Premium Only Content
PART 2 - How to Steal an Election | Election Theft 2020
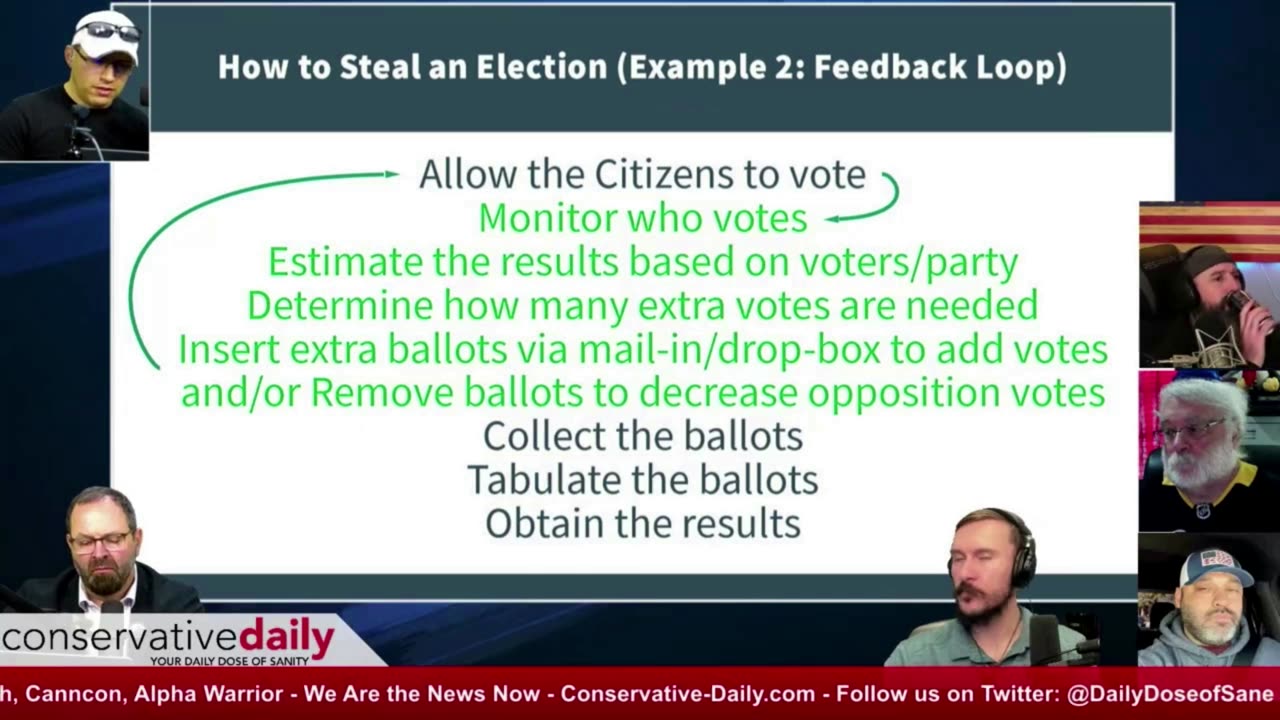
Watching Part 1 of How to Steal an Election is required before viewing Part 2 in order to understand the context of Part 2. Is election theft possible? Yes. The video goes back to a 2004 congressional testimony from Clint Curtis - a programmer who wrote an algorithm and code to steal an election on behalf of Republican Tom Feeny in Florida. From that point, programmers have had more than 20 years to improve, hide, and master the code required to manipulate the voting machines commonly used in elections today. Here, A panel of professional Software and IT Guys discuss how the 2020 Election was stolen. In this video, you'll see how using simple batch files (invisible commands to the computer that are executed automatically) from a simple flash drive to the Microsoft SQL Database Server can switch election results in less than 1 minute. MS SQL Server is found on every voting machine - put there by every voting machine manufacturer. Additionally, every Dell motherboard in the voting machines contains a wireless modem (enabling remote communications) with additional communication ports built into the board - ordered by Dominion Voting Systems (and other manufacturers). The video describes the accessibility vulnerabilities of Dominion's (and most company) Voting Machine Equipment and how they can be exploited by bad actors and even honest people with little to no knowledge that they are participating in the election theft. Part 2 of the video drills deeply into the election attack plans already being implemented and concludes with the notion that there is no fix to the election machine problem - all machines must go. However, the panel presents an outstanding way to conduct elections without the use of any election equipment that should be implemented by every county in the USA as a matter of course. The video is a must-see for every election official and informed American citizen.
-

FreshandFit
3 hours agoPodcaster "Rich And Unemployed" In Jail For $10M Fraud Bust!
12K2 -
 LIVE
LIVE
The HotSeat
1 hour agoThey’re Drowning the Truth: Texas Tragedy, Epstein Lies, and the Left’s Sick Celebration
1,017 watching -
 LIVE
LIVE
Film Threat
4 hours agoVERSUS: JURASSIC WORLD: REFUND | Film Threat Versus
182 watching -
 10:33
10:33
BlackBeltBarrister
4 hours ago $0.84 earnedIs This Ridiculous Yet?
12K4 -
 1:06:07
1:06:07
MTNTOUGH Podcast w/ Dustin Diefenderfer
6 hours agoPedro Ampuero: Stop Making Excuses and Start Exploring | MTNPOD #123
6.79K1 -
 1:51:10
1:51:10
The Quartering
4 hours agoTime To FIRE Pam Bondi , Texas Floods, Active Shooter At Border Patrol & More
106K51 -
 1:35:22
1:35:22
Russell Brand
5 hours agoSHOCK REPORT: DOJ, FBI Review Finds NO Jeffrey Epstein 'Client List,' Confirms Suicide - SF609
157K50 -
 LIVE
LIVE
RalliedLIVE
3 hours ago $0.86 earnedSHOTTY BOYS vs THE WORLD - WARZONE CHALLENGES
86 watching -
 1:05:27
1:05:27
Jeff Ahern
2 hours ago $0.48 earnedMonday Madness with Jeff Ahern
15.1K3 -
 45:34
45:34
SportsPicks
6 hours agoCrick's Corner: Episode 44
13.7K1