Premium Only Content
Chapter-30, LEC-3 | Functions Explained (lec-2) | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
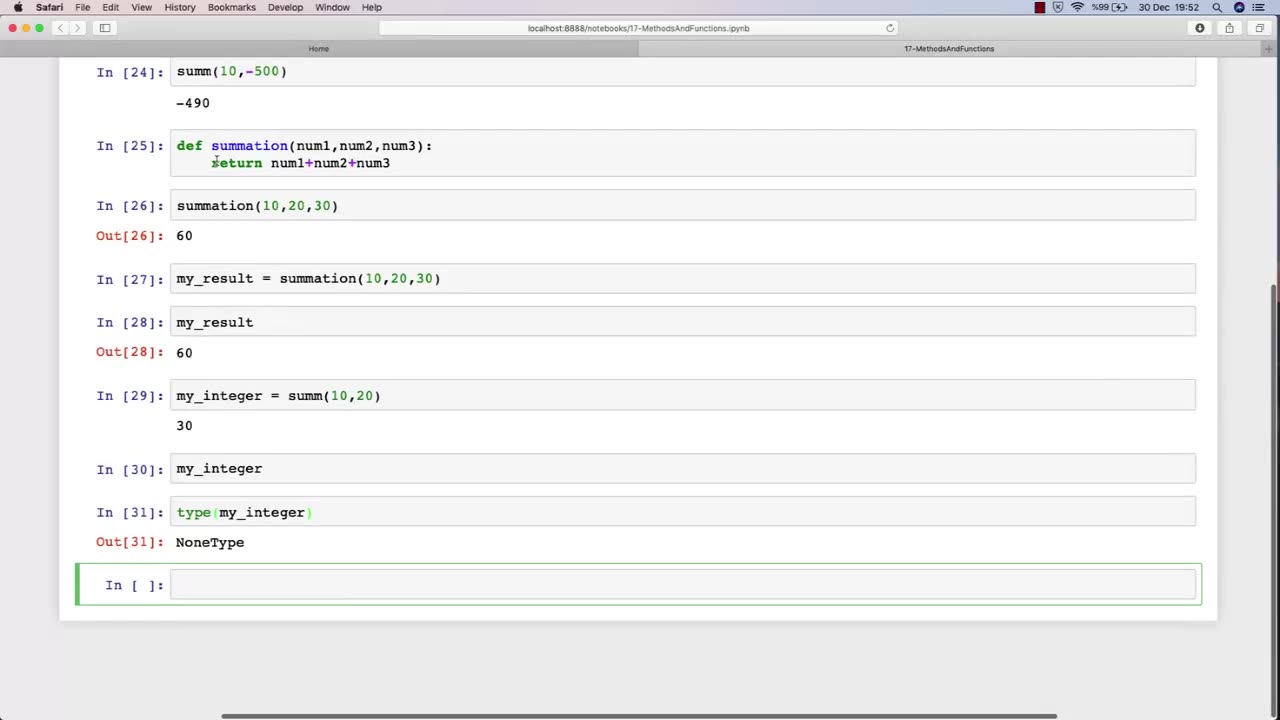
In Lecture 2 of an ethical hacking course, the function is to introduce students to the basic principles and concepts of ethical hacking. This lecture typically covers topics such as the difference between ethical hacking and illegal hacking, the various types of hackers, and the ethical and legal issues associated with ethical hacking.
The main objective of this lecture is to establish a foundational understanding of what ethical hacking is, why it is important, and the ethical and legal considerations that must be taken into account when conducting ethical hacking activities.
Students in this lecture learn about the various types of hackers, including black hat hackers, white hat hackers, and grey hat hackers. They learn about the motivations and characteristics of each type of hacker and how they differ in terms of their intentions and activities.
The lecture also covers the ethical considerations associated with ethical hacking, such as the importance of obtaining permission before conducting any testing, respecting the privacy of individuals and organizations, and adhering to ethical and professional standards.
Finally, the lecture covers the legal issues associated with ethical hacking, including the various laws and regulations governing cybersecurity and data protection, and the potential consequences of violating these laws.
Overall, the function of Lecture 2 in an ethical hacking course is to provide students with a broad understanding of the ethical and legal principles that underpin ethical hacking, and to ensure that they are equipped with the knowledge and skills necessary to conduct ethical hacking activities in a responsible and professional manner.
-
 1:05:56
1:05:56
vivafrei
2 hours agoComey Doubles Down, Prosecution Doubles Up! Election Day Madness! Boasberg Impeachment & MORE!
21.2K11 -
 LIVE
LIVE
SpartakusLIVE
1 hour agoNEW Meta = EPIC WINS on Battlefield 6 - REDSEC
167 watching -

StoneMountain64
5 hours agoBattlefield REDSEC leveling guns for attachments
29.6K1 -
 26:19
26:19
Liberty Hangout
4 days agoAnti-Trumpers Make Up Bizarre Theories
9.16K37 -
 LIVE
LIVE
GritsGG
5 hours agoWorld Record Win Streak Attempt! #1 Most Wins 3880+!
42 watching -
 LIVE
LIVE
The Rabble Wrangler
16 hours agoBattlefield with The Best in the West
47 watching -
 13:56
13:56
Cash Jordan
3 hours ago"OPEN BORDERS" Mob BATTERS Portland Jail… 'COMBAT' Marines DEFY Judge, BREAK BONES
4.92K8 -
 16:44
16:44
Russell Brand
4 hours agoAmerica’s Hidden Royalty
29.4K26 -
 LIVE
LIVE
LumpyPotatoX2
3 hours agoLightyear Frontier: Gameplay Showcase - Sponsored Stream
39 watching -
 DVR
DVR
ReAnimateHer
8 hours ago $0.13 earnedSurviving the Undead in Cold War Zombies
3853