Premium Only Content
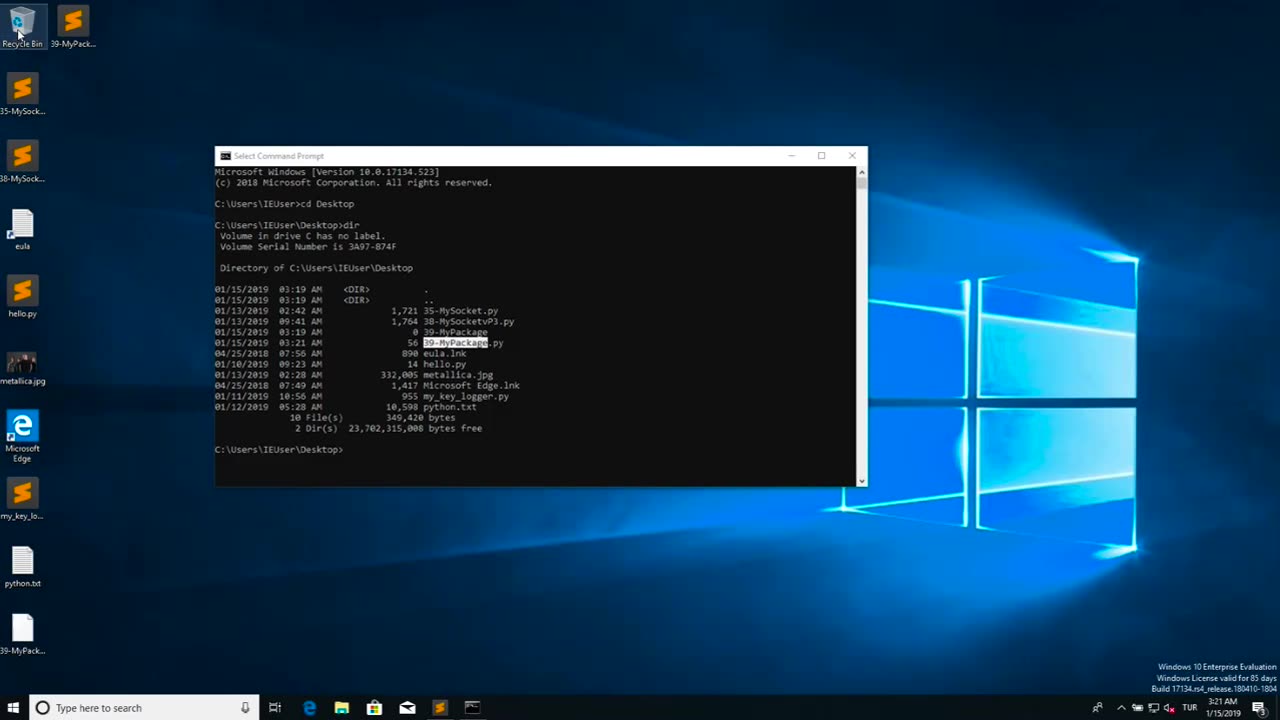
Chapter-39, LEC-2 | Malicious Files | #ethicalhacking #maliciousdiles #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
Malicious files refer to digital files, such as software programs or documents, that are intentionally designed to harm or compromise the security of a computer, network, or device. These files may contain malicious code, also known as malware, which can be executed or triggered to perform malicious activities without the knowledge or consent of the user.
Malicious files can come in various forms, including viruses, worms, Trojans, ransomware, spyware, adware, and other types of malware. They are typically disguised as legitimate files or software to deceive users into downloading or executing them. Once the malicious file is executed or opened, it can spread throughout the system, exploit vulnerabilities, steal sensitive information, disrupt operations, or cause other types of damage.
Malicious files are often distributed through various means, such as infected email attachments, compromised websites, infected USB drives, social engineering tactics, and other methods. They can target any type of device or operating system, including computers, servers, smartphones, tablets, and IoT (Internet of Things) devices.
The consequences of encountering and executing malicious files can be severe, ranging from data breaches and financial loss to privacy violations, system downtime, and reputational damage. Therefore, it is crucial to implement robust cybersecurity measures, such as using antivirus software, keeping software and systems updated, being cautious while downloading or opening files, and practicing safe online behavior, to protect against malicious files and other cyber threats.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
TheSaltyCracker
56 minutes agoIt's Over Zelensky ReeEEStream 11-21-25
9,338 watching -
 1:03:56
1:03:56
Glenn Greenwald
3 hours agoIs MAGA Divided? Revisiting the Major Controversies on the Right
25.4K18 -
 LIVE
LIVE
Mally_Mouse
21 hours ago🎮 Let's Play!!: Stardew Valley pt. 33
151 watching -
 33:09
33:09
Exploring With Nug
2 hours agoThey Weren’t Ready for Nightfall on Blood Mountain… So I Helped Them Down
118 -
 1:11:24
1:11:24
The Daily Signal
3 hours ago🚨BREAKING: Democrat Steals $5 Million from FEMA, Trump-Mamdani Meeting Gets Bizarre
274 -
 1:02:11
1:02:11
BonginoReport
4 hours agoJ.D. Vance Threatens to Kill JD Vance?! - Nightly Scroll w/ Hayley Caronia (Ep.183)
79.7K27 -
 3:09:50
3:09:50
Nerdrotic
15 hours ago $9.49 earnedWarner Bros Fire Sale! | Last Ronin CANNED | WICKED For Good REVIEW - Friday Night Tights 381
27.2K9 -
 LIVE
LIVE
Akademiks
2 hours agoMeg Thee Stallion Back LYING again? Offset vs Finesse2x. 6ix9ine house robbed.. HERES WHO DID IT
900 watching -
 LIVE
LIVE
SpartakusLIVE
2 hours agoFriday Night HYPE w/ YOUR King of Content
140 watching -
 LIVE
LIVE
Blabs Life
1 hour agoPeter Jackson's King Kong: The Official Game of the Movie | Noob Plays
85 watching