Premium Only Content
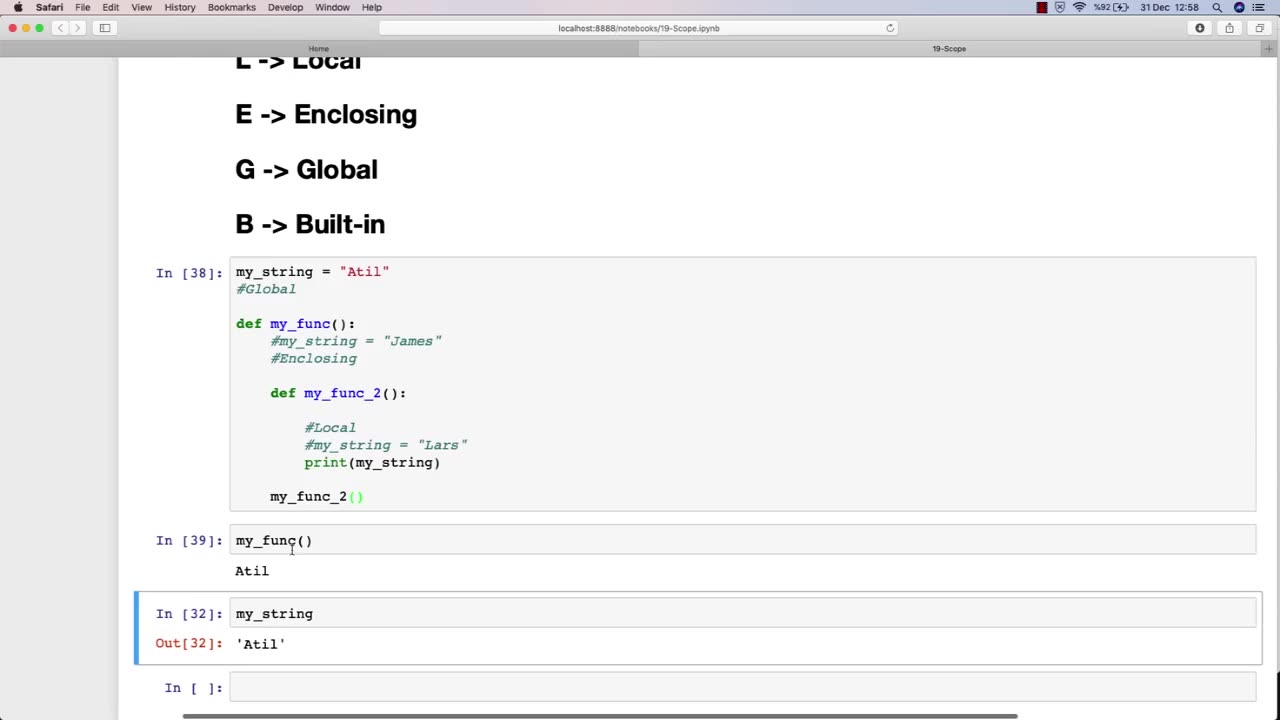
Chapter-30, LEC-6 | SCOPE | #ethicalhacking #education #hacking #rumble
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy
The scope of an ethical hacking course is vast and covers a wide range of topics related to cybersecurity and information security. At a high level, the scope of an ethical hacking course typically includes:
Understanding the fundamentals of cybersecurity: This includes understanding the various types of cybersecurity threats, such as viruses, malware, and phishing attacks, and the principles of risk management and threat modeling.
Network security: This includes understanding the fundamentals of network architecture and protocols, as well as how to secure networks against attacks such as denial-of-service (DoS) attacks and man-in-the-middle (MITM) attacks.
Web application security: This includes understanding the principles of web application architecture and how to secure web applications against common attacks such as cross-site scripting (XSS) and SQL injection.
Wireless security: This includes understanding the fundamentals of wireless networks and how to secure them against attacks such as rogue access points and eavesdropping.
Penetration testing: This includes understanding the principles of penetration testing and how to conduct effective ethical hacking activities, including reconnaissance, vulnerability assessment, and exploitation.
Ethical and legal considerations: This includes understanding the ethical and legal considerations associated with ethical hacking, such as obtaining permission and respecting privacy.
The scope of an ethical hacking course is constantly evolving to keep pace with the ever-changing cybersecurity landscape. As new threats emerge and new technologies are developed, the scope of an ethical hacking course must adapt to provide students with the latest knowledge and techniques in the field of cybersecurity.
-
 21:39
21:39
Nikko Ortiz
2 days agoI Take A North Korean Shooting
4.26K3 -
 1:46:26
1:46:26
The Michelle Moore Show
16 hours ago'The Religion Invasion In the U.S. and the Deep State Agenda' Guest, Mark Taylor: The Michelle Moore Show (Nov 3, 2025)
13.3K19 -
 LIVE
LIVE
TruthStream with Joe and Scott
5 days agoSovereign Codes & Cosmic Infrastructure,Ufo's, UAP's, Monads, Matrix Satellites, Interstellar Visitors, SYRONA #505
166 watching -
 LIVE
LIVE
Lofi Girl
2 years agoSynthwave Radio 🌌 - beats to chill/game to
136 watching -
 5:55:11
5:55:11
MattMorseTV
9 hours ago $71.54 earned🔴Trump's '60 Minutes' INTERVIEW + MUCH MORE.🔴
147K38 -
 2:02:36
2:02:36
Badlands Media
13 hours agoBaseless Conspiracies Ep. 157: Jack the Ripper, the Crash & the Great Disclosure Countdown
28.4K18 -
 2:06:09
2:06:09
Inverted World Live
10 hours agoMysterious Crash at Area 51 | Ep. 134
31K13 -
 2:48:59
2:48:59
TimcastIRL
8 hours agoTrump Endorses Cuomo, Says NO COMMIE MAMDANI, Obama REFUSES To Endorse Mamdani | Timcast IRL
265K174 -
 5:51:16
5:51:16
Drew Hernandez
1 day agoGOP CIVIL WAR: TUCKER CARLSON DERANGEMENT SYNDROME AT ALL TIME HIGH
52.6K41 -
 14:44
14:44
Sponsored By Jesus Podcast
1 day agoYou Can't Serve God & MONEY | Is Money the Root of All Evil?
23.3K20