Premium Only Content
Chapter-38, LEC-11 | Sending Commands With List | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
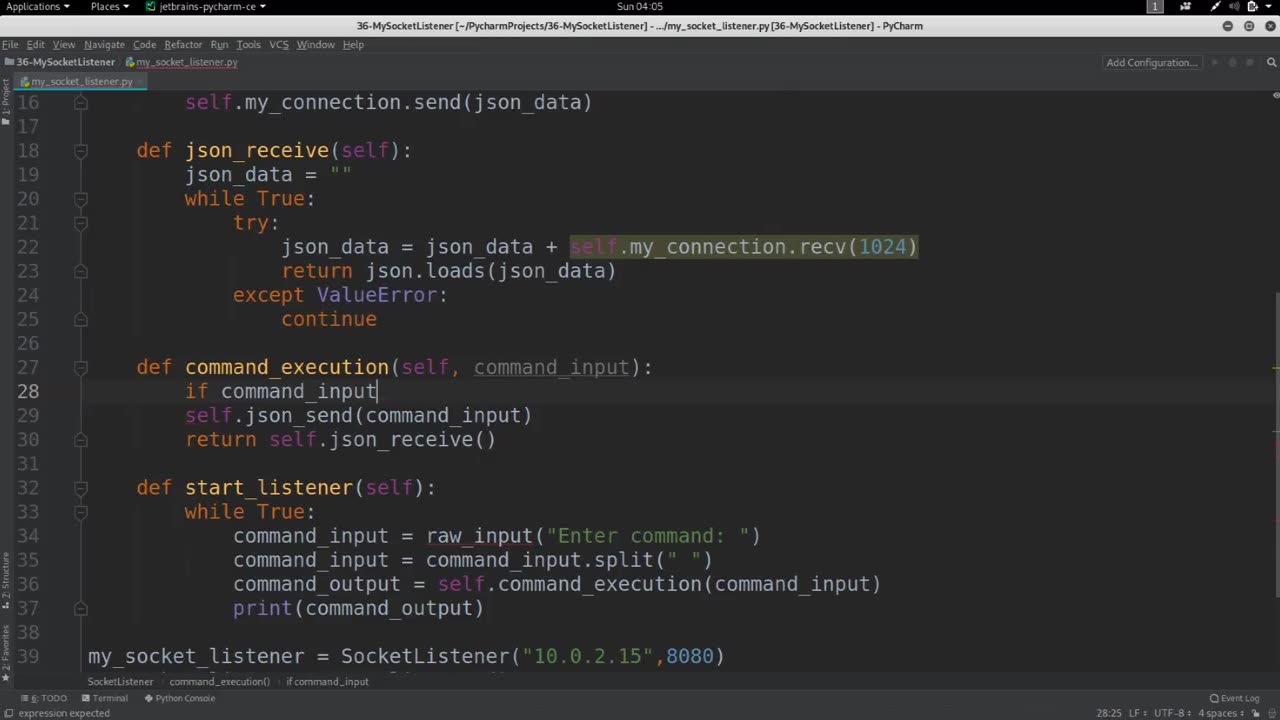
Sending commands with a list refers to the practice of sending a list of commands or instructions from one system or application to another for execution or processing. This can be done in various contexts, such as in computer programming, automation, or remote communication between systems.
When sending commands with a list, a typical workflow may involve the following steps:
Creating a list: A list is created to store the commands or instructions that need to be sent. A list is a data structure that can hold multiple items or elements in a specific order, and it can be of fixed or dynamic size depending on the programming language or application being used.
Adding commands to the list: Commands or instructions are added to the list, typically as individual elements. These commands can be represented as strings, objects, or any other data type that is appropriate for the specific application or system. The list can be modified by appending, inserting, or updating elements as needed.
Sending the list: The list of commands is then sent or transmitted to the receiving system or application. This can be done through various communication methods, such as APIs, sockets, HTTP requests, or other protocols depending on the system architecture and requirements.
Receiving and processing the list: The receiving system or application retrieves the list of commands and processes each command sequentially or in parallel, depending on the implementation. The commands are executed or interpreted according to their intended purpose, which could be performing actions, making decisions, updating data, or triggering specific functionalities.
Error handling: Proper error handling techniques should be implemented to handle any potential errors that may occur during the sending or processing of the list of commands. This can include checking for invalid commands, handling timeouts, managing exceptions, and providing appropriate feedback or error messages to the sender or end users.
Sending commands with a list can be a powerful way to communicate and automate tasks between systems or applications. It allows for flexibility in specifying multiple commands in a single transmission, enabling efficient and streamlined communication and automation workflows. Properly designing and implementing the list of commands, along with robust error handling, can help ensure reliable and secure command execution in various systems and applications.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Grant Stinchfield
1 hour agoThe Mind Meltdown: Are COVID Shots Fueling America’s Cognitive Collapse?
134 watching -
 1:00:46
1:00:46
VINCE
4 hours agoThe Proof Is In The Emails | Episode 161 - 11/04/25
146K115 -
 2:12:22
2:12:22
Benny Johnson
2 hours ago🚨Trump Releases ALL Evidence Against James Comey in Nuclear Legal BOMBSHELL! It's DARK, US in SHOCK
77.7K26 -
 2:04:05
2:04:05
Badlands Media
11 hours agoBadlands Daily: November 4, 2025
58.6K8 -
 2:59:49
2:59:49
Wendy Bell Radio
7 hours agoBUSTED.
71.6K83 -
 1:15:01
1:15:01
The Big Mig™
4 hours agoDing Dong The Wicked Witch Pelosi Is Gone
12.3K6 -
 34:57
34:57
Daniel Davis Deep Dive
3 hours agoFast Tracking Weapons to Ukraine, Close to $3 Billion /Lt Col Daniel Davis
16.9K7 -
 DVR
DVR
The State of Freedom
5 hours ago#347 Relentlessly Pursuing Truth, Transparency & Election Integrity w/ Holly Kesler
10.9K -
 1:34:34
1:34:34
Graham Allen
4 hours agoThe MAGA “Civil War” Will LOSE The Midterms! Is A Fracture Coming? ALL Eyes On Key Races!
89.7K44 -
 20:28
20:28
Real Estate
1 month ago $1.34 earnedMILLIONS of Homeowners ARE LOSING MONEY NOW...
18K3