Premium Only Content
Chapter-36, LEC-3 | Wireshark Analysis | #ethicalhacking #hacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
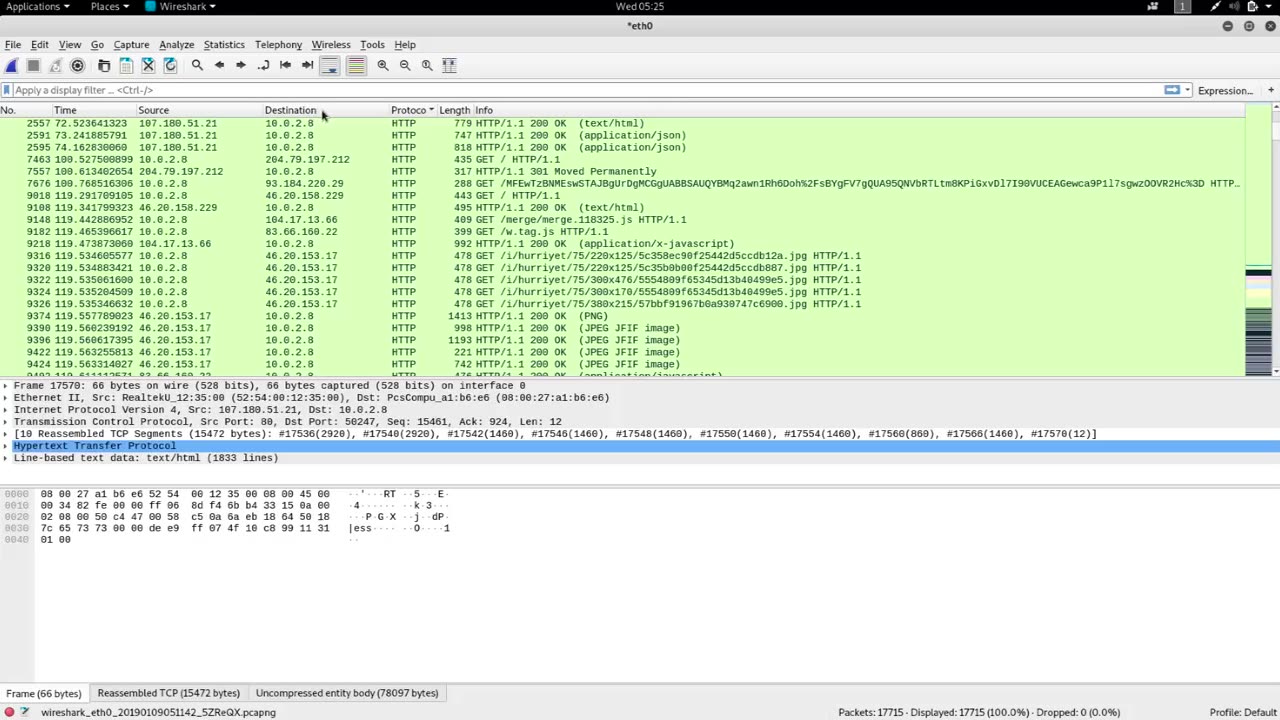
Wireshark Analysis is a powerful and popular open-source network protocol analyzer that allows network analysts to capture, inspect, and analyze network traffic in real-time. Wireshark is widely used in various network-related scenarios, such as network troubleshooting, performance analysis, security analysis, and protocol analysis.
With Wireshark Analysis, network analysts can capture network packets from various network interfaces, such as Ethernet, Wi-Fi, or USB, and analyze the captured packets to gain insights into the behavior of network protocols, applications, and devices. Wireshark supports a wide range of protocols, including Ethernet, IP, TCP, UDP, DNS, HTTP, FTP, SSL/TLS, VoIP, and many others, making it a versatile tool for analyzing different types of network traffic.
Wireshark provides a rich set of features for network analysis, including powerful filtering capabilities that allow analysts to capture specific types of packets or extract specific information from captured packets. It also offers advanced packet decoding and analysis, allowing analysts to dissect and interpret the contents of network packets, including headers, payloads, and other protocol-specific data.
Wireshark Analysis also includes various statistics and graphical tools for visualizing network traffic, such as protocol distribution charts, flow graphs, and time-based statistics, which can help analysts identify patterns, anomalies, and performance issues in network traffic.
Furthermore, Wireshark Analysis offers powerful features for security analysis, including the ability to detect and analyze potential security threats, such as malware, ransomware, and other cyber attacks, by inspecting packet payloads, analyzing patterns of network behavior, and detecting suspicious activities.
Wireshark Analysis is widely used by network administrators, security analysts, and developers to troubleshoot network issues, optimize network performance, diagnose protocol errors, investigate security incidents, and develop or test network applications. It provides a comprehensive set of tools and functionalities for capturing, analyzing, and interpreting network traffic, making it an invaluable tool in the arsenal of network professionals for understanding and managing complex networks.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 1:02:08
1:02:08
BonginoReport
4 hours agoNicki Minaj Speaks Out Against Christian Persecution - Nightly Scroll w/ Hayley Caronia (Ep.169)
37.7K23 -
 LIVE
LIVE
SpartakusLIVE
4 hours agoSNIPING in Battlefield 6 - REDSEC || Monday MOTIVATION to CONQUER the Week
143 watching -
 LIVE
LIVE
Nerdrotic
2 hours ago $2.05 earnedNerdrotic At Night 531
280 watching -
 LIVE
LIVE
The Jimmy Dore Show
3 hours agoTrump Threatens to INVADE Nigeria! Kash Patel CRASHES OUT Over Jet Use Criticism!
7,469 watching -
 LIVE
LIVE
Conductor_Jackson
22 hours agoLet's Play Unrailed 2 Solo! 🚂🚂🚂🚂🚂🚂
11 watching -
 1:25:38
1:25:38
Kim Iversen
4 hours agoTrump’s Nigeria Threat Isn’t About Christians — It’s About China
81.7K84 -
 6:15:23
6:15:23
VikingNilsen
7 hours ago🔴LIVE - ARC RAIDERS - QUEST GRINDING
2.45K -
 59:10
59:10
Sean Unpaved
3 hours agoDodgers Dynasty Rolls On, NFL Chaos Reigns, & MNF Showdown Countdown
16.8K1 -
 1:35:56
1:35:56
Redacted News
5 hours agoA MAGA Civil War has just begun, Christians slaughtered in Nigeria, Charlie Kirk's audiit | Redacted
122K179 -
 26:34
26:34
Stephen Gardner
5 hours ago🔥Elon EXPOSES The Exact Blueprint Dems use to CHEAT on Joe Rogan!!
47.3K104