Premium Only Content
Chapter-30, LEC-3 | Functions Explained (lec-2) | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
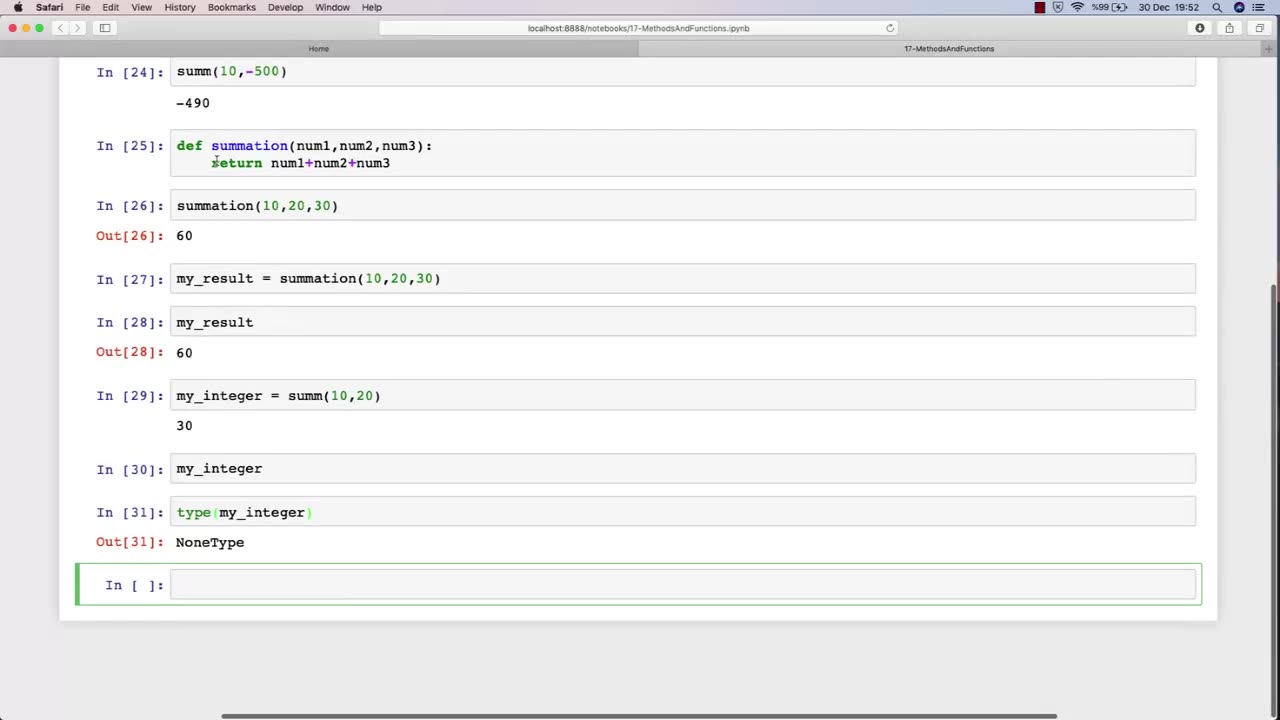
In Lecture 2 of an ethical hacking course, the function is to introduce students to the basic principles and concepts of ethical hacking. This lecture typically covers topics such as the difference between ethical hacking and illegal hacking, the various types of hackers, and the ethical and legal issues associated with ethical hacking.
The main objective of this lecture is to establish a foundational understanding of what ethical hacking is, why it is important, and the ethical and legal considerations that must be taken into account when conducting ethical hacking activities.
Students in this lecture learn about the various types of hackers, including black hat hackers, white hat hackers, and grey hat hackers. They learn about the motivations and characteristics of each type of hacker and how they differ in terms of their intentions and activities.
The lecture also covers the ethical considerations associated with ethical hacking, such as the importance of obtaining permission before conducting any testing, respecting the privacy of individuals and organizations, and adhering to ethical and professional standards.
Finally, the lecture covers the legal issues associated with ethical hacking, including the various laws and regulations governing cybersecurity and data protection, and the potential consequences of violating these laws.
Overall, the function of Lecture 2 in an ethical hacking course is to provide students with a broad understanding of the ethical and legal principles that underpin ethical hacking, and to ensure that they are equipped with the knowledge and skills necessary to conduct ethical hacking activities in a responsible and professional manner.
-
 LIVE
LIVE
Dr Disrespect
10 hours ago🔴LIVE - DR DISRESPECT - ARC RAIDERS - FULL SEND INTO THE RED
1,136 watching -
 1:02:08
1:02:08
BonginoReport
4 hours agoNicki Minaj Speaks Out Against Christian Persecution - Nightly Scroll w/ Hayley Caronia (Ep.169)
37.7K23 -
 LIVE
LIVE
SpartakusLIVE
4 hours agoSNIPING in Battlefield 6 - REDSEC || Monday MOTIVATION to CONQUER the Week
139 watching -
 LIVE
LIVE
Nerdrotic
2 hours ago $2.05 earnedNerdrotic At Night 531
278 watching -
 LIVE
LIVE
The Jimmy Dore Show
3 hours agoTrump Threatens to INVADE Nigeria! Kash Patel CRASHES OUT Over Jet Use Criticism!
7,488 watching -
 LIVE
LIVE
Conductor_Jackson
22 hours agoLet's Play Unrailed 2 Solo! 🚂🚂🚂🚂🚂🚂
10 watching -
 1:25:38
1:25:38
Kim Iversen
4 hours agoTrump’s Nigeria Threat Isn’t About Christians — It’s About China
81.7K84 -
 6:15:23
6:15:23
VikingNilsen
7 hours ago🔴LIVE - ARC RAIDERS - QUEST GRINDING
2.45K -
 59:10
59:10
Sean Unpaved
3 hours agoDodgers Dynasty Rolls On, NFL Chaos Reigns, & MNF Showdown Countdown
16.8K1 -
 1:35:56
1:35:56
Redacted News
5 hours agoA MAGA Civil War has just begun, Christians slaughtered in Nigeria, Charlie Kirk's audiit | Redacted
122K179