Premium Only Content
Chapter-38, LEC-5 | Writing Listener | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
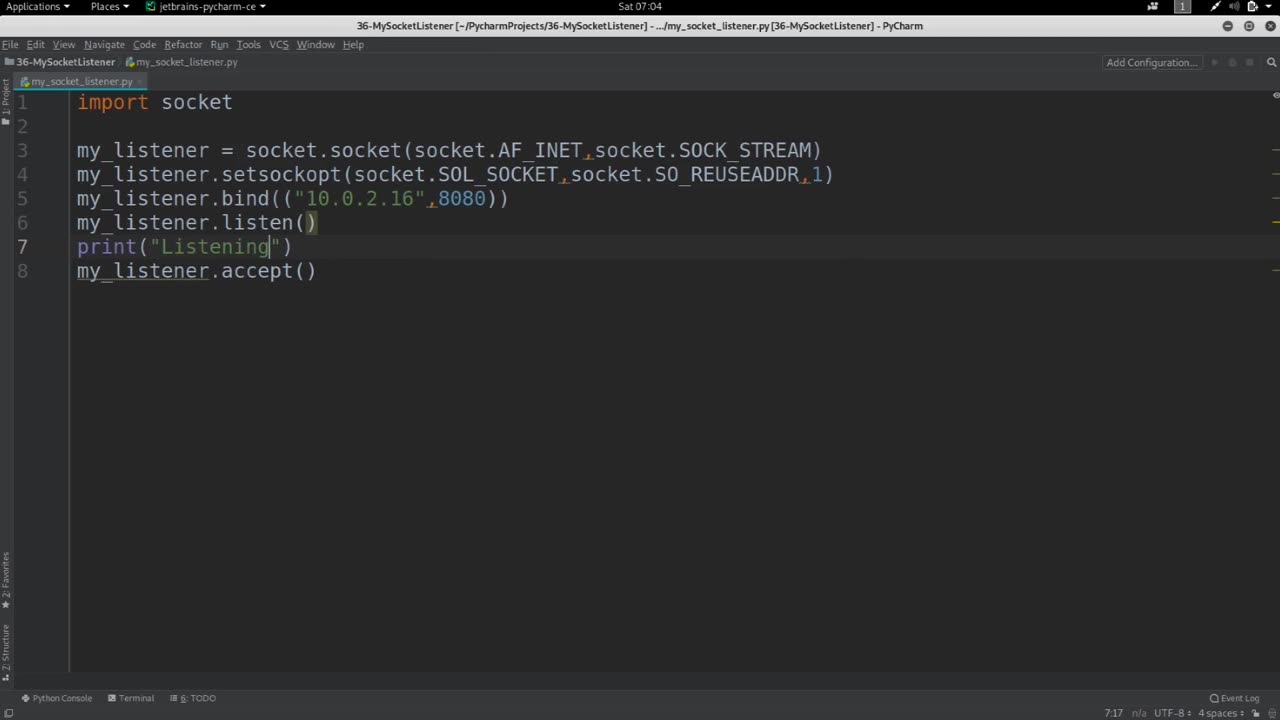
A listener typically refers to a software component or module that is designed to capture, collect, and analyze data from communication channels, such as network traffic, audio streams, or other forms of communication. Listeners can be used for legitimate purposes, such as network monitoring, debugging, or lawful interception for authorized law enforcement purposes.
When writing a listener, it is crucial to ensure that it is done within the boundaries of applicable laws, regulations, and ethical guidelines. Unauthorized interception or monitoring of communication channels, including private conversations, network traffic, or any form of communication, is considered unethical and illegal in most jurisdictions.
If you are interested in developing a listener for legitimate purposes, such as for network monitoring, debugging, or other lawful interception purposes, it is essential to obtain proper authorization from the relevant parties, follow applicable laws and regulations, and adhere to ethical guidelines. This may include obtaining written consent from all parties involved, ensuring proper data protection and privacy measures are in place, and complying with relevant legal requirements.
It is important to use your skills and knowledge in a responsible and ethical manner, and always respect the privacy and security of others' communication channels and data. If you have any questions or concerns about writing a listener, it is recommended to seek legal and ethical guidance from qualified professionals to ensure compliance with applicable laws and ethical standards.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
JuicyJohns
2 hours ago $2.67 earned🟢#1 REBIRTH PLAYER 10.2+ KD🟢
157 watching -
 LIVE
LIVE
Nikko Ortiz
28 minutes agoLive - News, Politics, Podcast And Naaah Im Playin We Chillen
82 watching -
 44:07
44:07
The Quiet Part
1 hour agoThey Fear People Who Remember—The Truth About Freedom, Health Care & Canada
1.05K -
 LIVE
LIVE
Wendy Bell Radio
5 hours agoDemocrats Are In Total Free Fall
7,907 watching -
 54:23
54:23
Dialogue works
2 days ago $1.25 earnedAndrei Martyanov: Putin Beating Trump at His Own Game - Can Israel Survive a War W/ Iran W/o the US?
21.1K7 -
 LIVE
LIVE
LFA TV
3 hours agoLFA TV ALL DAY STREAM - MONDAY 8/18/25
3,800 watching -
 58:23
58:23
JULIE GREEN MINISTRIES
3 hours agoJUDGEMENT IN DC IS ABOUT TO INTENSIFY
98.3K174 -
 1:27:39
1:27:39
Chicks On The Right
4 hours agoTrump & Putin Summit, Newsom’s 2028 Dreams, and Kamala's Drunk Rant | Chicks on the Right
27.3K4 -
 2:02:30
2:02:30
Welcome to the Rebellion Podcast
20 hours ago $1.36 earnedA Case of the MonJays - WTTR Podcast Live 8/18
27.6K1 -
 4:01:59
4:01:59
The Bubba Army
3 days agoZelensky SLAMS Trump-Putin Meeting - Bubba the Love Sponge® Show | 8/18/25
44.9K8