Premium Only Content
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
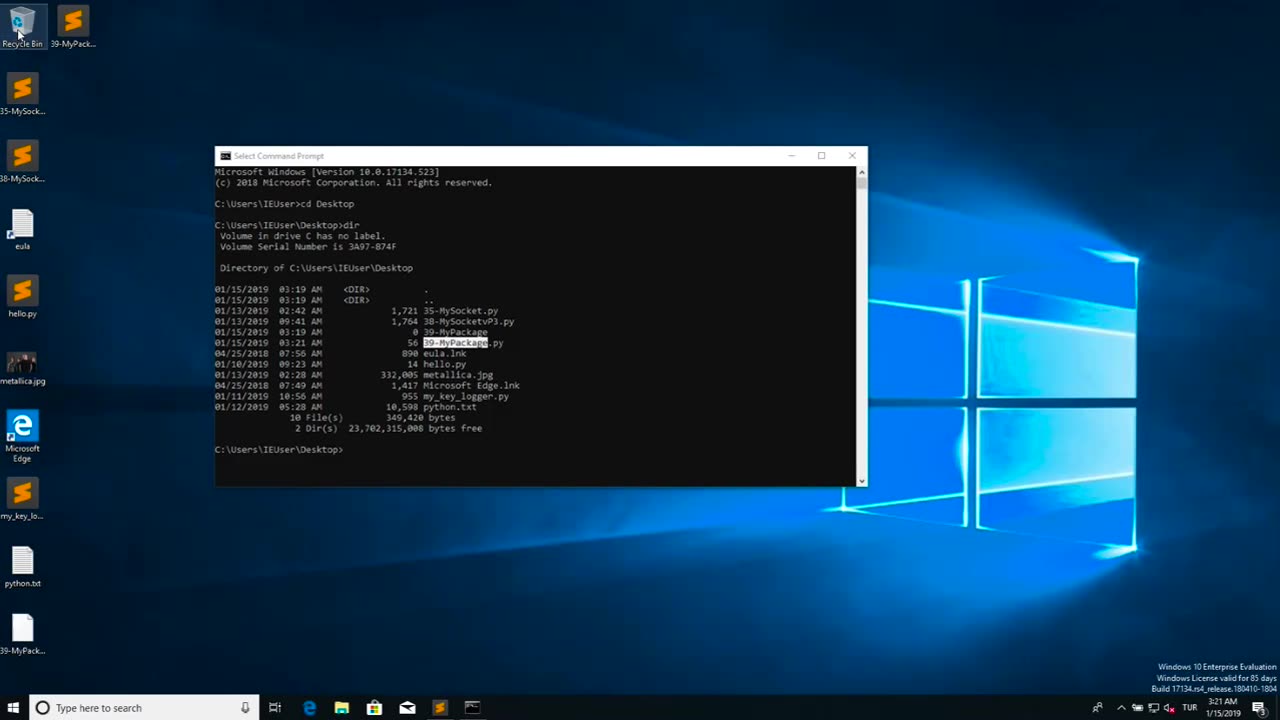
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
The Charlie Kirk Show
2 hours agoJUDGMENT DAY 2025: The Election Results Stream
10,286 watching -
 LIVE
LIVE
MattMorseTV
3 hours ago $13.82 earned🔴Election Day LIVE COVERAGE.🔴
2,088 watching -
 LIVE
LIVE
Professor Nez
5 hours ago🚨ELECTION NIGHT 2025 LIVE! Massive Upsets Brewing in New York, New Jersey & Virginia!
128 watching -
 LIVE
LIVE
Due Dissidence
8 hours agoLIVE: ELECTION RESULTS From NYC, NJ, and VA - Trump Approval CRATERS, Kash's Private Jet CRASH OUT
1,235 watching -
 12:50
12:50
Demons Row
1 hour agoBikers of New Jersey 💀🏍️ Pagans, Thunder Guards, and Thug Riders
7 -
 42:31
42:31
Stephen Gardner
4 hours ago🔥Old Obama Video RESURFACES - His Own Words CONDEMNED Him! Trump Gains MASSIVE Momentum!!
5.33K12 -
 LIVE
LIVE
LFA TV
23 hours agoLIVE & BREAKING NEWS! | TUESDAY 11/4/25
580 watching -
 1:03:37
1:03:37
BonginoReport
3 hours agoElection Night Showdown Spotlight - Nightly Scroll w/ Hayley Caronia (Ep.170)
82.8K20 -
 LIVE
LIVE
Edge of Wonder
3 hours agoSupernatural Forces & Giants Built Great Pyramid of Egypt
191 watching -
 1:24:03
1:24:03
Kim Iversen
4 hours agoAn Islamist Socialist in NYC? The Panic Is Epic | Neocons To Tucker: 'Love Israel OR ELSE'
72.1K94