Premium Only Content
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
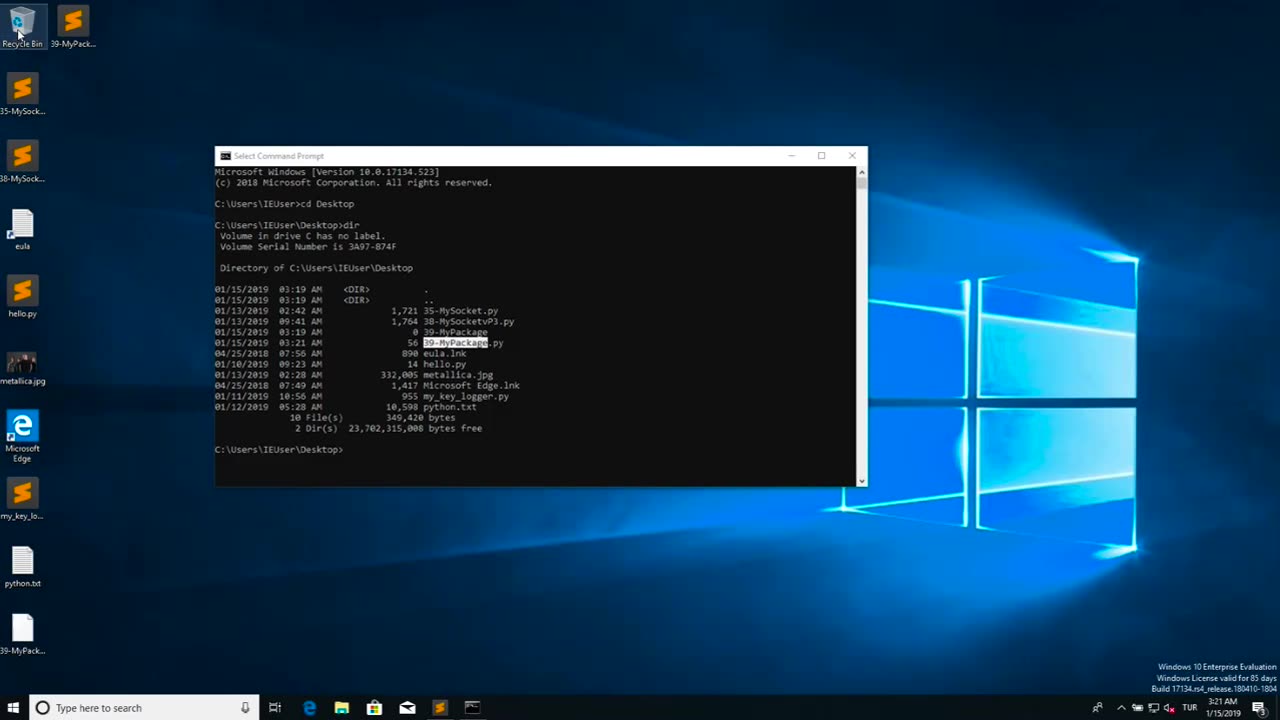
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
TimcastIRL
1 hour agoVP Says No Unity With Democrats Celebrating Charlie Kirk Assassination, Left Confirmed | Timcast IRL
22,468 watching -
 LIVE
LIVE
Katie Miller Pod
22 minutes agoEpisode 6 - Attorney General Pam Bondi | The Katie Miller Podcast
483 watching -
 LIVE
LIVE
Barry Cunningham
1 hour agoFOR PRESIDENT TRUMP WILL TAKE NO PRISONERS AND THE LIBS SHOULD EXPECT NO MERCY!
2,549 watching -
 1:09:26
1:09:26
Glenn Greenwald
3 hours agoTrump's Shifting Immigration and H-1B Policies: With Journalist Lee Fang and Political Science Professor Ron Hira | SYSTEM UPDATE #515
112K8 -
 LIVE
LIVE
The Jimmy Dore Show
2 hours agoEmmy Winners DEMAND Israel Stop the Genocide! Charlie Kirk’s LAST INTERVIEW Before His Death!
5,019 watching -
 LIVE
LIVE
LFA TV
22 hours agoLFA TV ALL DAY STREAM - MONDAY 9/15/25
916 watching -
 54:12
54:12
Donald Trump Jr.
2 hours agoCharlie's Vision. Our Future. | TRIGGERED Ep274
143K93 -
 1:03:35
1:03:35
BonginoReport
3 hours agoKirk’s Alleged Killer Dating Hateful Transgender??? - Nightly Scroll w/ Hayley Caronia (Ep.134)
80.4K94 -
 1:01:12
1:01:12
The Nick DiPaolo Show Channel
5 hours agoKirk Assassination Exposes Insane Left | The Nick Di Paolo Show #1793
50.7K15 -

The Mike Schwartz Show
4 hours agoTHE MIKE SCHWARTZ SHOW Evening Edition 09-15-2025
24.1K10