Premium Only Content
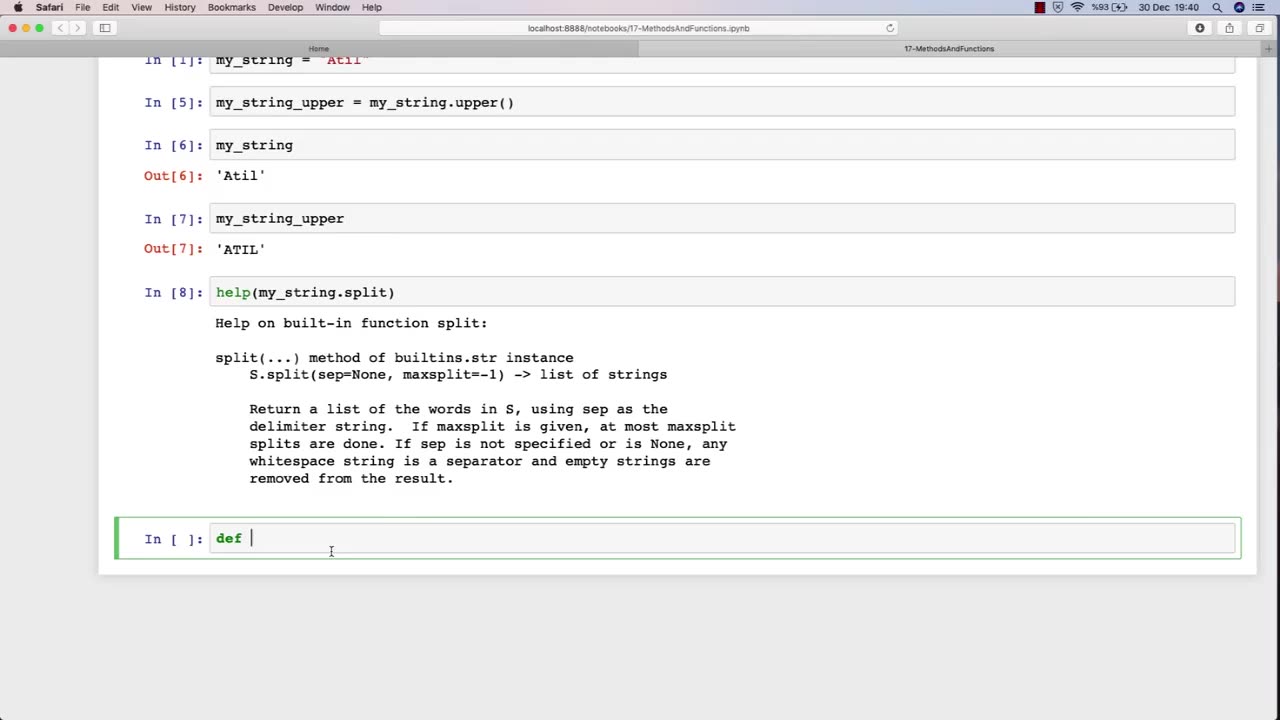
Chapter-30, LEC-2 | Functions Explained (lec-1) | #rumble #ethicalhacking #education
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools
#bushwhacking #hacking_or_secutiy
The function of an ethical hacking course is to equip individuals with the knowledge, skills, and techniques necessary to become a professional ethical hacker. Ethical hacking is a critical component of cybersecurity, as it involves identifying and addressing potential vulnerabilities in computer systems, networks, and applications before malicious actors can exploit them.
An ethical hacking course typically covers a range of topics related to cybersecurity, including penetration testing, vulnerability assessment, network security, web application security, social engineering, cryptography, and incident response. The course provides students with an understanding of various security threats and how to mitigate them through the use of specialized tools and techniques.
During an ethical hacking course, students learn how to perform vulnerability assessments, conduct penetration testing, and analyze system and network logs to identify potential security threats. They also learn how to use various tools, such as vulnerability scanners and network analyzers, to assess the security posture of a system or network. Additionally, students learn about common attack vectors and techniques, such as SQL injection and cross-site scripting, and how to defend against them.
Overall, the goal of an ethical hacking course is to train individuals to become skilled and responsible cybersecurity professionals who can help organizations protect themselves from cyber attacks. By learning how to identify vulnerabilities and mitigate security threats, students can help ensure the security and privacy of sensitive information and safeguard against potential data breaches.
-
 LIVE
LIVE
Nerdrotic
59 minutes agoNerdrotic At Night 531
510 watching -
 LIVE
LIVE
TheCrucible
33 minutes agoWATCH PARTY! Coach Greg Adams vs Andrew Wilson: Marriage in the West is Good For Men (11/03/25)
1,205 watching -
 LIVE
LIVE
The Jimmy Dore Show
1 hour agoTrump Threatens to INVADE Nigeria! Kash Patel CRASHES OUT Over Jet Use Criticism!
5,123 watching -
 1:25:38
1:25:38
Kim Iversen
3 hours agoTrump’s Nigeria Threat Isn’t About Christians — It’s About China
63.3K53 -
 59:10
59:10
Sean Unpaved
2 hours agoDodgers Dynasty Rolls On, NFL Chaos Reigns, & MNF Showdown Countdown
3.03K1 -
 1:35:56
1:35:56
Redacted News
3 hours agoA MAGA Civil War has just begun, Christians slaughtered in Nigeria, Charlie Kirk's audiit | Redacted
101K133 -
 LIVE
LIVE
Dr Disrespect
8 hours ago🔴LIVE - DR DISRESPECT - ARC RAIDERS - FULL SEND INTO THE RED
1,537 watching -
 26:34
26:34
Stephen Gardner
3 hours ago🔥Elon EXPOSES The Exact Blueprint Dems use to CHEAT on Joe Rogan!!
30.1K89 -
 51:10
51:10
Dad Saves America
7 hours ago $1.36 earnedMask Off Mamdani: NYC’s Socialist “Savior” Is Another Spoiled Aristocrat
14.8K5 -
 6:14
6:14
Buddy Brown
8 hours ago $2.56 earnedLaw Enforcement Caught SNOOPING on PRIVATE LAND! | Buddy Brown
15.2K24