on international cybercrime. At the same time they are saying this, we are hearing certain countries reject the inclusion of practical and robust safeguards which are derived from their existing human rights law obligations. We see that the safeguards, rather than being an obstacle to such cooperation, should really be seen as enabling. Not having them would introduce uncertainty, and that would hinder cooperation, the very thing that certain states say they desire by virtue of the treaty, and also cause risk to human rights, most importantly.
The U.S. Deserves Stronger Spyware Protections Than Biden’s Executive Order U.S. President Joe Biden has signed an executive order that limits U.S. government agencies from using commercially available spyware – but that doesn’t mean there will be no government use of spyware in the United States. Spyware is a type of malicious software (or malware) which allows someone to gain remote access to a target’s device without the knowledge or consent of the device operator. This includes all of the data on it: messenger logs, photos, files, and contacts. It also gives the ability to conduct novel forms of real-time surveillance, for example, by accessing the device’s microphone and cameras. This technique has been used by nation-states around the world to spy on journalists, dissidents, and minority groups.
Additionally, spyware allows governments to manipulate data on devices, including corrupting, planting, or deleting data, or recovering data that has been deleted, all while erasing any trace of the intrusion. There is a growing concern about law enforcement taking control of suspects' digital devices and tampering with their content.
The executive order arrived only days before revelations that the United States, which was previously thought to have steered clear of some of the most infamous foreign spyware products, actually had a contract to test and deploy the notorious Pegasus created by Israeli company NSO Group. The contract was signed under a fake name on November 8, 2021 between an organization that acts as a front for the U.S. government and an American affiliate of NSO group. Only five days before, on November 3, 2021, the U.S. Commerce Department added NSO Group and other foreign spyware companies to a blacklist —the “Entity List for engaging in activities that are contrary to the national security or foreign policy interests of the United States.” So the signing of this straw contract was in apparent breach of this ban.
NSO Group is just one of the companies that should be covered by the new executive order. Foreign spyware like Karma has been used to abuse human rights as well, purchased by the UAE-based cyber-espionage company DarkMatter. DarkMatter went a step further than even the NSO Group, deploying the spyware to targets themselves and closely coordinating with its government customers in operations using spyware. One such operation involved the arrest and torture of prominent women’s rights advocate Loujain AlHathloul. Representing AlHathloul, EFF took DarkMatter to court for their violation of U.S. anti-hacking and international human rights laws.
The executive order signals that the Biden administration’s biggest concern with using spyware like Pegasus is that its foreign origins create a counter-intelligence concern. While this is a relatively narrow lens to look at the harms of spyware,, the executive order does make strides in specifying ways in which spyware is not to be used, bucking the global trend of using this software to target on journalists and dissidents. The EO prohibits the US from purchasing or using any spyware sold by a company whose products have been used for either of two prohibited purposes:
(1) to collect information on activists, academics, journalists, dissidents, political figures, or members of non-governmental organizations or marginalized communities in order to intimidate such persons; curb dissent or political opposition; otherwise limit freedoms of expression, peaceful assembly, or association; or enable other forms of human rights abuses or suppression of civil liberties; or
(2) to monitor a United States person, without such person’s consent, in order to facilitate the tracking or targeting of the person without proper legal authorization, safeguards, and oversight
Though the NSO Group’s Pegasus spyware has garnered particular attention for its widespread use against human rights advocates, journalists, and politicians, the EO did not name any company specifically, keeping the policy broad. This may lead some government agencies to think that their purchase of foreign spyware might fly under the radar if it comes from another, smaller vendor, or the vendor can plausibly deny that it is really spyware that they are selling. We urge the Biden administration to publish a non-exhaustive list of spyware companies included as part of this ban. That would send a clear message to agencies who wish to exploit any ambiguity in order to skirt the law.
Building upon the U.S. EO, a global coalition of eleven countries, including Australia, Canada, Costa Rica, Denmark, France, New Zealand, Norway, Sweden, Switzerland, the United Kingdom, and the United States, are working towards a common goal of countering the misuse of commercial spyware. This alliance is committed to establishing robust guardrails and procedures that uphold fundamental human rights, civil liberties, and the rule of law, within each of their respective systems.
While this signals discomfort with foreign-made spyware, no one should take this as an indication that the U.S. government is averse to using similar technologies developed internally, or indeed acquiring foreign spyware companies for domestic use. Given the government’s long history of using and abusing incredibly invasive techniques, people in the United States should push for robust human rights safeguards to ensure the government won’t proceed with only the minor restrictions of this executive order to rein them in.
Be Skeptical of FBI Warnings About Phone Chargers Every few years, an unsourced report circulates that “the FBI says plugging into public charging kiosks is dangerous.” Here’s why you should ignore the freakout and install software updates regularly.
Your phone is designed to communicate safely with lots of things – chargers , web sites, Bluetooth devices such as earbuds or speakers, Wi-Fi, and even other phones, for instance when sending and receiving text messages. If doing any of these normal phone things can give your phone malware, that is a security vulnerability (which is a type of bug).
Security vulnerabilities happen with some frequency. That is why your phone prompts you to update your software so often – the makers of its software find out about bugs and fix them.
So, when you hear a report that public chargers are giving people malware, you should ask “what is the vulnerability being used, and when will it be fixed?” as well as “how widespread is the problem? How many people are affected?” Unfortunately, the periodic reports of “juice jacking” never have such details, usually because they are recycled from earlier reports which themselves lack details.
The most recent news reports reference a tweet from the FBI Denver field office. According to reporter Dan Goodin’s conversation with an FBI spokesperson, the field office relied on an article the FCC published in 2019 warning about USB charging stations. The only source for that article was a warning from the Los Angeles County District Attorney’s Office that did not itself allege any specific bug or specific instances of charging stations being used for attacks. The FCC later quietly removed the sourcing from its article, allowing itself to be incorrectly treated as a primary source for juice jacking claims.
While the video from the LA County D.A. doesn’t mention it, the ultimate source for the term “juice jacking” is a Brian Krebs article from 2011 reporting on a vulnerability demonstrated at DEFCON that year. As you can imagine, phone security has changed dramatically since 2011. And so far there have been no reports of widespread exploitation of USB vulnerabilities in the wild.
As a complex protocol, USB does present a large attack surface– and there are some built-in risks, like the ability for a USB device to pretend to be a keyboard (so lock your phone while charging). You may also want to bring your own charger or battery for electrical reasons. Phone manufacturers often recommend charging only with approved chargers, to avoid charging too slow or (worse) too fast, and potentially damaging your phone or battery. But realistic security is about risk management, and for most people the risk of a public USB charger is very low.
Undoubtedly there will continue to be bugs in phones’ USB stacks in the future, just as there will be bugs in web browsers and chat apps. Some of those bugs will have the potential to infect your phone with malware, particularly if large numbers of people forget to update their software. But with a little skepticism and common sense, we can stop zombie scaremongering about charging stations from making the rounds again.
-
 14:38
14:38
What If Everything You Were Taught Was A Lie?
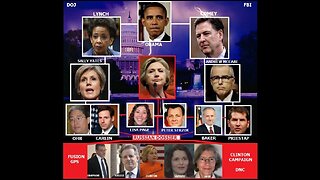
1 year agoWhy U.S.A. Government CIA-DOJ-FBI-Etc. Killing Thousands Whistleblowers Dead ?
4.66K13 -
 3:57
3:57
TrueLoveFaith
1 year agoEXPOSING THE CORRUPTION TOP TO BOTTOM DOJ,CIA,FBI,ETC,ETC - MORE BELOW
457 -
 8:47
8:47
Top Usa NEWS FEEDER
1 year agoCommentary: From What, Exactly, Is the FBI Protecting Us?
1961 -
 4:27
4:27
galacticstorm
3 months agoREESE REPORT | CIA Admits To Instigating War With Russia
4361 -
 6:00
6:00
The Resistance
3 months agoCIA Admits To Instigating War With Russia
198 -
 3:04:02
3:04:02
Common [CENSORED]: An America First Podcast
4 months agoEp.90 CIA MASTERMINDED RUSSIA HOAX TO ATTACK TRUMP, INSIDER EXPOSES FBI AGITATION PROGRAM USED ON J6
755 -
 5:58
5:58
NAZIworldORDER - NWO - SECRET SOCIETIES, ILLUMINATI, GREAT RESET
1 year agoUNITED STATES OF TERROR - Do you believe that the corrupt U.S Government & CCP China are enemies?
10.9K15 -
 1:03:34
1:03:34
MyCatholicRedPill
1 year ago11.23.22: The J@B info is going VIRAL! People cry for FREEDOM from IRAN/BRAZIL! PED@s exposed! PRAY!
316 -
 2:59:16
2:59:16
EXPOSE the PEDOS end of the CABAL
1 year agoInside The CIA - On Company Business (1980)
4.97K5 -
 40:30
40:30
MyCatholicRedPill
4 months agoThe U.S. Govt. Can Legally Kill Us - The 2nd Largest PSYOP in the Past 120 Years!
2.66K2