Premium Only Content
Chapter-27, LEC-2 | Numbers | #ethicalhacking #hacking #education #cybersport #cybersecurity
#ethicalhacking #hacking #rumble #virel #trending #education
Subscribe to our channel YouTube channel.❤️
/@thecybersecurityclassroom
Followe me on Rumble.💕
/@the1cybersequrityclassroom
#hacking #growthhacking #biohacking #ethicalhacking #lifehacking #whacking #hackingout #happyhacking #brainhacking #travelhacking #househacking #brainhackingum #hackingtools #bushwhacking #hacking_or_secutiy #porthacking #belajarhacking #hackinginstagram
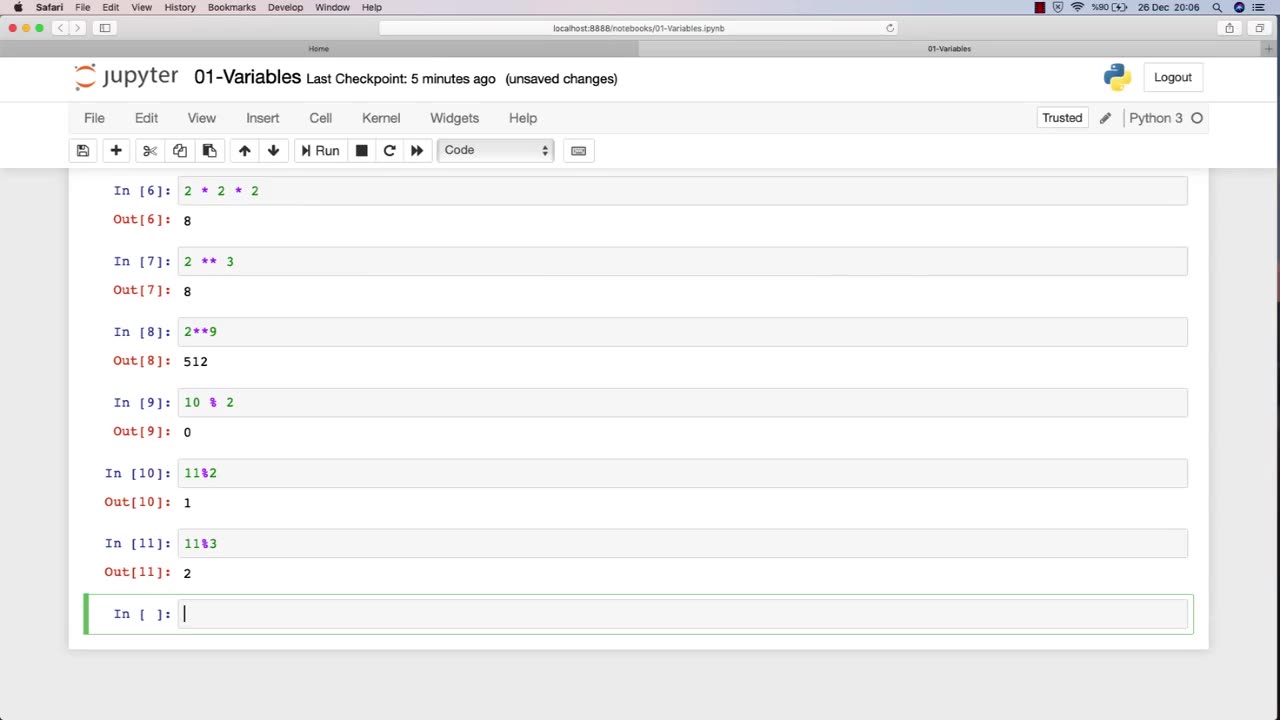
Ethical hacking is a field that involves the use of various techniques and tools to identify and address vulnerabilities in computer systems and networks. Numbers play a critical role in ethical hacking, and understanding how to work with numbers is essential for success in this field.
Here are some examples of how numbers are used in ethical hacking:
IP Addresses: IP addresses are used to identify network devices and are essential for ethical hackers to understand. Ethical hackers use IP addresses to scan for open ports, identify potential vulnerabilities, and carry out attacks.
Ports: Ports are used to establish connections between devices on a network. Ethical hackers use knowledge of port numbers to scan for vulnerabilities, carry out attacks, and test the security of a network.
Passwords: Passwords are often used to protect sensitive information in computer systems and networks. Ethical hackers use various techniques to crack passwords, such as brute-force attacks, dictionary attacks, and rainbow table attacks.
Encryption: Encryption is the process of converting data into a secure format that cannot be read by unauthorized parties. Ethical hackers use their understanding of encryption algorithms and techniques to identify vulnerabilities and weaknesses in encryption systems.
Binary and hexadecimal: Binary and hexadecimal are number systems used in computing. Ethical hackers use their understanding of these number systems to analyze and manipulate data at the low-level, such as reverse engineering software or discovering vulnerabilities in firmware.
Overall, a strong understanding of numbers is essential for success in ethical hacking. By understanding how numbers are used in this field, ethical hackers can more effectively identify and address vulnerabilities in computer systems and networks.
-
 LIVE
LIVE
Due Dissidence
8 hours agoLIVE: ELECTION RESULTS From NYC, NJ, and VA - Trump Approval CRATERS, Kash's Private Jet CRASH OUT
1,264 watching -
 12:50
12:50
Demons Row
1 hour agoBikers of New Jersey 💀🏍️ Pagans, Thunder Guards, and Thug Riders
7 -
 42:31
42:31
Stephen Gardner
4 hours ago🔥Old Obama Video RESURFACES - His Own Words CONDEMNED Him! Trump Gains MASSIVE Momentum!!
5.33K11 -
 LIVE
LIVE
LFA TV
23 hours agoLIVE & BREAKING NEWS! | TUESDAY 11/4/25
592 watching -
 1:03:37
1:03:37
BonginoReport
3 hours agoElection Night Showdown Spotlight - Nightly Scroll w/ Hayley Caronia (Ep.170)
82.8K20 -
 LIVE
LIVE
Edge of Wonder
3 hours agoSupernatural Forces & Giants Built Great Pyramid of Egypt
188 watching -
 1:24:03
1:24:03
Kim Iversen
4 hours agoAn Islamist Socialist in NYC? The Panic Is Epic | Neocons To Tucker: 'Love Israel OR ELSE'
72.1K93 -
 LIVE
LIVE
Tundra Tactical
3 hours agoProfessional Gun Nerd Plays Battlefield 6
71 watching -
 LIVE
LIVE
Quite Frankly
8 hours ago31/ATLAS to Enoch, Election Night Updates, Open Lines | Timothy Alberino 11/4/25
708 watching -
 1:05:56
1:05:56
vivafrei
3 hours agoComey Doubles Down, Prosecution Doubles Up! Election Day Madness! Boasberg Impeachment & MORE!
32.7K23