Premium Only Content
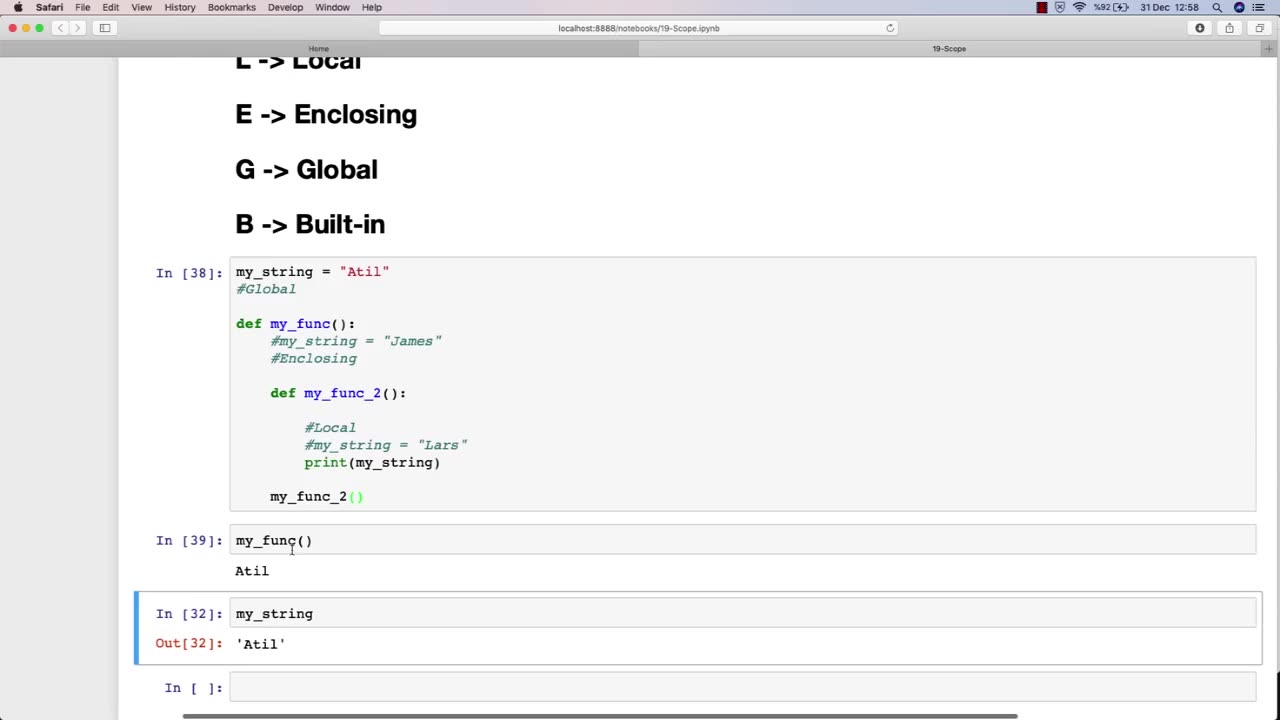
Chapter-30, LEC-6 | SCOPE | #ethicalhacking #education #hacking #rumble
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy
The scope of an ethical hacking course is vast and covers a wide range of topics related to cybersecurity and information security. At a high level, the scope of an ethical hacking course typically includes:
Understanding the fundamentals of cybersecurity: This includes understanding the various types of cybersecurity threats, such as viruses, malware, and phishing attacks, and the principles of risk management and threat modeling.
Network security: This includes understanding the fundamentals of network architecture and protocols, as well as how to secure networks against attacks such as denial-of-service (DoS) attacks and man-in-the-middle (MITM) attacks.
Web application security: This includes understanding the principles of web application architecture and how to secure web applications against common attacks such as cross-site scripting (XSS) and SQL injection.
Wireless security: This includes understanding the fundamentals of wireless networks and how to secure them against attacks such as rogue access points and eavesdropping.
Penetration testing: This includes understanding the principles of penetration testing and how to conduct effective ethical hacking activities, including reconnaissance, vulnerability assessment, and exploitation.
Ethical and legal considerations: This includes understanding the ethical and legal considerations associated with ethical hacking, such as obtaining permission and respecting privacy.
The scope of an ethical hacking course is constantly evolving to keep pace with the ever-changing cybersecurity landscape. As new threats emerge and new technologies are developed, the scope of an ethical hacking course must adapt to provide students with the latest knowledge and techniques in the field of cybersecurity.
-
 5:31
5:31
John Rich Official
12 days agoThe Righteous Hunter by John Rich
1.05K2 -
 48:48
48:48
The Culture War with Tim Pool
1 hour agoThe West Is COLLAPSING Under Mass Migration | The Culture War's Across The Pond
1.8K17 -
 LIVE
LIVE
The Mel K Show
58 minutes agoMORNINGS WITH MEL K - We Have Not Yet Begun to Fight - The Clock is Ticking! 11-28-25
461 watching -
 LIVE
LIVE
Film Threat
13 hours agoHOLLYWOOD FOR SALE! BLACK FRIDAY BLOW OUT! | Film Threat Livecast
66 watching -
 UPCOMING
UPCOMING
The Shannon Joy Show
1 hour agoSJ Show Nov 28 - The SJ Friday Matinee Watch Party With Commentary Featuring The Big Short!
54 -
 LIVE
LIVE
Grant Stinchfield
3 hours agoThe Medical Deep State Exposed — And McCullough Has the Receipts!
122 watching -
 LIVE
LIVE
Trumpet Daily
36 minutes agoTrumpet Daily LIVE | Nov. 28, 2025
326 watching -
 LIVE
LIVE
LFA TV
14 hours agoLIVE & BREAKING NEWS! | FRIDAY 11/28/25
7,751 watching -
 2:00:18
2:00:18
Badlands Media
10 hours agoBadlands Daily – Nov. 28, 2025
76.1K12 -
 2:18:44
2:18:44
Nikko Ortiz
2 hours agoVR Ghost Of Tabor... | Rumble LIVE
4.55K2