Premium Only Content
Chapter-27, LEC-12 | Tuples | #ethicalhacking #hacking #education #growthhacking #biohacking
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools #bushwhacking #hacking_or_secutiy #porthacking #belajarhacking #hackinginstagram #growthacking #biohackingsecrets #realityhacking #neurohacking #hackingnews #funnelhacking #mindhacking #funnelhackinglive #hackinglife #termuxhacking #learnhacking #bodyhacking #patternhacking #biohackingsuccess #ikeahacking #hackingorsecurity #russianhacking #traumahacking #shackingup #hackinghealth #growthhackingtips #wifihacking
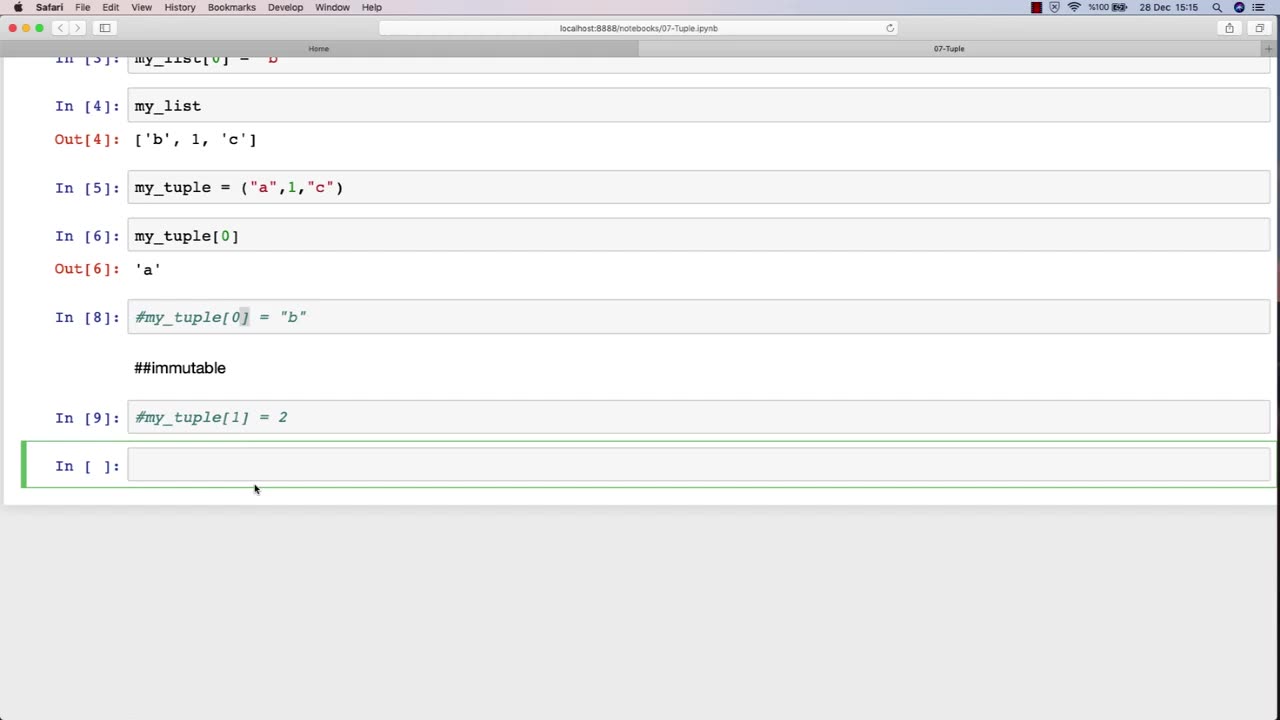
Tuple: "Types of Attacks"
Description: The types of attacks used in ethical hacking refer to the various methods and techniques that attackers use to compromise computer systems and networks. The following is a tuple of some of the common types of attacks that may be covered in an ethical hacking course:
Phishing attacks - A type of social engineering attack that tricks users into revealing sensitive information or performing harmful actions, such as clicking on a malicious link or downloading malware.
SQL injection attacks - A type of web application attack that exploits vulnerabilities in SQL database queries to gain unauthorized access to data.
Cross-site scripting (XSS) attacks - A type of web application attack that injects malicious scripts into a web page to steal user information or hijack user sessions.
Brute force attacks - A type of password guessing attack that tries all possible password combinations to gain unauthorized access to a system or network.
Denial of Service (DoS) attacks - A type of attack that floods a network or system with traffic to make it unavailable to legitimate users.
Man-in-the-middle (MitM) attacks - A type of attack that intercepts and modifies communication between two parties to steal sensitive information or perform malicious actions.
Session hijacking attacks - A type of attack that steals user session tokens to gain unauthorized access to a web application or system.
Ransomware attacks - A type of malware attack that encrypts files on a system and demands payment in exchange for the decryption key.
Advanced persistent threats (APTs) - A type of sophisticated and targeted attack that uses multiple techniques and tactics to compromise a system or network over a long period of time.
Insider attacks - A type of attack that is carried out by someone who has authorized access to a system or network, such as an employee or contractor.
By understanding the various types of attacks, ethical hackers can better identify and address security vulnerabilities in computer systems and networks. In an ethical hacking course, students learn how to use different tools and techniques to simulate these attacks in a controlled environment and develop effective strategies for preventing and mitigating them.
-
 LIVE
LIVE
LFA TV
11 hours agoLIVE & BREAKING NEWS! | TUESDAY 11/4/25
5,404 watching -
 LIVE
LIVE
The Bubba Army
23 hours agoIS FETTERMAN GOING REPUBLICAN? - Bubba the Love Sponge® Show | 11/04/25
2,709 watching -

BEK TV
1 day agoTrent Loos in the Morning - 11/04/2025
8.92K -
 21:38
21:38
Professor Nez
21 hours agoTrump JUST BROKE the INTERNET with SAVAGE Line on Ilhan Omar!
42.3K58 -
 1:17:52
1:17:52
Dialogue works
3 days ago $10.17 earnedMartin Armstrong: This Is How World War III Starts… And It Already Has
36.4K18 -
 38:16
38:16
daniellesmithab
3 days agoAlberta Update: Getting Kids Back to the Classroom
28.4K11 -
 20:48
20:48
BlaireWhite
5 days agoTrans TikTokers Are Crashing Out (Over Nothing)
32.6K11 -
 2:07:06
2:07:06
Side Scrollers Podcast
22 hours agoHasan Piker CAUGHT LYING AGAIN + Twitch URGES LEFTIST IDEOLOGY + More | Side Scrollers
74.8K11 -
 8:40
8:40
MattMorseTV
18 hours ago $14.34 earnedSchumer just KICKED OFF the Left-Wing CIVIL WAR.
35.8K34 -
 21:39
21:39
Nikko Ortiz
2 days agoI Take A North Korean Shooting
33.5K6