Premium Only Content
Chapter-36, LEC-7 | Protecting Overselves | #ethicalhacking #hacking
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
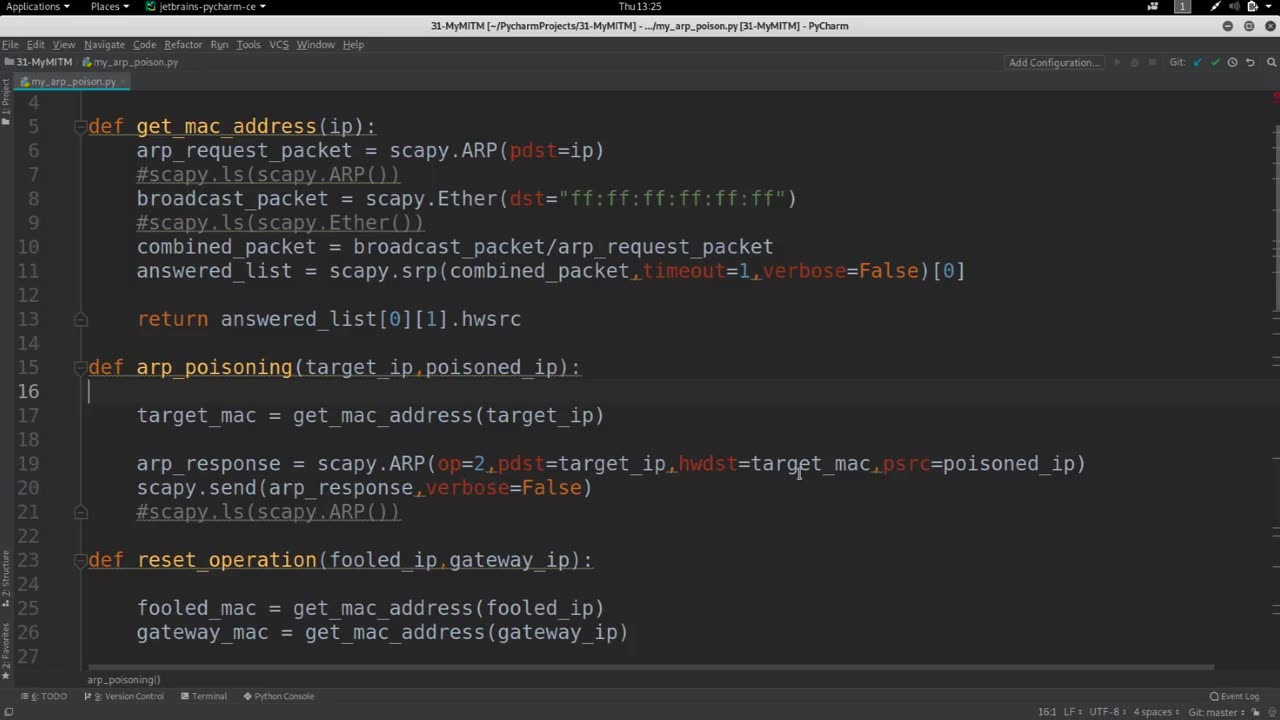
Protecting ourselves refers to taking measures and precautions to safeguard our personal information, privacy, and security in various aspects of our lives, including online activities, physical security, and data protection. With the increasing prevalence of digital technologies and the internet, protecting ourselves has become crucial to prevent potential risks and threats, such as identity theft, data breaches, cyber attacks, physical harm, and financial loss.
Protecting ourselves involves adopting good security practices and being vigilant in our daily activities. This can include:
Securing online accounts: Using strong and unique passwords for each online account, enabling two-factor authentication (2FA), and being cautious of phishing attempts and social engineering attacks to prevent unauthorized access to our online accounts.
Being mindful of personal information: Being cautious about sharing personal information online, including on social media, and being aware of the privacy settings and permissions of the apps and platforms we use.
Keeping devices and software updated: Regularly updating our operating systems, apps, and software with the latest security patches and fixes to protect against known vulnerabilities.
Using encryption and secure communication: Using encryption technologies, such as HTTPS for websites, and virtual private networks (VPNs) for secure communications, especially when accessing sensitive information or using public Wi-Fi networks.
Being cautious with emails and attachments: Avoiding opening suspicious emails or attachments, and being cautious of phishing emails or emails from unknown sources that may contain malware or viruses.
Protecting physical security: Locking our doors and windows, using security systems and surveillance cameras, and being cautious with strangers or suspicious activities in our physical surroundings.
Being mindful of social media and online presence: Being cautious about the information we share on social media, being mindful of our online presence, and adjusting privacy settings to control what information is visible to others.
Backing up important data: Regularly backing up important files and data to prevent loss due to data breaches, hardware failure, or other unforeseen events.
Educating ourselves about cybersecurity: Staying informed about the latest cybersecurity threats, trends, and best practices through reliable sources, and educating ourselves and our family members about safe online practices.
Protecting ourselves requires a proactive approach, constant vigilance, and staying informed about the evolving landscape of cybersecurity threats. By taking steps to protect our personal information, privacy, and security, we can minimize the risks of becoming victims of cybercrime and other security breaches.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
The Charlie Kirk Show
19 minutes agoJUDGMENT DAY 2025: The Election Results Stream
3,317 watching -
 DVR
DVR
Kim Iversen
2 hours agoAn Islamist Socialist in NYC? The Panic Is Epic | Neocons To Tucker: 'Love Israel OR ELSE'
58.3K65 -
 LIVE
LIVE
MattMorseTV
1 hour ago🔴Election Day LIVE COVERAGE.🔴
1,263 watching -
 1:05:56
1:05:56
vivafrei
2 hours agoComey Doubles Down, Prosecution Doubles Up! Election Day Madness! Boasberg Impeachment & MORE!
21.2K6 -
 LIVE
LIVE
SpartakusLIVE
1 hour agoNEW Meta = EPIC WINS on Battlefield 6 - REDSEC
111 watching -
 DVR
DVR
StoneMountain64
4 hours agoBattlefield REDSEC leveling guns for attachments
29.6K1 -
 26:19
26:19
Liberty Hangout
4 days agoAnti-Trumpers Make Up Bizarre Theories
9.16K27 -
 LIVE
LIVE
GritsGG
5 hours agoWorld Record Win Streak Attempt! #1 Most Wins 3880+!
46 watching -
 LIVE
LIVE
The Rabble Wrangler
15 hours agoBattlefield with The Best in the West
61 watching -
 13:56
13:56
Cash Jordan
2 hours ago"OPEN BORDERS" Mob BATTERS Portland Jail… 'COMBAT' Marines DEFY Judge, BREAK BONES
4.92K7