Premium Only Content
Chapter-35, LEC-5 | Getting MAC Address | #rumble #ethicalhacking #hacking #porthacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
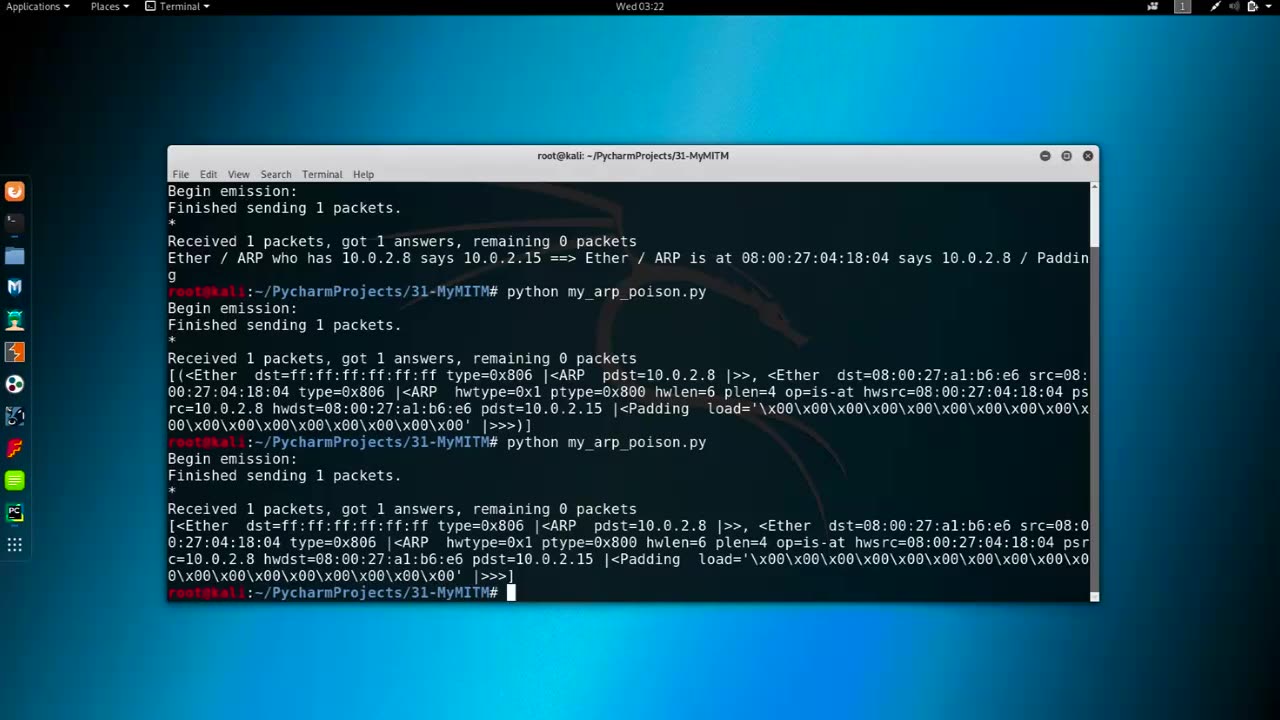
Getting MAC Address refers to the process of obtaining the Media Access Control (MAC) address of a network interface card (NIC) or a network-connected device. The MAC address, also known as the hardware address or physical address, is a unique identifier assigned to the NIC or network interface of a device at the factory, and it is used to uniquely identify a device within a network.
There are several methods to obtain the MAC address of a device:
Command-Line Interface (CLI): Many operating systems, such as Windows, macOS, Linux, and networking devices, provide command-line interfaces (CLI) that allow users to retrieve the MAC address using commands like "ipconfig" (Windows), "ifconfig" (macOS and Linux), or "show interfaces" (networking devices).
Graphical User Interface (GUI): Some operating systems, such as Windows and macOS, provide graphical user interfaces (GUI) that display the MAC address in the network settings or device properties.
Network Configuration or Management Tools: Network configuration or management tools, such as network monitoring software, network scanners, or network inventory tools, may have features to automatically detect and retrieve MAC addresses of devices within a network.
Physical Inspection: On some devices, the MAC address may be printed on a label or engraved on the NIC or device itself, making it possible to physically inspect the device to obtain its MAC address.
Network Protocol: Some network protocols, such as the Address Resolution Protocol (ARP) or the Dynamic Host Configuration Protocol (DHCP), may provide information about MAC addresses during network communication or device registration.
Obtaining MAC addresses can be useful for various networking tasks, such as troubleshooting, network monitoring, network access control, or device identification. However, it's important to note that MAC addresses can be easily spoofed or manipulated, and they should not be solely relied upon for device authentication or security purposes. Other security measures, such as encryption, authentication protocols, and access controls, should also be implemented to secure network communications and protect against unauthorized access.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 LIVE
LIVE
Dr Disrespect
5 hours ago🔴LIVE - DR DISRESPECT - TRIPLE THREAT CHALLENGE - RIVALS, PUBG, WARZONE
4,341 watching -
 18:52
18:52
VSiNLive
18 days agoFrom Las Vegas Dealer to Professional Gambler: How "Miss Brown" Won MILLIONS While Card Counting
20.2K2 -
 35:03
35:03
Stephen Gardner
1 hour ago🔥JUST NOW: Trump JUST SHOCKED Congress with new DEMAND!!
26.4K16 -
 LIVE
LIVE
checkmate7_7
3 hours ago $0.32 earnedStarting over. | !GUILDED
85 watching -
 LIVE
LIVE
Film Threat
7 hours agoVERSUS: BEST & WORST OF 2024! SQUID GAME SEASON 2! JANUARY SUCKS! | Film Threat Versus
131 watching -
 18:14
18:14
Neil McCoy-Ward
10 hours agoThis Is Absolutely Outrageous!!! (The UK Gov Have Betrayed Their Citizens...)
5.11K10 -
 1:56:15
1:56:15
The Officer Tatum
3 hours agoLIVE: Trudeau Resigns, Interview w Former DNC Fundraiser Lindy Li + MORE | Officer Tatum Show EP 35
21.3K6 -
 1:51:31
1:51:31
The Quartering
5 hours agoTrump HUMILIATED Trudeau Into QUITTING, Cybertruck Bomber Story Gets Weird, X Censorship & More
105K28 -
 1:43:39
1:43:39
Tucker Carlson
3 hours agoBilly Bush: The Infamous Trump Tape, Secrets of Corporate Media, & Megyn Kelly v. Harvey Weinstein
136K55 -
 2:08:29
2:08:29
Nerdrotic
5 hours ago $5.86 earnedHappy January 6th | FNT Square Up - Nerdrotic Nooner 455
78.3K10