Premium Only Content
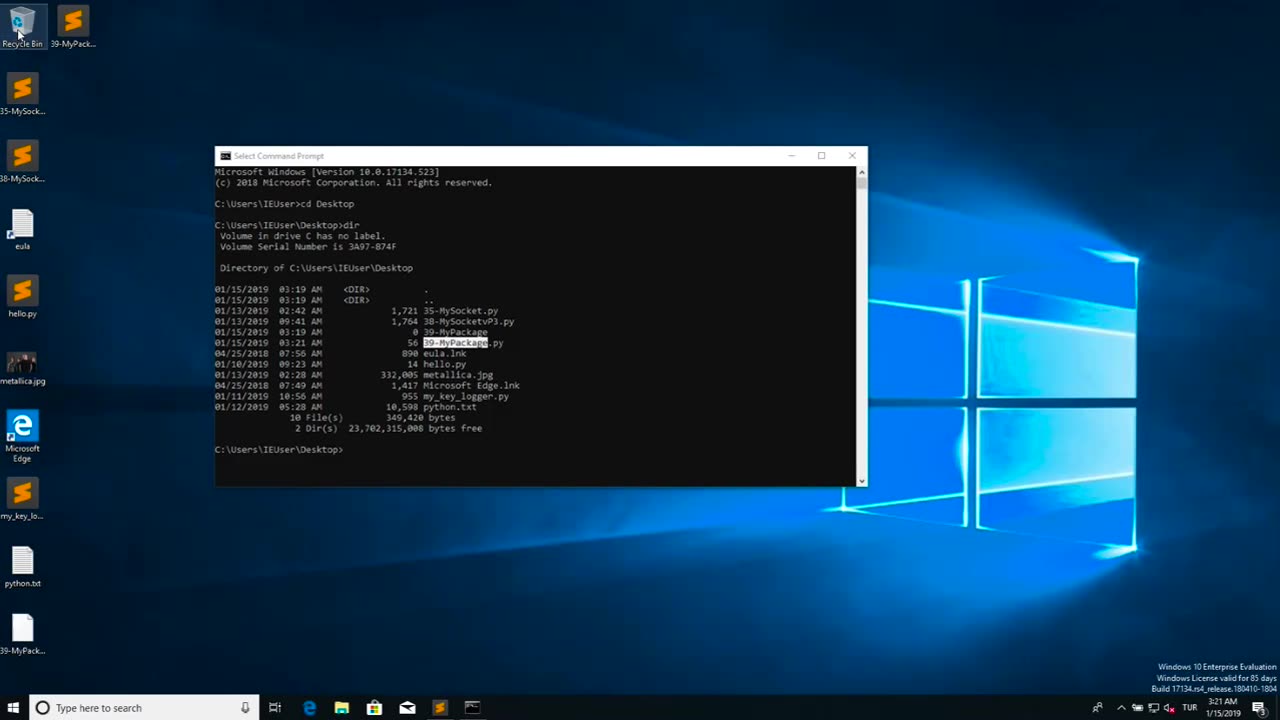
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Russell Brand
2 hours agoTrump Goes NUCLEAR on China - accuses Xi of CONSPIRING against US with Putin & Kim - SF627
17,316 watching -
 LIVE
LIVE
Dr Disrespect
2 hours ago🔴LIVE - DR DISRESPECT - METAL EDEN - NEW 2025 SCI-FI FPS LAUNCH STREAM
1,397 watching -
 LIVE
LIVE
Sean Unpaved
1 hour agoTrey Wingo's Gridiron Grab
201 watching -
 1:06:28
1:06:28
Timcast
2 hours agoTrump Admin Threatens GOP Who Vote To Release Epstein Files
109K58 -
 LIVE
LIVE
Side Scrollers Podcast
3 hours agoDruski/White Face Controversy + Women “Experience Guilt” Gaming + More | Side Scrollers Live
402 watching -
 1:39:53
1:39:53
The Mel K Show
2 hours agoMORNINGS WITH MEL K - Narratives Implode as Light Shines on Covid Deception 9-3-25
7.48K3 -
 LIVE
LIVE
The Shannon Joy Show
1 hour agoExclusive With Congressman Tom Massie: "The Epstein Files Are NOT A Hoax. There Are Real Victims"
249 watching -
 1:52:46
1:52:46
Steven Crowder
4 hours agoCongress Drops New Epstein Files and Trump Drops New Bombs on Venezuela Terrorists
263K147 -
 1:10:39
1:10:39
The Rubin Report
3 hours agoCNN Host Actually Thought She'd Outsmarted Shapiro, Until He Asked This
52.8K38 -
 1:02:00
1:02:00
VINCE
5 hours agoThe Left's Demented Fantasies Shatter | Episode 117 - 09/03/25
193K117