Premium Only Content
Chapter-34, LEC-8 | Python3 Compatibility | #rumble #ethicalhacking #education #hacking
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
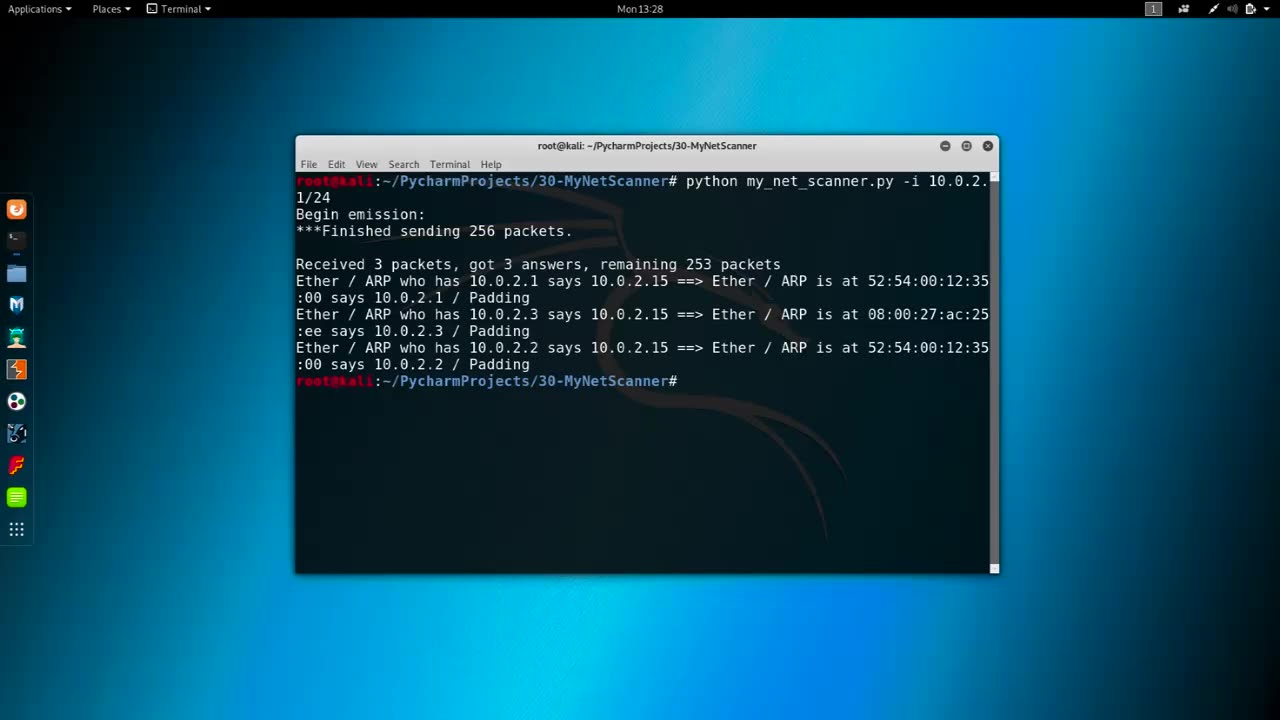
Python3 compatibility in the context of network scanning. With the evolution of Python programming language and the increasing popularity of Python3, it is essential for ethical hackers to ensure that their network scanner is compatible with Python3 to stay up-to-date with the latest advancements in the field.
The lecture begins with an overview of the importance of Python3 compatibility in network scanning. The instructor explains the differences between Python2 and Python3 and highlights the advantages of using Python3 for network scanning, such as improved performance, enhanced security, and support for modern features and libraries.
Next, the lecture delves into the process of making a network scanner compatible with Python3. Students learn about the key differences and potential issues when transitioning from Python2 to Python3, such as changes in syntax, string handling, and module names. The instructor provides practical guidance on how to update and modify the existing code of a network scanner to ensure it is compatible with Python3, including updating print statements, using the correct encoding, and addressing deprecated functions and modules.
Furthermore, the lecture covers best practices for developing network scanners with Python3 compatibility in mind. Students learn about using modern Python3 features, leveraging third-party libraries that are compatible with Python3, and following coding conventions and standards to write clean, efficient, and secure code.
Throughout the lecture, practical demonstrations and examples are provided to illustrate the concepts and techniques being taught. Students are encouraged to actively participate in hands-on exercises to gain practical experience in updating and modifying a network scanner for Python3 compatibility.
In summary, Lecture 7 of Chapter 34 in the Ethical Hacking Course focuses on ensuring Python3 compatibility in network scanning. The lecture highlights the importance of staying up-to-date with Python3 advancements, provides practical guidance on updating and modifying existing code for Python3 compatibility, and emphasizes best practices for developing network scanners with Python3. By mastering Python3 compatibility, ethical hackers can ensure that their network scanners are effective, efficient, and future-proof.
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
-
 39:51
39:51
Tucker Carlson
3 hours agoGeorge Galloway Speaks Out on Being Forced Into Exile After Criticizing Ukraine War
27.8K90 -
 21:23
21:23
Neil McCoy-Ward
2 hours ago🔥 While You're Working Hard... They're Planning To Take EVERYTHING From You!!!
6.15K2 -
 2:13:37
2:13:37
Side Scrollers Podcast
5 hours agoTwitch CONTROVERSY Hit New Low + Reddit Mods QUIT + FireMAN is Now Sexist + More | Side Scrollers
66K6 -
 5:31
5:31
John Rich Official
13 days agoThe Righteous Hunter by John Rich
23.4K11 -
 59:51
59:51
Rebel News
3 hours agoEby threatens to block pipeline, Guilbeault out of cabinet, Land disputes continue | Rebel Roundup
24.7K4 -
 1:45:59
1:45:59
Robert Gouveia
5 hours agoAmerican Soldier DEAD! Trump Furious! Afghan 'Vetted by CIA'! Third World FREEZE!
48.9K39 -
 48:48
48:48
The Culture War with Tim Pool
5 hours agoThe West Is COLLAPSING Under Mass Migration | The Culture War's Across The Pond
35.7K68 -
 1:42:33
1:42:33
The Mel K Show
5 hours agoMORNINGS WITH MEL K - We Have Not Yet Begun to Fight - The Clock is Ticking! 11-28-25
29.3K16 -
 1:25:54
1:25:54
Film Threat
17 hours agoHOLLYWOOD FOR SALE! BLACK FRIDAY BLOW OUT! | Film Threat Livecast
17.4K2 -
 2:51:52
2:51:52
The Shannon Joy Show
5 hours agoSJ Show Nov 28 - The SJ Friday Matinee Watch Party With Commentary Featuring The Big Short!
16.8K