Premium Only Content
Chapter-36, LEC-5 |Working With Layers | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
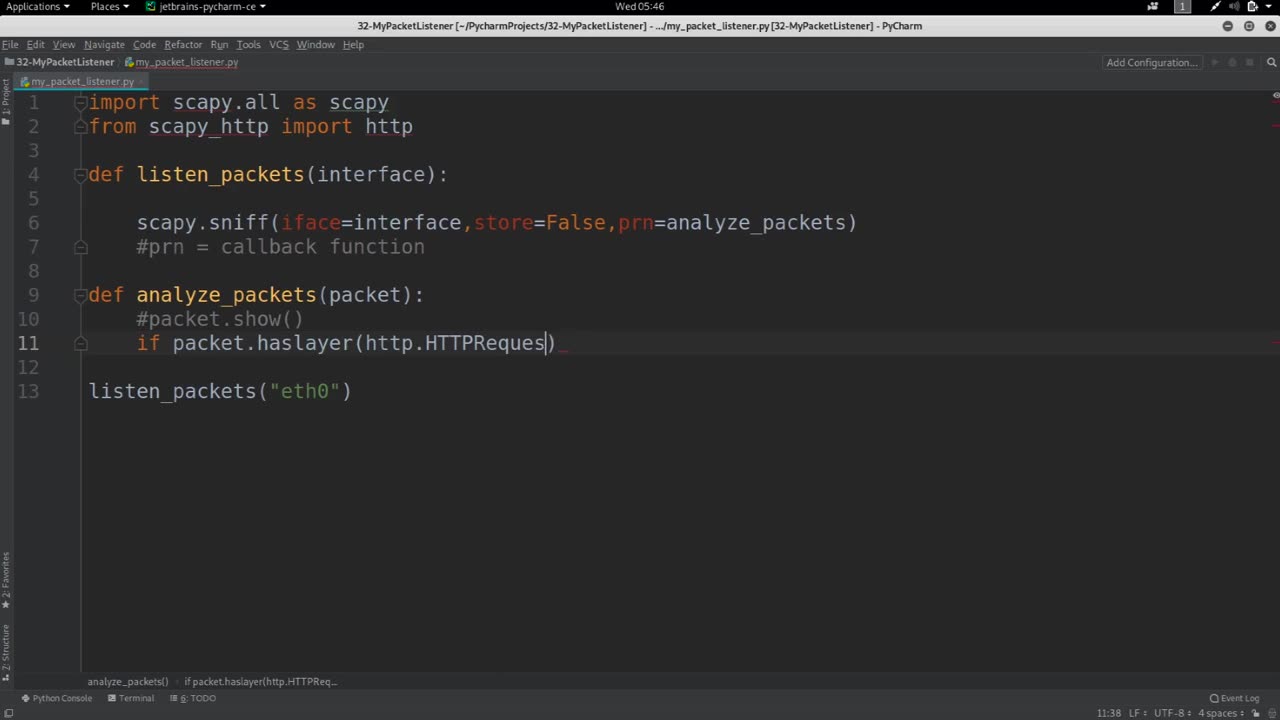
Working with layers refers to the process of analyzing and understanding the different layers of the OSI (Open Systems Interconnection) model or the TCP/IP (Transmission Control Protocol/Internet Protocol) model, which are two commonly used models for understanding and organizing network communication protocols.
The OSI model and the TCP/IP model both divide the complex process of network communication into multiple layers, each with its own specific functions and responsibilities. Understanding these layers and how they interact with each other is crucial for network administrators, engineers, and analysts to effectively troubleshoot, diagnose, and optimize network performance.
Here's a general overview of the layers in the OSI model and the TCP/IP model:
OSI Model:
1. Physical Layer: This is the lowest layer and deals with the physical transmission of data over the network, such as the electrical, mechanical, and physical characteristics of the network medium, such as cables, switches, and hubs.
2. Data Link Layer: This layer is responsible for establishing and maintaining reliable communication links between adjacent network nodes, such as switches and bridges. It also handles error detection and correction at the data link level.
3. Network Layer: This layer provides routing and addressing functions to establish communication between different networks. It determines the optimal path for data packets to reach their destination and handles logical addressing, such as IP addresses.
4. Transport Layer: This layer is responsible for ensuring reliable communication between end-to-end devices, such as computers or servers. It provides mechanisms for segmentation, flow control, error recovery, and reassembly of data.
5. Session Layer: This layer establishes, maintains, and terminates sessions between applications running on different devices. It also manages session synchronization and recovery in case of failures.
6. Presentation Layer: This layer is responsible for data representation and translation, such as converting data into a format that can be understood by different systems. It also handles encryption, compression, and other data formatting tasks.
7. Application Layer: This is the topmost layer and provides the interface between the network and the applications running on end devices. It includes protocols for specific applications, such as HTTP for web browsing, SMTP for email, and FTP for file transfer.
TCP/IP Model:
1. Link Layer: This layer is similar to the OSI Data Link Layer and is responsible for the physical transmission of data over the network medium.
2. Internet Layer: This layer is similar to the OSI Network Layer and handles routing, addressing, and packet fragmentation for data packets to travel across different networks.
3. Transport Layer: This layer is similar to the OSI Transport Layer and provides reliable communication between end-to-end devices, such as computers or servers, using protocols like TCP (Transmission Control Protocol) or UDP (User Datagram Protocol).
4. Application Layer: This layer is similar to the OSI Application Layer and includes protocols for specific applications, such as HTTP, SMTP, FTP, and DNS (Domain Name System).
Working with layers involves understanding the functions, protocols, and interactions of each layer, as well as how they impact the overall network communication. It requires knowledge of network protocols, network devices, and network topologies, and it is essential for troubleshooting network issues, optimizing network performance, and ensuring secure and efficient network communication.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-

ThisIsDeLaCruz
46 minutes agoBack Stage Pass with Avenged Sevenfold
762 -
 LIVE
LIVE
Tundra Tactical
3 hours agoProfessional Gun Nerd Plays Battlefield 6
71 watching -
 1:01:12
1:01:12
Donald Trump Jr.
5 hours agoThe China Matrix with Journalist Lee Smith | TRIGGERED Ep.288
105K71 -
 LIVE
LIVE
MattMorseTV
2 hours ago🔴Trump's '60 Minutes' INTERVIEW + MUCH MORE.🔴
1,331 watching -
 LIVE
LIVE
Dr Disrespect
10 hours ago🔴LIVE - DR DISRESPECT - ARC RAIDERS - FULL SEND INTO THE RED
1,138 watching -
 1:02:08
1:02:08
BonginoReport
4 hours agoNicki Minaj Speaks Out Against Christian Persecution - Nightly Scroll w/ Hayley Caronia (Ep.169)
37.7K23 -
 LIVE
LIVE
SpartakusLIVE
4 hours agoSNIPING in Battlefield 6 - REDSEC || Monday MOTIVATION to CONQUER the Week
143 watching -
 LIVE
LIVE
Nerdrotic
2 hours ago $2.05 earnedNerdrotic At Night 531
280 watching -
 LIVE
LIVE
The Jimmy Dore Show
3 hours agoTrump Threatens to INVADE Nigeria! Kash Patel CRASHES OUT Over Jet Use Criticism!
7,469 watching -
 LIVE
LIVE
Conductor_Jackson
22 hours agoLet's Play Unrailed 2 Solo! 🚂🚂🚂🚂🚂🚂
11 watching