Premium Only Content
Chapter-31, LEC-5 | Inheritance | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy #porthacking#porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
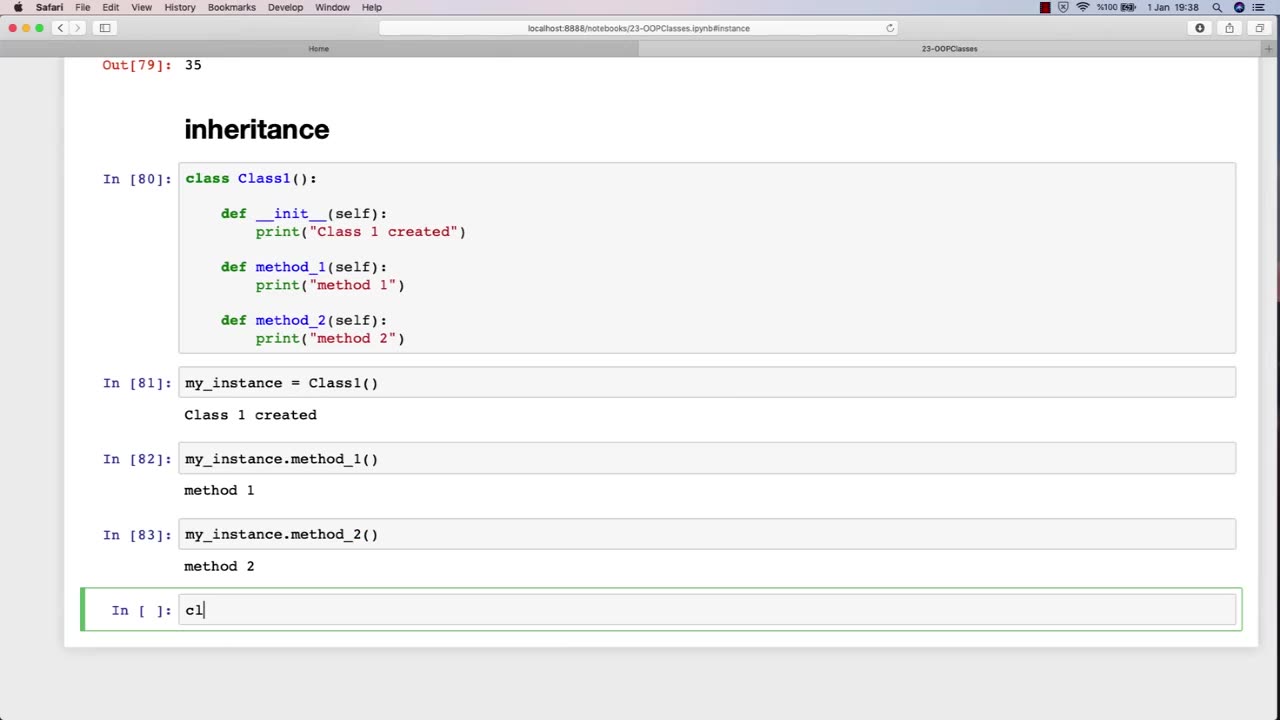
Inheritance is an important concept in object-oriented programming, and it can also be relevant to an ethical hacking course. In the context of ethical hacking, inheritance can refer to the use of pre-existing code or tools to aid in the hacking process.
For example, ethical hackers may inherit code or tools from previous projects, open-source software, or online resources. This code or tools may help them automate tasks, test for vulnerabilities, or exploit known weaknesses. By inheriting code or tools, ethical hackers can save time and effort, while also benefiting from the knowledge and expertise of other developers.
However, it is important for ethical hackers to be aware of the potential risks and limitations of inheriting code or tools. Inherited code may contain bugs or vulnerabilities that could introduce new security risks, and inherited tools may not be well-suited to the specific context of the hacking project. Therefore, ethical hackers must exercise caution when using inherited code or tools, and should always verify their functionality and security before incorporating them into their own work.
Furthermore, ethical hackers must also consider the ethical implications of inheriting code or tools. They must ensure that the code or tools they use are legally obtained and do not infringe on intellectual property rights or other legal obligations. They must also be mindful of the potential impact of their actions, and ensure that they are using their skills and tools for ethical purposes.
In summary, inheritance is an important concept in ethical hacking, as it allows hackers to leverage pre-existing code or tools to aid in their work. However, ethical hackers must be aware of the potential risks and limitations of inherited code or tools, and must also consider the ethical implications of their actions.
-
 35:27
35:27
megimu32
5 hours agoMEGI + PEPPY LIVE FROM DREAMHACK!
131K14 -
 1:03:23
1:03:23
Tactical Advisor
9 hours agoNew Gun Unboxing | Vault Room Live Stream 044
198K31 -
 19:12
19:12
Robbi On The Record
10 hours ago $16.92 earnedThe Loneliness Epidemic: AN INVESTIGATION
41.3K77 -
 14:45
14:45
Mrgunsngear
1 day ago $98.73 earnedFletcher Rifle Works Texas Flood 30 Caliber 3D Printed Titanium Suppressor Test & Review
81.6K21 -
 17:17
17:17
Lady Decade
1 day ago $6.12 earnedMortal Kombat Legacy Kollection is Causing Outrage
47K9 -
 35:51
35:51
Athlete & Artist Show
1 day ago $11.13 earnedIs Ryan Smith The Best Owner In The NHL?
65.3K6 -
 22:56
22:56
American Thought Leaders
2 days agoCharles Murray: I Thought Religion Was Irrelevant to Me. I Was Wrong.
57.6K30 -
 36:22
36:22
Brad Owen Poker
11 hours agoGIGANTIC $17,000+ Pot In BOBBY’S ROOM! TRAPPING Top Pro w/FULL HOUSE!! Big Win! Poker Vlog Ep 326
66K3 -
 3:53
3:53
GreenMan Studio
1 day agoRUMBLE RUNDOWN: DREAM HACK SPECIAL W/Greenman Reports
54.8K10 -
 1:28
1:28
Damon Imani
2 days agoThey Laughed at Trump’s Cognitive Test — Damon Made Them REGRET It!
54.2K37