Premium Only Content
This video is only available to Rumble Premium subscribers. Subscribe to
enjoy exclusive content and ad-free viewing.
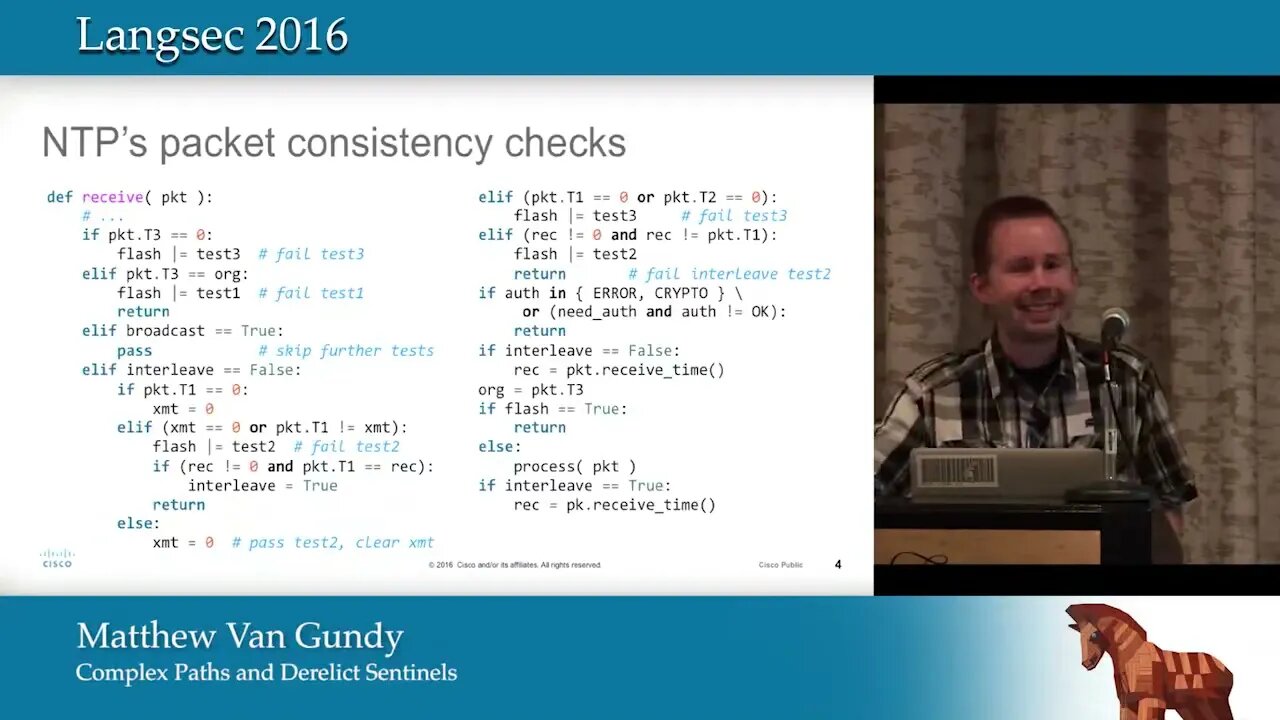
Complex Paths and Derelict Sentinels software engineering underpinnings of NTP vulnerabilities
Loading comments...
-
 29:08
29:08
Afshin Rattansi's Going Underground
1 day agoCol. Lawrence Wilkerson: World War 3 is ALREADY HERE, Netanyahu is INTENT on Greater Israel
4.41K11 -
 LIVE
LIVE
SpartakusLIVE
4 hours agoNONSTOP Snipes, Rockets, and BICEPS = Monday MOTIVATION
411 watching -
 LIVE
LIVE
Rallied
5 hours ago $1.96 earnedSolo Challenges All Day
290 watching -
 LIVE
LIVE
Flyover Conservatives
8 hours agoIs AI Actually Alien Intelligence? Dr. Jason Dean Exposes the Dark Side | FOC Show
414 watching -
 1:47:36
1:47:36
Glenn Greenwald
5 hours agoJD Vance and Rand Paul Clash on Due Process: War on Terror Echoes; Has the U.S. Given Up on Confronting China? Ben Shapiro's Latest Falsehoods About Israel | SYSTEM UPDATE #510
83K57 -
 LIVE
LIVE
RaikenNight
2 hours ago $0.14 earnedExploring the Galaxy of No Mans Sky
77 watching -
 LIVE
LIVE
Spartan
4 hours agoRanked and Expedition 33 (NG+4 and all enemies Set to 10x health)
63 watching -
 LIVE
LIVE
Jokeuhl Gaming and Chat
7 hours agoDARKTIDE - Warhammer 40k w/ Nubes and AoA
99 watching -
 2:19:56
2:19:56
Nerdrotic
14 hours ago $3.03 earnedNerdrotic Nooner 513
40.1K2 -

BigTallRedneck
3 hours agoRANKED FINALS W OMEGA
12.3K